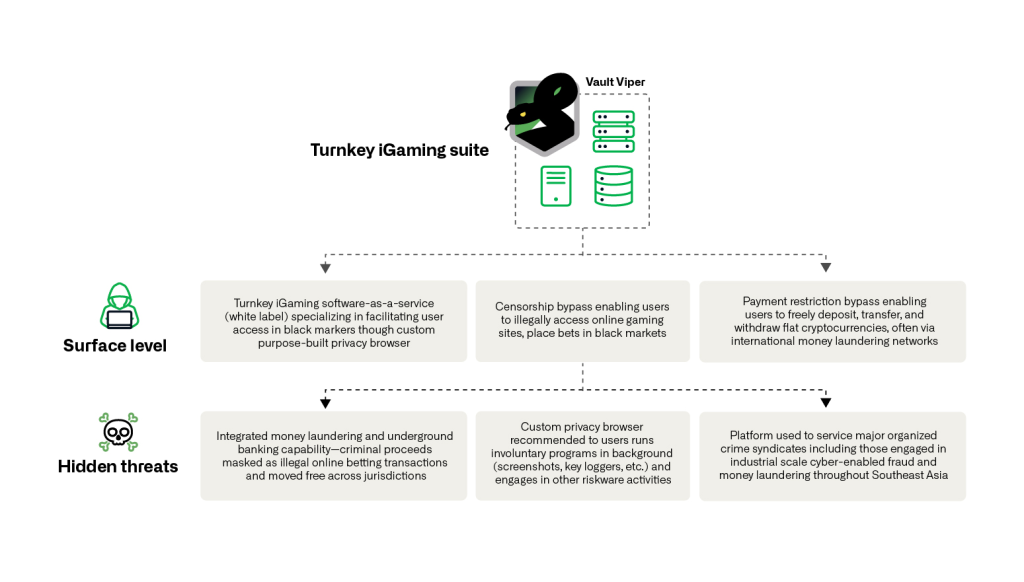
Vault Viper, a threat actor recently unmasked by Infoblox Threat Intelligence, has emerged at the intersection of Asia’s online gambling industry and cyber-enabled organized crime, targeting betting sites with a custom browser engineered for malware distribution.
This operation centers on the Universe Browser, a modified Chromium build developed and distributed by the Baoying Group (BBIN), one of Asia’s largest iGaming solution providers with deep-rooted ties to criminal syndicates and transnational money laundering networks.
Custom Browser as Crimeware
The Universe Privacy Browser is compellingly advertised as a privacy solution for online gamblers, promising the ability to bypass censorship and access betting platforms in countries where gambling is outlawed.
Behind this façade, technical analysis reveals overt malware characteristics: the browser routes traffic through actor-controlled proxy servers in China, installs persistent background programs, and manipulates network configurations to establish covert communications and facilitate credential theft.
The Windows variant, distributed as UB-Launcher.exe, demonstrates advanced anti-analysis techniques, checking for virtual machines, modifying the Windows registry for persistence, and injecting code into system processes such as IEXPLORE.EXE, classic traits of information stealers and remote access trojans.
On execution, Universe Browser installs itself into a legitimate Chrome directory, replacing binaries and disabling Chrome’s security features (sandboxing, developer tools).
It then loads custom extensions (Screenshot and lineSelector) that monitor and interact with gambling domains, passing encrypted data and screenshot payloads to the remote Vault Viper infrastructure.
The browser’s core networking binary, UBService.exe, manages proxy routing, stores encrypted records in local SQLite databases, and handles updates by connecting to command-and-control domains using hardcoded cryptographic keys: a robust setup for persistent device access and mass exploitation.
Criminal Ecosystem & Infrastructure
Vault Viper’s reach extends across thousands of gambling and fraud-associated domains, anchored by BBIN’s infrastructure in the Philippines and Taiwan but obfuscated by shell companies around the globe.
The threat actor leverages authoritative hosting on Western cloud providers, distinct ASN peering, and distributed DNS management, allowing rapid domain shifting and resilience against enforcement.
The browser, frequently pushed via illegal casino websites such as Bolai Casino, is also distributed on mobile platforms, requesting excessive permissions and locking out rooted devices to resist analysis.
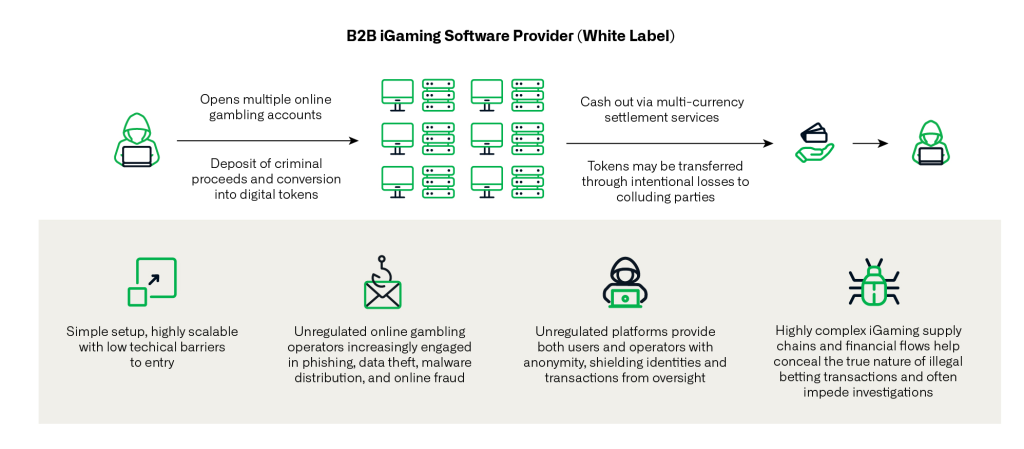
This technical campaign goes hand-in-hand with an elaborate money laundering scheme and ties to notorious criminal organizations, including the Suncity Group, whose leader, Alvin Chau, was convicted for orchestrating multi-billion-dollar illegal betting operations across Asia.
Vault Viper’s malware ecosystem not only enables clandestine access and surveillance of users but also siphons personal and financial data from unwitting gamblers, incorporating stolen credentials and illicit payments into extended cybercrime operations.
In sum, Vault Viper’s customized browser stands as both an exploitation toolkit and a gateway for deeper criminal monetization, representing a sophisticated evolution in the threat landscape surrounding Asia’s online betting industry.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates