A sophisticated SnakeKeylogger campaign has emerged, leveraging socially engineered emails impersonating CPA Global and Clarivate to distribute malicious ISO and ZIP attachments.
Security researchers have identified multiple indicators suggesting that threat actors behind this operation are successfully exploiting user trust and native Windows scripting to deploy an information-stealing Trojan, SnakeKeylogger, which harvests keystrokes, browser credentials, and system fingerprints before exfiltrating data via PowerShell.
Infection Vector and Delivery Mechanism
The attack chain begins with an email seemingly sent from “CPA-Payment Files,” referencing a remittance advice dated October 7, 2025, to lend authenticity. Recipients are urged to open an attached ISO or ZIP archive.
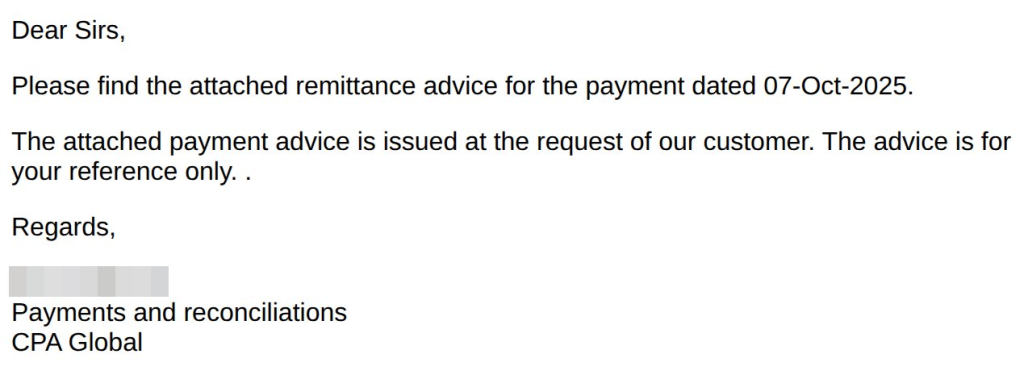
Once extracted, the archive contains a malicious BAT script named “PaymentAdvice.bat.” This script invokes a PowerShell command that downloads a secondary payload from a remote server over HTTPS.
Deceptively obfuscated, the BAT file includes variables that resolve to the PowerShell download URL.
Upon execution, the PowerShell script establishes persistence by creating a registry key under HKCU\Software\Microsoft\Windows\CurrentVersion\Run. Then, stage the SnakeKeylogger binary from an embedded Base64 string.
Once installed, SnakeKeylogger injects itself into standard processes explorer.exe to evade detection. The malware captures keystrokes across active windows and periodically gathers system data, including Windows version, installed antivirus products, and running processes.
It also scans web browsers for saved credentials and cookies. Captured data is encrypted using AES-256 in GCM mode, with the encryption key derived from the victim’s machine GUID and a hardcoded salt.
Communication and Exfiltration
SnakeKeylogger communicates with its command-and-control (C2) server over HTTP POST requests, disguised as legitimate telemetry calls. The exfiltration routine packages encrypted logs into JSON payloads and sends them to a PHP endpoint on the attacker-controlled domain.
Timing mechanisms randomize the intervals between exfiltration attempts to blend into regular network traffic. If the C2 endpoint is unreachable, the malware queues logs locally and retries every 30 minutes.
Network defenders should implement strict email filtering rules to block ISO and ZIP attachments or flag emails impersonating known vendors. Execution policies for PowerShell should be set to RemoteSigned, and script block logging should be enabled.
Endpoint protection platforms capable of monitoring command-line and registry modifications can detect abnormal persistence behaviors. Rapid identification of anomalous HTTP POST requests to non-corporate domains can further thwart data exfiltration.
This SnakeKeylogger campaign underscores the continued evolution of infostealer threats that blend social engineering with native scripting. Organizations must maintain layered defenses, from robust email security to stringent endpoint monitoring, to defend against such weaponized email campaigns.
IoCs:
- 1bf2e282e0b58814838af57c8792b6147eacedb3f954821b8eea3b79e1f77cb3 (ZIP in mail attachment)
- fb17cc142e92edd5c683c3d53ff8e15f73c67b65df116827f92c9f81c672ec26 (ISO in mail attachment)
- 929fc6575e8ca6b7a657c784254693c4a343e0576bc64a8ba42eac5003796e68 (BAT downloader)
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates