Socket’s Threat Research Team has uncovered a sophisticated phishing campaign dubbed “Beamglea” that exploited 175 malicious npm packages to target over 135 industrial, technology, and energy companies worldwide.
The malicious packages accumulated more than 26,000 downloads collectively, serving as infrastructure for widespread credential harvesting attacks against major corporations across multiple sectors.
The campaign leveraged npm’s public registry and unpkg.com’s content delivery network to host redirect scripts that funnel victims to credential harvesting pages. Unlike traditional supply chain attacks, these packages don’t execute malicious code when installed via npm.
Instead, threat actors abuse npm as free hosting infrastructure for phishing attacks, exploiting unpkg.com’s automatic HTTPS serving of public packages without paying for servers or SSL certificates.
Automated Package Generation and Distribution Strategy
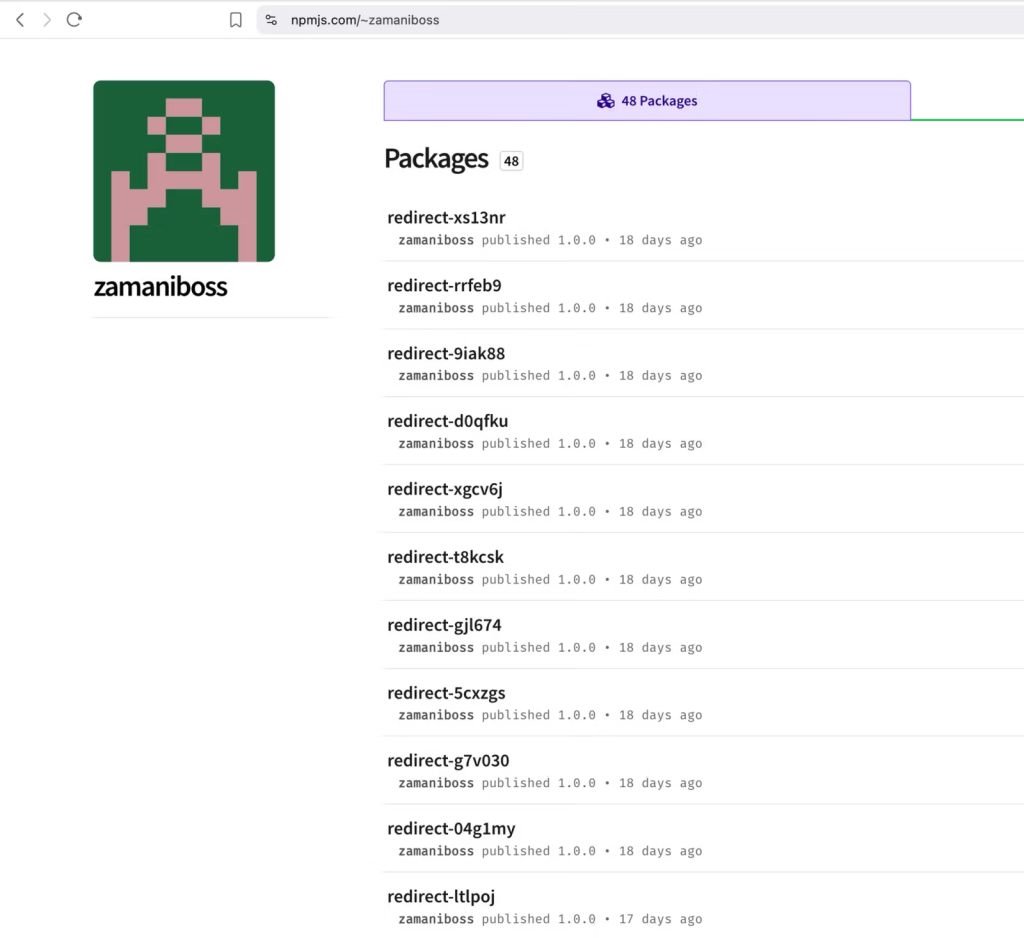
The attackers developed sophisticated Python tooling to automate the entire campaign infrastructure. Analysis revealed redirect_generator.py scripts and PyInstaller-compiled executables that handle victim-specific targeting.
The automation system generates random six-character package names following the pattern “redirect-[a-z0-9]{6}” and processes JavaScript templates by injecting victim email addresses and phishing URLs.
The complete attack chain begins with publishing the package to npm, followed by automatic CDN hosting through unpkg.com. Threat actors then distribute HTML files themed as purchase orders and project documents to targeted victims.
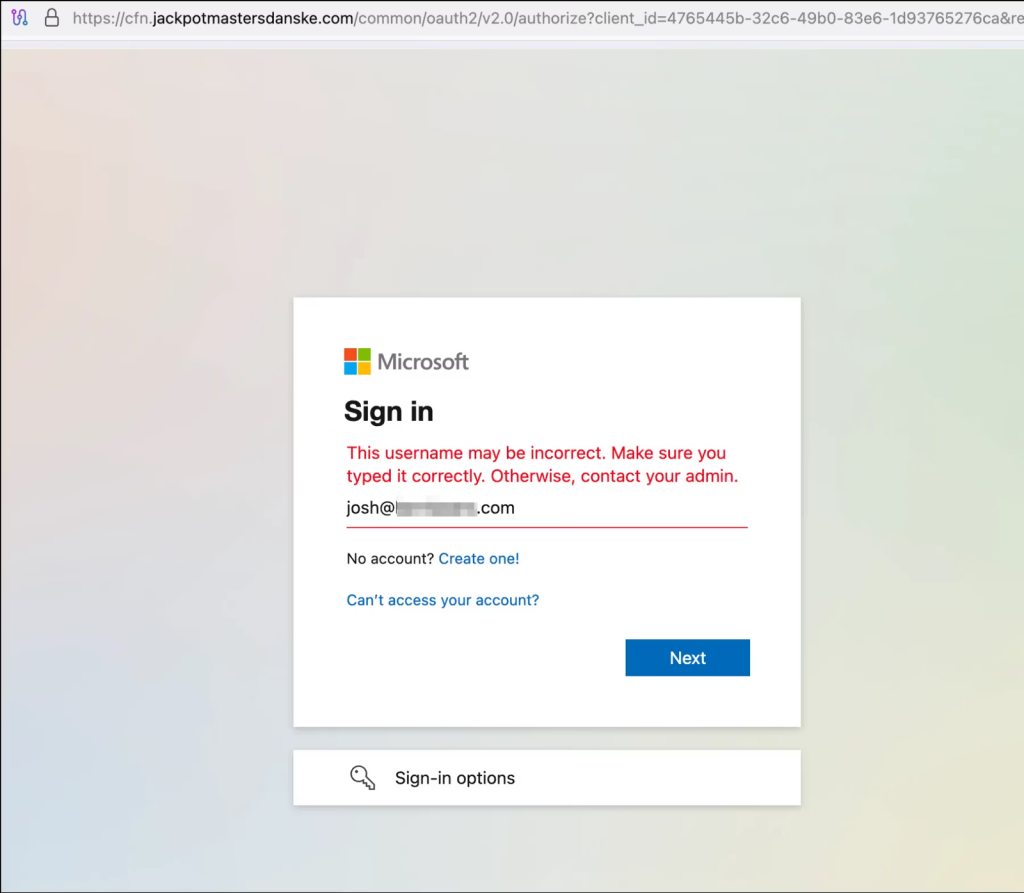
When victims open these HTML files, embedded JavaScript loads from the unpkg.com CDN and redirects to phishing pages that capture credentials with pre-filled email fields to appear legitimate.
Socket’s analysis identified over 630 HTML phishing lures across the 175 packages, using business document themes such as purchase orders like “PO3725.html” and technical specifications like “Product drawing and specification for Heat Exchangers.html.”
All HTML files contain the campaign identifier “nb830r6x” in meta tags and load JavaScript from unpkg.com URLs when opened in browsers.
Command Infrastructure and Industrial Targeting
The campaign operates through seven phishing domains, with cfn.jackpotmastersdanske.com serving as the primary infrastructure, handling 51% of packages.
Secondary infrastructure includes musicboxcr.com with base64-encoded parameters and villasmbuva.co.mz using Mozambique top-level domains. Base64-decoded URL parameters reveal specific targeting of Office 365 accounts without multi-factor authentication enabled.
Industrial manufacturing companies comprised 35% of targets, including Algodue, Piusi, Stratasys, ArcelorMittal, and Demag Cranes. Technology and electronics firms represented 20% of targets, featuring Moxa, D-Link, and Renishaw.
Energy and chemical companies accounted for 15%, including Sasol, ThyssenKrupp Nucera, and H2 Systems. Geographic targeting focused heavily on Western Europe, particularly Germany, the Netherlands, Belgium, and Italy.
Organizations should immediately force password resets for potentially compromised accounts, enable multi-factor authentication across all business systems, and review email gateway logs for HTML attachments delivered between September and October 2025.
The campaign’s automation and scale indicate an organized threat actor infrastructure requiring comprehensive defensive measures against similar npm-based phishing attacks.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates