ESET researchers have uncovered a new wave of Operation DreamJob, a long-running campaign conducted by the Lazarus Group, a North Korea-aligned advanced persistent threat (APT) actor.
The operation has recently targeted several European defense companies, particularly those engaged in unmanned aerial vehicle (UAV) development and manufacturing.
Researchers assess that the primary motive was the theft of proprietary data and military manufacturing know‑how linked to UAV systems currently deployed in Ukraine.
Technical aspects of the attack
The ongoing campaign, active since March 2025, leveraged social engineering as its entry vector a hallmark of Operation DreamJob.
Targeted employees received fabricated job offers that included malicious attachments and trojanized software that executed infection chains when opened.
ESET telemetry identified three affected entities: a metal engineering company in Southeastern Europe, an aircraft component manufacturer, and a Central European defense firm.
All incidents involved a dropper carrying the internal name “DroneEXEHijackingLoader.dll,” suggesting a deliberate focus on drone technology. This DLL served as a loader for ScoringMathTea, a remote access trojan (RAT) that grants attackers complete control of compromised systems.
First identified in 2022, ScoringMathTea has become Lazarus’s preferred payload for espionage operations, with capabilities including file manipulation, system reconnaissance, and remote command execution.
To evade detection, Lazarus embedded their malicious code into legitimate open-source projects from GitHub, such as DirectX Wrappers, Notepad++ plugins, and MuPDF Reader. These modified binaries employed DLL proxying and AES‑128 or ChaCha20 encryption to conceal secondary payloads.
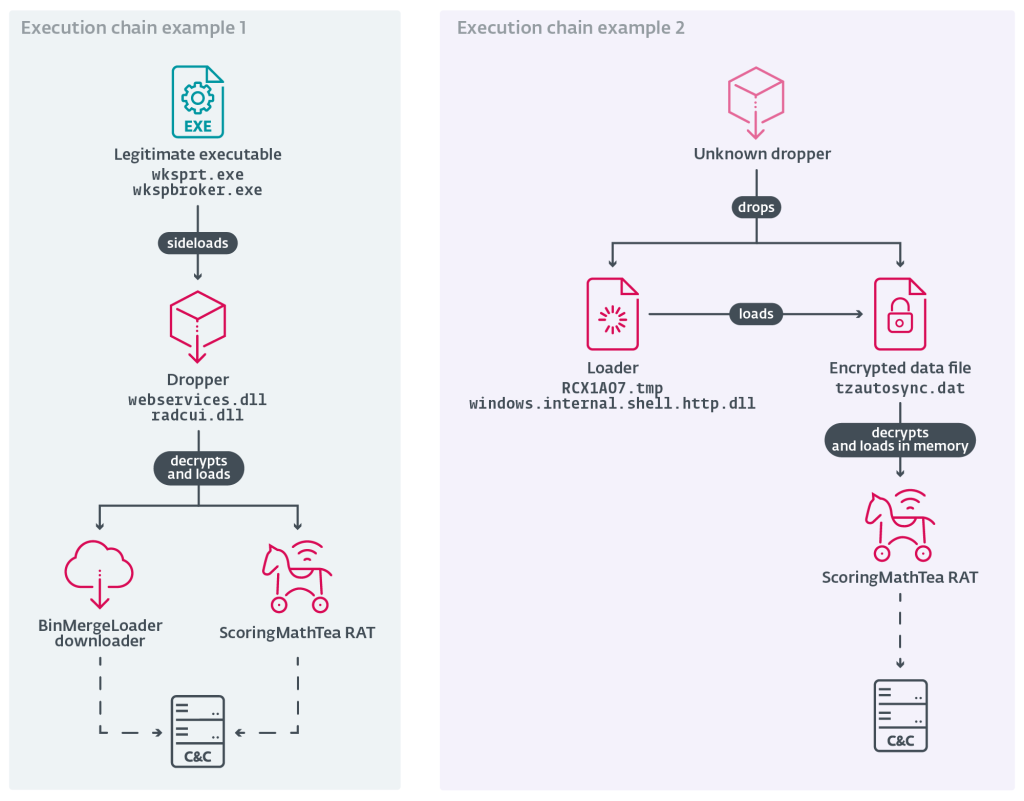
The attackers also created QuanPinLoader and BinMergeLoader, leveraging the Microsoft Graph API for stealthy command-and-control (C2) communications using legitimate authentication tokens. None of the encrypted payloads appeared on disk, increasing operational stealth.
Geopolitical context and motivations
ESET reports that the targets were indirectly linked to ongoing conflict dynamics between Russia and Ukraine, with some victim companies supplying components used in UAVs operating in Ukrainian airspace.
North Korean troops have reportedly supported Russia on the battlefield, likely motivating the Lazarus operation to collect UAV-related intelligence that could enhance Pyongyang’s domestic drone program.
North Korea has been investing heavily in drone manufacturing infrastructure, including efforts to replicate Western UAV designs such as the RQ‑4 Global Hawk and MQ‑9 Reaper.
The cyberattacks are likely part of Pyongyang’s broader strategy to steal advanced aeronautical data, streamline drone production, and possibly export low-cost combat UAVs.
ESET’s findings suggest that despite heightened awareness of Operation DreamJob, the campaign continues to exploit human factors successfully.
The trend underscores persistent vulnerabilities in employee vetting and highlights the urgent need for defense contractors to strengthen detection and training programs against social-engineering threats.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates