Iran-linked advanced persistent threat (APT) group MuddyWater has launched a sophisticated cyber-espionage operation that uses a refreshed malware toolkit to infiltrate international organizations across the Middle East, North Africa, and beyond.
Group-IB Threat Intelligence attributes the campaign to MuddyWater with high confidence following the discovery of new phishing activity involving the Phoenix backdoor version 4, custom tools, and legitimate remote monitoring software.
Phishing to Phoenix Backdoor Deployment
According to Group-IB, the attack began through a compromised mailbox accessed via NordVPN, allowing MuddyWater to distribute malicious emails that appeared as legitimate correspondence.
The phishing messages carried Microsoft Word attachments, which, when macros were enabled, executed embedded Visual Basic for Applications (VBA) code. This script dropped a loader known as FakeUpdate, which decrypted and injected the Phoenix backdoor v4 into the system memory.
Once executed, Phoenix v4 established persistence, gathering system data, and maintaining remote command-and-control (C2) communication through WinHTTP.
The backdoor created a registry key under HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon, modifying the Shell value to ensure execution upon startup.
Supported commands allowed attackers to execute shells, transfer files, and adjust sleep intervals, enabling stealthy long-term espionage.
The C2 infrastructure revealed deeper operational clues. The domain screenai[.]online, registered on August 17, 2025, via NameCheap and fronted by Cloudflare, resolved to the real IP 159[.]198[.]36[.]115.
The server operated for five days before being decommissioned, hosting additional tools including remote monitoring utilities Action1 and PDQ RMM, both previously linked to MuddyWater activity.
Custom Credential Stealer and COM Persistence
Group-IB analysis also uncovered a custom browser credential stealer, disguised as a calculator application, designed to harvest login data from browsers such as Chrome, Edge, Opera, and Brave.
The tool decrypted stored credentials using recovered OS encryption keys, saving them to C:\Users\Public\Downloads\cobe-notes.txt.
Phoenix v4 featured an additional persistence mechanism using a Component Object Model (COM) DLL that triggered Mononoke.exe. This overlaps with previously observed CannonRat malware components, further reinforcing the attribution to MuddyWater.
Expanding Espionage Reach
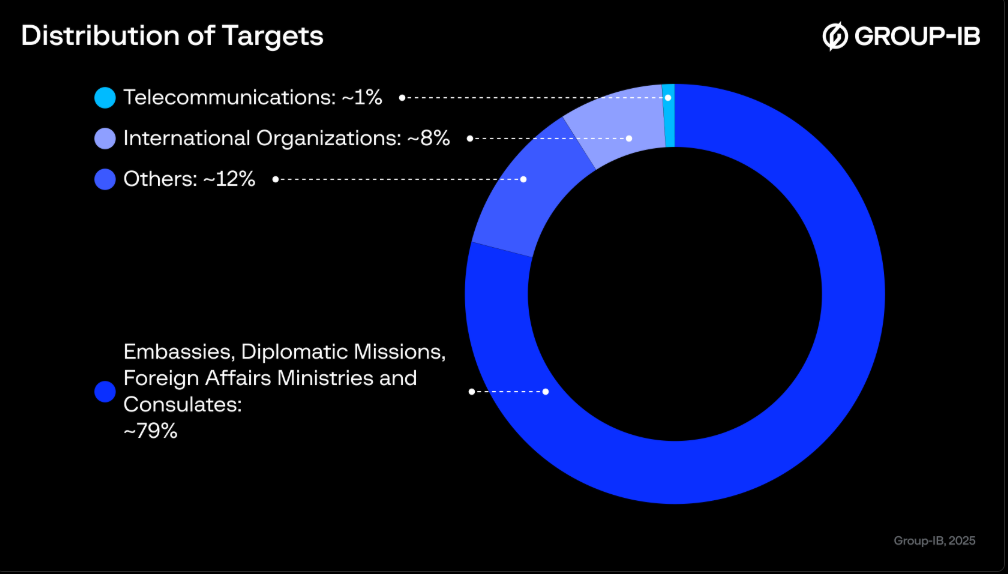
Group-IB reported that over 100 governmental and international organizations were targeted in this campaign, including those involved in diplomacy, humanitarian operations, and the energy sector.
The espionage operation showcases MuddyWater’s integration of custom implants with legitimate tools, signaling increasing technical maturity and a continued focus on geopolitical intelligence gathering.
The campaign’s discovery highlights the persistent threat posed by Iran-aligned actors, emphasizing the need for strengthened defense controls such as EDR tuning, macro restrictions, and vigilant monitoring of RMM tool usage within enterprise networks.
Indicators of Compromise (IOCs)
| Backdoor | mononoke.exe | 668dd5b6fb06fe30a98dd59dd802258b45394ccd7cd610f0aaab43d801bf1a1e |
| Backdoor | mononoke.exe | 5ec5a2adaa82a983fcc42ed9f720f4e894652bd7bd1f366826a16ac98bb91839 |
| Backdoor | sysProcUpdate | 1883db6de22d98ed00f8719b11de5bf1d02fc206b89fedd6dd0df0e8d40c4c56 |
| Backdoor | sysProcUpdate | 3ac8283916547c50501eed8e7c3a77f0ae8b009c7b72275be8726a5b6ae255e3 |
| Backdoor | sysProcUpdate | 76fa8dca768b64aefedd85f7d0a33c2693b94bdb55f40ced7830561e48e39c75 |
| Backdoor | sysProcUpdate | 3d6f69cc0330b302ddf4701bbc956b8fca683d1c1b3146768dcbce4a1a3932ca |
| C2 Domain | Creation date 2025-08-17 | screenai[.]online |
| C2 IP | real IP address behind CloudFlare | 159[.]198[.]36[.]115 |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates