Agenda, also known as Qilin, has deployed a new Linux-based ransomware variant that runs on Windows hosts, marking a significant escalation in the group’s multi-platform attack operations.
According to Trend™ Research, attackers used legitimate IT tools such as Splashtop Remote and WinSCP to deliver a Linux payload, effectively bypassing Windows-centric security systems and endpoint detection solutions.
Cross-Platform Execution via Remote Tools
The campaign abuses remote management and file-transfer tools to deploy ransomware across hybrid environments quietly. Attackers combined WinSCP, a secure file transfer tool, with Splashtop Remote to execute a Linux binary directly on Windows hosts.
This technique allows cross-environment propagation and evasion of traditional defenses that are not configured to detect Linux binaries executed on Windows.
Trend Labs observed that Agenda leveraged ATERA Networks’ remote monitoring platform to install AnyDesk, along with ScreenConnect for command execution and persistence.
The attackers performed targeted credential harvesting against Veeam backup infrastructure, extracting credentials from multiple databases to disable recovery and steal backup tokens before deploying the payload.
The hybrid ransomware then utilized SPLASHTOP’s SRManager.exe to execute the Linux binary (mmh_linux_x86-64) on Windows machines, demonstrating one of the first known cross-compiled ransomware deployments through legitimate enterprise tools.
BYOVD and VMware Targeting
Trend’s analysis revealed that Agenda relied heavily on Bring Your Own Vulnerable Driver (BYOVD) techniques to neutralize antivirus and EDR tools.
Malware components like 2stX.exe and Or2.exe exploited the vulnerable driver eskle.sys from a Chinese gaming vendor to disable security products.
Additional DLL loaders, including msimg32.dll, dropped malicious drivers (rwdrv.sys, hlpdrv.sys) known from Akira ransomware campaigns, further expanding evasion capabilities.
The Linux variant showcased hypervisor awareness, including detection of VMware ESXi and Nutanix AHV environments.
Its configuration included whitelisting, timed execution, and password-protected encryption routines, suggesting the group’s focus on virtualization infrastructure commonly used in enterprise data centers.
Trend researchers found that the attackers distributed SOCKS proxies (socks64.dll) across Veeam, VMware, and Adobe directories to conceal command-and-control traffic. This multi-proxy setup maintained communication redundancy and helped mask malicious activity under regular enterprise traffic.
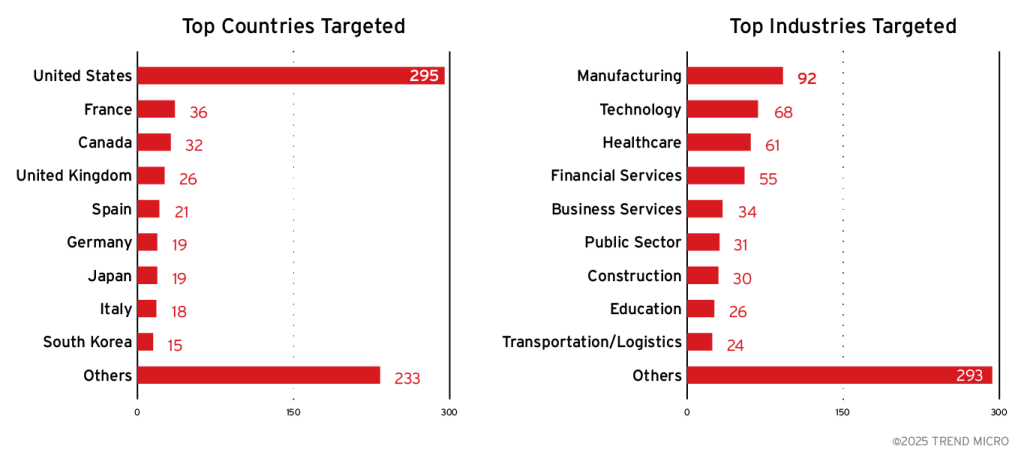
Agenda has compromised over 700 organizations across 62 countries this year, targeting manufacturing, financial, and healthcare sectors. Experts warn enterprises using RMM platforms and hybrid setups to tighten access controls, monitor credential use, and detect Linux payload execution on Windows systems.
Trend Vision One™ now detects and blocks the identified IoCs, offering intelligence reports and hunting queries to identify similar cross-platform intrusions.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates