In late September 2025, eSentire’s Threat Response Unit (TRU) uncovered a sophisticated Rust-based backdoor, dubbed “ChaosBot,” targeting a financial services environment.
This novel malware leverages compromised CiscoVPN credentials and an over-privileged Active Directory account to deploy and control infected systems.
Utilizing legitimate Microsoft Edge components for DLL side-loading and Discord as a stealthy command-and-control (C2) channel, ChaosBot demonstrates advanced evasion and persistence techniques that challenge traditional defenses.
Malware Deployment via CiscoVPN and Active Directory
The attack begins when threat actors obtain valid VPN credentials or trick users into launching malicious Windows shortcut files.
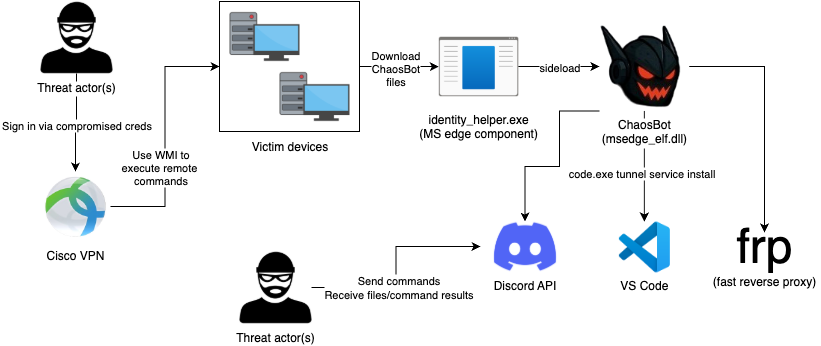
These shortcuts execute PowerShell commands to download the primary payload, msedge_elf.dll, and the helper executable identity_helper.exe into the Public user profile directory (C:\Users\Public\Libraries).
By side-loading the DLL into the signed Edge binary, ChaosBot avoids initial detection and gains code execution under the context of a trusted application.
With access to a misconfigured Active Directory service account named serviceaccount, the malware uses Windows Management Instrumentation (WMI) to execute remote commands across the network.
This approach enables rapid deployment of ChaosBot on multiple hosts without the need for interactive logins.
Once resident, ChaosBot performs system reconnaissance by executing built-in LOLBins such as systeminfo and ipconfig /all through the following PowerShell template:
powershellpowershell -Command "$OutputEncoding = [System.Text.Encoding]::UTF8; <SOME_COMMAND>"
The results are uploaded as text attachments via multipart/form-data to the threat actor’s Discord server, providing situational awareness and proof of execution.
Discord-Powered Command-and-Control and Evasion Techniques
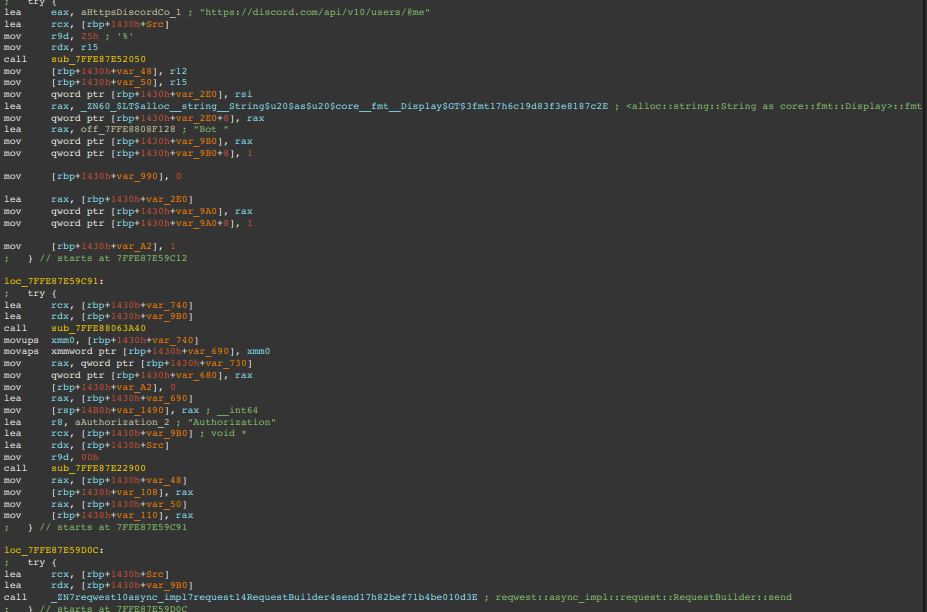
ChaosBot communicates stealthily over Discord’s API using either the reqwest or serenity Rust libraries. It validates its bot token with a GET request to /api/v10/users/@me, then creates a new channel named after the victim’s host.
Commands posted by operators in that channel are fetched in polling loops, enabling live remote execution.
File download and upload commands allow adversaries to transfer tools like Fast Reverse Proxy (frp), deployed as node.exe with a corresponding node.ini configuration, to maintain a reverse tunnel into AWS-hosted infrastructure.
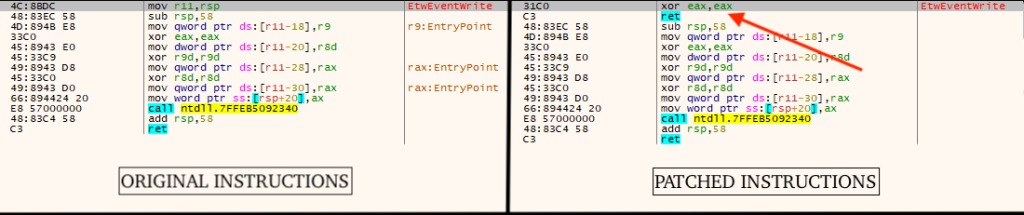
To evade detection, ChaosBot patches the first instructions of ntdll!EtwEventWrite, disabling Event Tracing for Windows telemetry. It also checks MAC address prefixes against known VMware and VirtualBox identifiers, exiting if a match is found.
In some variants, operators experimented with establishing Visual Studio Code Tunnels as alternate backdoors, though automation failures limited their effectiveness.
After discovery, TRU analysts isolated the infected host to contain the breach and guided remediation efforts.
Key recommendations include enforcing multi-factor authentication on VPN and AD accounts, limiting service account privileges, rotating credentials promptly, maintaining up-to-date patches, and deploying comprehensive EDR/NGAV solutions capable of detecting stealthy side-loading and legitimate-service-based C2 traffic.
For continuous visibility and rapid response, organizations lacking in-house resources should partner with a 24/7 Managed Detection and Response provider to defend against advanced threats like ChaosBot.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates