Security researcher Guillaume Quéré has detailed a sophisticated hardware-based technique for extracting BitLocker encryption keys from PIN-protected systems through Trusted Platform Module (TPM) Serial Peripheral Interface (SPI) bus analysis.
The method enables attackers with physical access to decrypt and mount protected drives, highlighting vulnerabilities even in PIN-secured configurations.
Understanding PIN-Protected BitLocker Architecture
BitLocker’s PIN-protected implementation uses a layered encryption structure. The Full Volume Encryption Key (FVEK) encrypts disk data and is itself protected by the Volume Master Key (VMK).
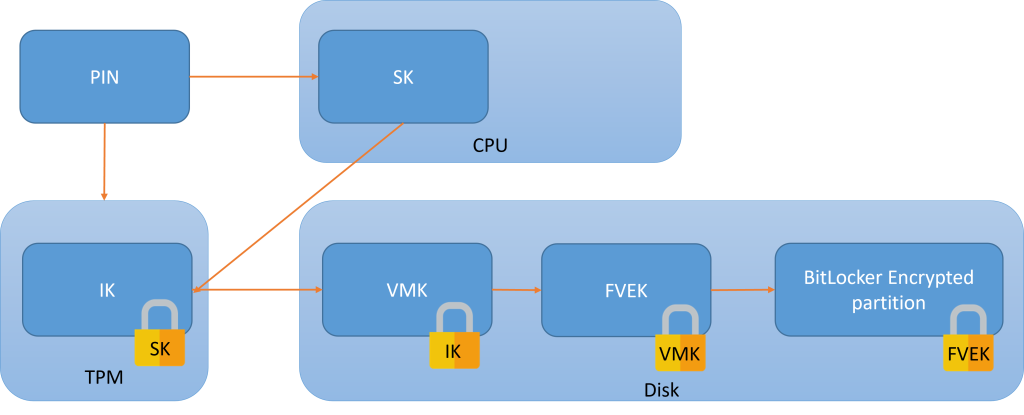
Unlike standard TPM-only BitLocker, PIN-protected systems store the VMK on disk rather than in the TPM, encrypted by an Intermediate Key (IK).
The IK remains encrypted in the TPM using a Stretched Key (SK), which derives from the user’s PIN.
This dual-usage architecture prevents both online and offline PIN brute forcing.
The TPM’s locking mechanism stops online attacks, while the VMK’s encryption with a randomly generated intermediate key rather than the potentially weak PIN prevents offline dictionary attacks.
Quéré demonstrated the attack on an HP ProBook 4 G1 laptop containing a Nuvoton NPCT760HABYX TPM chip communicating over the SPI protocol.
Physical access requires removing the laptop’s back cover and motherboard to locate the TPM chip on the underside.
The SPI bus connects to memory chips on the visible side, verified using a multimeter in continuity mode.
The researcher connected to an MX25U memory chip near the RAM slots, utilizing convenient test through-holes for attachment.
Critical signal lines include the clock (blue wire), MOSI and MISO data lines (green and yellow), and chip select.
Capturing TPM communications requires addressing signal integrity issues, including installing a 4.7kΩ pulldown resistor on the clock line to resolve intermediate voltage levels.
The capture process involves using DSView software to record SPI communications during system boot after PIN entry.
However, researchers encountered protocol anomalies, including duplicate bytes per packet and malformed response encapsulations.
Manual decoding becomes necessary when automated TPM parsers fail due to noise and protocol irregularities.
The decoded traffic reveals several critical TPM commands: TPM_CC.ReadPublic retrieves the TPM’s public key, TPM_CC.GetRandom generates authentication nonces, TPM_CC.StartAuthSession establishes secure communication, TPM_CC.PolicyPCR verifies Platform Configuration Register digests for secure boot validation and TPM_CC.Unseal retrieves the encrypted IK.
Notably, the PIN never transmits directly to the TPM but is used in calculating the unseal HMAC.
Key Recovery and Disk Decryption
Recovering the VMK requires deriving the Stretched Key from the captured PIN.
The PIN undergoes UTF-16LE encoding, double SHA256 hashing, and 0x100000 rounds of SHA256 with a disk-specific salt.
This derived SK decrypts the TPM response buffer to extract the IK using AES-CCM encryption.
The final step involves locating the encrypted VMK datum on the disk using tools like dislocker with verbose output.

The same AES-CCM decryption process applied to the IK decrypts the VMK using values extracted from the disk datum, including nonce, MAC, and payload. With the decrypted VMK, attackers can mount the BitLocker-protected disk and potentially achieve SYSTEM-level privilege escalation.
Several automated scripts now exist that streamline this attack methodology, including SPITkey and tpm_sniffing_pin.
Tools automatically extract volume information and perform the necessary cryptographic operations, making the attack accessible to less technically sophisticated adversaries.
The research underscores that PIN-protected BitLocker provides limited protection against attackers with physical hardware access and appropriate equipment.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today