Remote Monitoring and Management (RMM) tools, long valued for their legitimate system administration capabilities, are increasingly being repurposed by threat actors to establish covert remote access and persistence.
Recent research published on DarkAtlas highlights how ConnectWise’s ScreenConnect platform has emerged as a preferred alternative to AnyDesk among adversaries, thanks to its flexibility, cross-platform deployment, and reduced detection footprint.
RMM Abuse in Modern Intrusions
ScreenConnect, developed by ConnectWise, provides administrators with remote access, scripting, file transfer, and unattended session management across Windows, macOS, Linux, and mobile platforms.
Despite its enterprise-grade design, these same features enable attackers to infiltrate target networks under the guise of legitimate remote support activity.
During the investigation, analysts noted that threat groups have leveraged ScreenConnect’s Build+ option accessible through its management console to generate customized installers and phishing-ready invite links.
These URLs (often spoofing trusted domains such as kh4lifa.test[.]screenconnect[.]com) allow adversaries to socially engineer victims into enrolling malware-laced clients. Once executed, the installer ScreenConnect.ClientSetup.msi deploys primarily in memory, leaving minimal on-disk traces.
The installed agent, launched as ScreenConnect.WindowsClient.exe under C:\Program Files (x86)\ScreenConnect Client (760c1fc14562a55f), registers as a persistent Windows service.
Its lightweight operations and encrypted communication channels make network and file-based detection difficult.
Analysts found configuration files such as user.config and system.config within the SysWOW64 directory, containing hostnames, encrypted keys, and session metadata linking compromised endpoints to remote C2 servers.
Detecting and Responding to ScreenConnect Abuse
Once ScreenConnect sessions are active, multiple Windows Event IDs can serve as indicators of intrusion. Event ID 4573 signals the initial connection attempt, while 100 and 101 within Application Logs track subsequent remote session activities.
File transfer events generate Event 201, recorded when adversaries exfiltrate or plant data via the ConnectWiseControl web interface. However, inbound file reception leaves minimal log evidence beyond observable edits in user.config.
Unlike AnyDesk, which preserves chat logs on disk, ScreenConnect stores conversation data in volatile memory, necessitating memory acquisition to recover chat-based artifacts or attacker instructions.
Forensic analysts should therefore prioritize RAM capture alongside endpoint and network telemetry collection for comprehensive incident reconstruction.
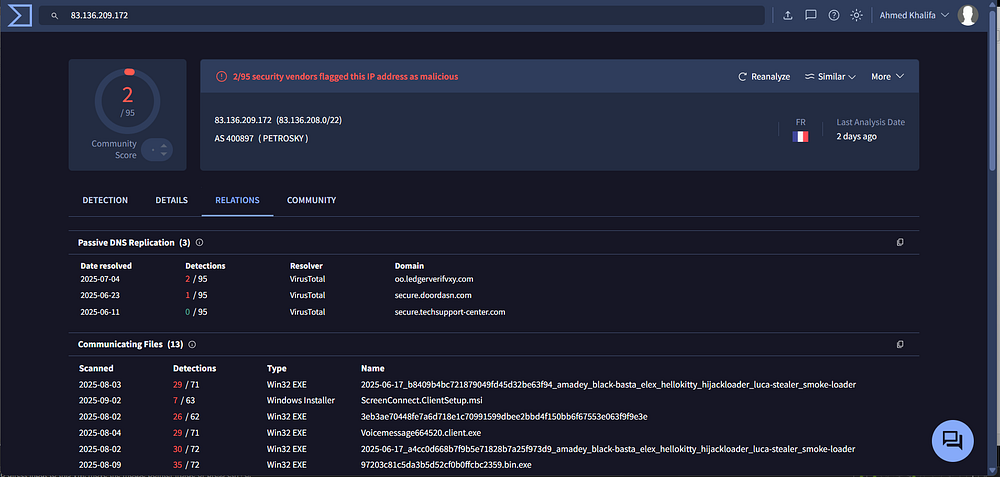
ScreenConnect’s legitimate functionality, combined with its silent installation and flexible delivery mechanisms, underscores the growing challenge for defenders.
Security teams are urged to monitor custom installer activity, anomalous remote sessions, and configuration file changes tied to ScreenConnect processes.
As RMM abuse escalates across APT campaigns, forensic vigilance and endpoint validation remain essential to deterring unauthorized remote control.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates