Google’s Threat Intelligence Group (GTIG) has uncovered a Vietnamese cybercriminal campaign that leverages fake job postings to compromise digital marketing professionals and hijack corporate advertising accounts.
The financially motivated cluster, tracked as UNC6229, employs advanced social engineering and malware-delivery tactics to infiltrate business environments via victims’ personal devices and online credentials.
Social Engineering Behind “Fake Career” Scams
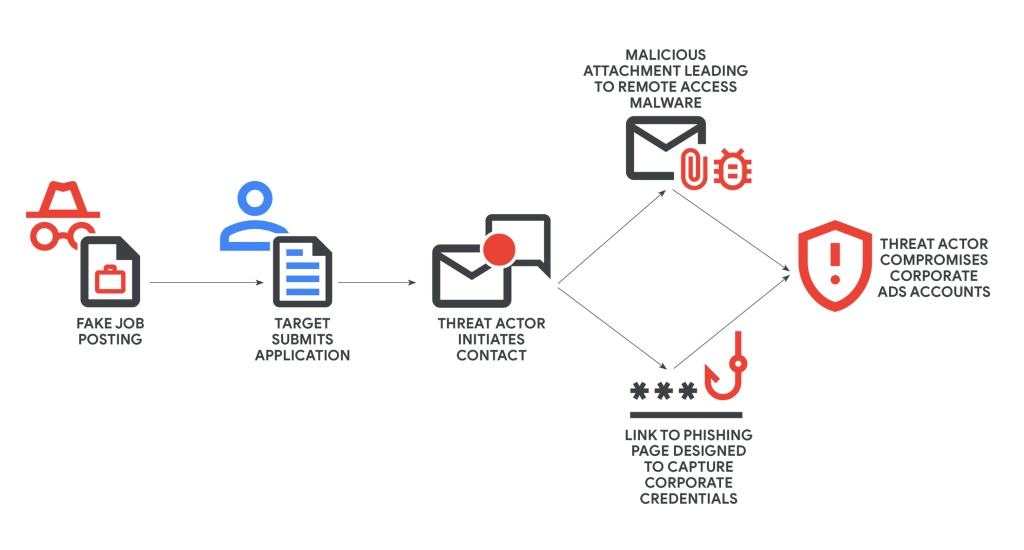
GTIG’s research reveals that UNC6229 relies on a victim-initiated interaction model, in which unsuspecting job seekers apply to fraudulent openings posted on legitimate platforms like LinkedIn and freelance marketplaces, and even on attacker-controlled job websites such as staffvirtual[.]website.
These fake listings typically advertise remote roles in the digital marketing and advertising sector.
Once a target applies, attackers collect the individual’s name, resume, and contact information, laying the groundwork for personalized phishing or malware distribution. The initial contact usually appears legitimate, referencing the relevant job post to build credibility.
GTIG reports that the actors frequently use customer relationship management (CRM) tools, including instances of Salesforce that have been abused, to send emails and manage their operations.
This exploitation of trusted SaaS infrastructure helps their messages evade spam filters and reach victims’ inboxes.
Malware and Phishing Techniques
The attack progresses when the victim receives either a malicious attachment or a phishing link. In malware-driven variants, the attacker sends a password-protected ZIP archive that purports to be a skills test or pre-employment form.
Once opened, the file deploys remote access trojans (RATs), enabling full system compromise and credential theft.
Phishing variants route victims to convincing sign-in portals that mimic major corporate services, with back-end kits designed to capture credentials from platforms like Microsoft 365 and Okta, even bypassing using multi-factor authentication (MFA) mechanisms.
Once inside a compromised system, the attackers can access connected business accounts, particularly advertising or social media management platforms. These accounts are then monetized—either by running fraudulent ads for profit or by reselling them to other threat groups.
Expanding Threat Outlook
GTIG attributes UNC6229 to a Vietnam-based operation showing signs of collaboration and tool-sharing among multiple financially motivated actors.
While the current campaigns focus on digital marketing professionals, GTIG warns that similar tactics could easily expand into other industries handling sensitive commercial data.
To mitigate risk, Google has blocked all identified domains and files through its Safe Browsing service.
The company continues to share intelligence with the broader security community to enhance detection of SaaS abuse and reinforce defenses against sophisticated, trust-based phishing campaigns.
Indicators of Compromise
The following indicators of compromise are available to registered users in a Google Threat Intelligence (GTI) collection.
staffvirtual[.]website |
137a6e6f09cb38905ff5c4ffe4b8967a45313d93bf19e03f8abe8238d589fb42 |
33fc67b0daaffd81493818df4d58112def65138143cec9bd385ef164bb4ac8ab |
35721350cf3810dd25e12b7ae2be3b11a4e079380bbbb8ca24689fb609929255 |
bc114aeaaa069e584da0a2b50c5ed6c36232a0058c9a4c2d7660e3c028359d81 |
e1ea0b557c3bda5c1332009628f37299766ac5886dda9aaf6bc902145c41fd10 |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates