Security researchers at GitGuardian have uncovered a critical path traversal vulnerability in Smithery.ai, a popular Model Context Protocol (MCP) server hosting platform, that exposed over 3,000 hosted AI servers and compromised thousands of API keys.
The discovery, disclosed by security researcher Gaetan Ferry, highlights growing concerns about centralized AI infrastructure security and supply chain risks.
Docker Build Flaw Opens Door to Mass Compromise
The vulnerability stemmed from a configuration bug in Smithery’s server build process.
The platform, which hosts remote MCP servers to simplify deployment, relies on GitHub repositories containing server code and Docker configurations.
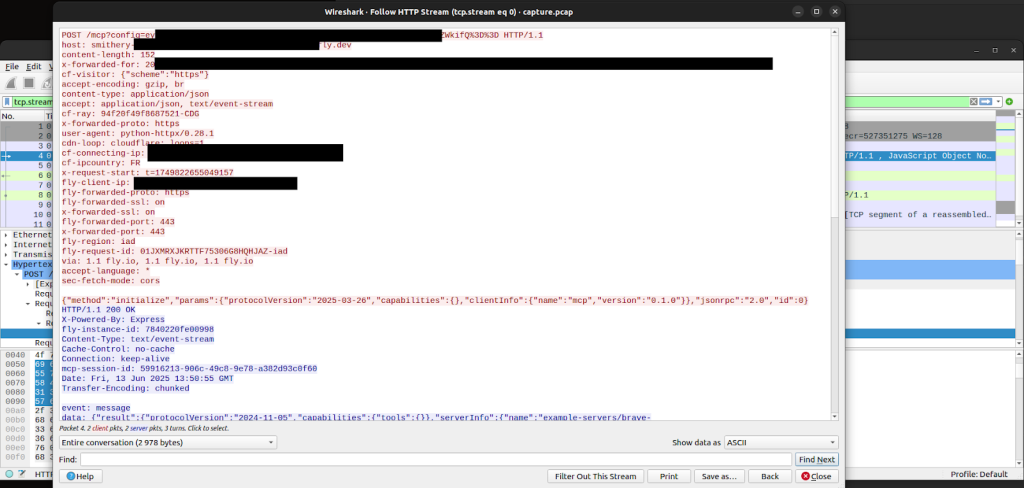
Researchers discovered that the dockerBuildPath parameter was improperly validated, allowing attackers to specify arbitrary filesystem locations as the Docker build context.
By exploiting this path traversal flaw, attackers could access sensitive files on Smithery’s build infrastructure.
Ferry demonstrated the attack by creating a malicious smithery.yaml configuration that pointed the build context to the parent directory, exposing the build user’s home directory.
Using a specially crafted Dockerfile, researchers exfiltrated filesystem listings and discovered Docker authentication credentials stored in the .docker/config.json file.
The compromised credentials proved severely overprivileged, granting access not only to Smithery’s Docker registry but also to fly.io’s machines API.
This allowed attackers to execute arbitrary code on any of the 3,000+ hosted MCP servers and access portions of Smithery’s infrastructure.
Testing revealed that attackers could dump network traffic from compromised servers, capturing API keys and authentication tokens transmitted by thousands of clients.
The vulnerability represents a textbook supply chain attack scenario, where compromising a single trusted platform could cascade into breaches affecting hundreds of organizations.
MCP servers function as gateways to sensitive external services, including databases, APIs, and data sources, making them high-value targets.
The centralized hosting model amplified the potential impact, creating a single point of failure for the entire ecosystem.
Ferry noted that most MCP servers use static, long-term API keys rather than OAuth tokens, which increases exploitation timeframes and limits privilege management capabilities.
This mirrors recent attacks like the Salesloft supply chain compromise, where attackers leveraged stored OAuth credentials to breach multiple customer environments.
GitGuardian disclosed the vulnerability to Smithery on June 13, 2025, and the platform responded swiftly. Within 24 hours, Smithery deployed a partial fix and rotated compromised credentials.
A complete remediation was implemented by June 15, just two days after disclosure. Investigators found no evidence that malicious actors exploited the vulnerability before it was patched.
The incident underscores the critical importance of secure configuration management in AI infrastructure and highlights emerging threats in the rapidly evolving AI security landscape.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today