ClayRat, a rapidly evolving Android spyware campaign, has surged in activity over the past three months, with zLabs researchers documenting more than 600 unique samples and 50 droppers.
Primarily targeting Russian-speaking users, ClayRat leverages a sophisticated blend of social engineering, phishing sites, and malicious Telegram channels to trick victims into installing rogue APKs disguised as legitimate applications such as WhatsApp, Google Photos, TikTok, and YouTube.
Deceptive Distribution Tactics
Threat actors behind ClayRat register look-alike domains that mimic official service pages like GdeDPS and deploy them as landing pages, directing visitors to Telegram channels. On these channels, staged comments and inflated download counts provide social proof to reduce suspicion.
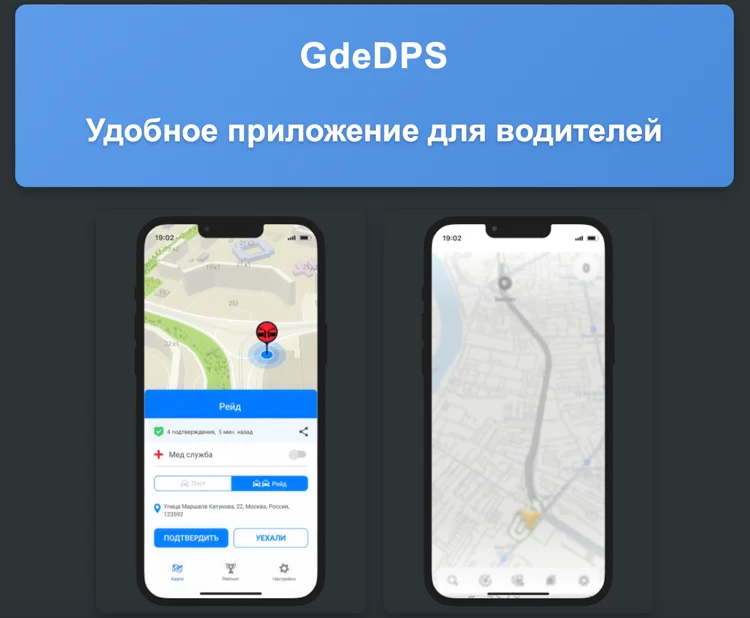
Victims are instructed to bypass Android’s security warnings, sideload the malicious APK, and grant the app the default SMS handler role.
Several samples act as droppers, displaying a fake Google Play update interface and guiding users through a “session-style” installation flow that emulates Android 13+ update screens to lower perceived risk.
Phishing sites impersonating “YouTube Plus” or other popular apps host APKs disguised as legitimate updates, complete with step-by-step installation instructions that urge users to enable installations from unknown sources.
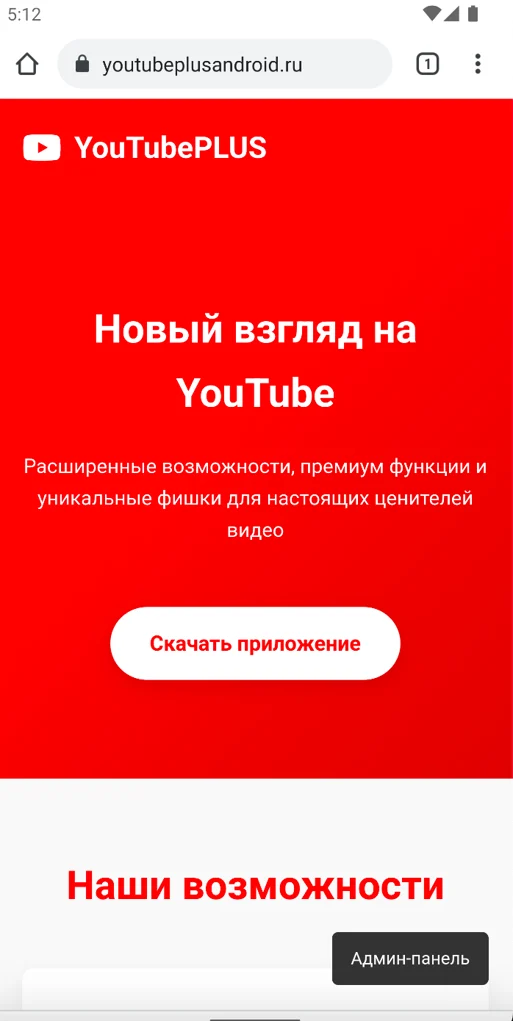
New ClayRat iterations employ increasingly sophisticated obfuscation and packing techniques, dynamically loading encrypted payloads from within the app’s assets.
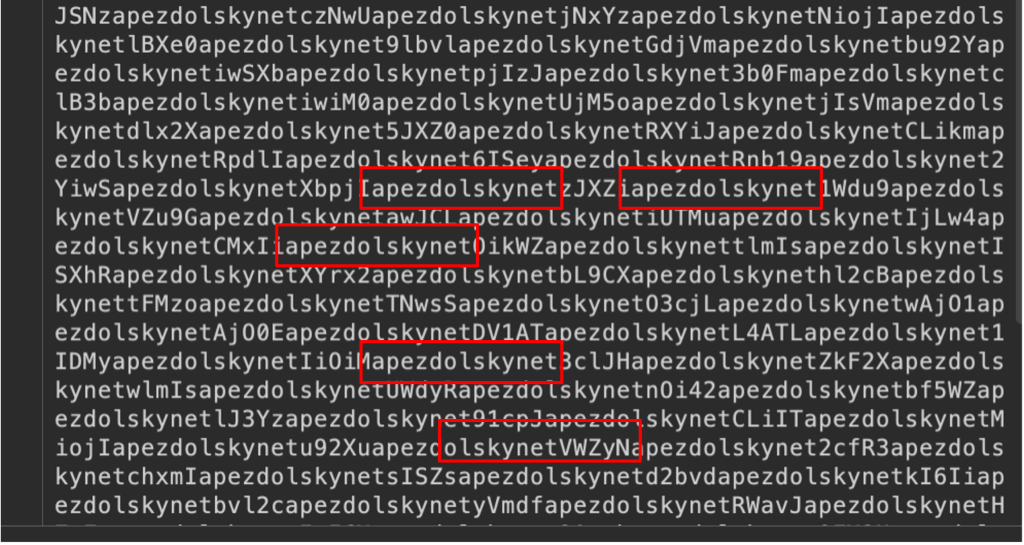
Early variants inserted the marker string “apezdolskynet” into Base64-encoded HTTP requests to its command-and-control (C2) infrastructure, while later versions adopted AES-GCM encryption for C2 communications.
This tightly coupled packing and dynamic loading approach thwarts static analysis and signature-based detection, allowing each sample to evade conventional defenses.
ClayRat’s operators continue to refine their code, ensuring each new dropper and payload iteration remains covert and difficult to analyze.
Comprehensive Surveillance and Self-Propagation
Once granted the default SMS handler role, ClayRat gains broad access to SMS content and messaging functions without triggering individual runtime prompts. Upon activation, it harvests SMS messages, call logs, notifications, and device information, then exfiltrates this data to its C2 server.
It can capture front-camera photographs, initiate outbound SMS messages, and make calls directly from the compromised device.
A core component of ClayRat’s design is its self-propagation capability: the spyware iterates through the victim’s contact list and sends socially engineered messages “Узнай первым! <link>” to every contact.
These messages, appearing to originate from a trusted source, lure new victims into the same infection chain or malicious Telegram channels.
The malware’s command set includes operations such as get_sms_list, get_calls, get_camera, make_call, send_sms, and notifications management, all invoked via simple HTTP POST requests.
Upon receiving a get_proxy_data command, ClayRat can transition its communication channel from HTTP to WebSocket, enhancing persistence and evading network-level filters.
Zimperium’s Mobile Threat Defense (MTD) and zDefend solutions have proactively detected ClayRat’s packed variants and droppers from their earliest iterations.
Leveraging behavioral machine learning models, zLabs researchers flagged and quarantined malicious APKs before public disclosures or signature updates were available.
As ClayRat continues to expand, security teams should monitor SMS handler role requests closely and educate users on the dangers of sideloading applications from unverified sources.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates