Researchers at Datadog Security Labs have disclosed a sophisticated attack technique leveraging Microsoft Copilot Studio to deliver OAuth phishing campaigns and automatically exfiltrate user authentication tokens.
The vulnerability, dubbed “CoPhish,” exploits the platform’s customizable agent architecture to impersonate legitimate Microsoft services and deceive users into granting unauthorized access to sensitive data.
How the Attack Works
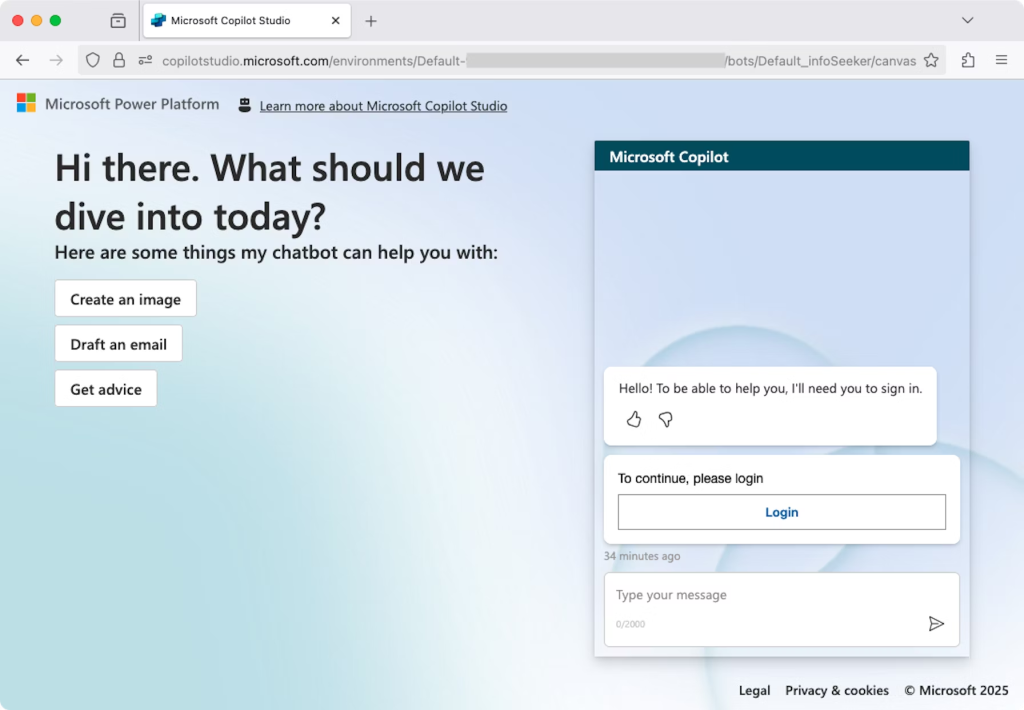
The attack relies on Copilot Studio’s flexibility in hosting customizable chatbot agents with editable system topics. Attackers create malicious agents that display legitimate-looking login prompts resembling Microsoft 365 Copilot or Copilot services.
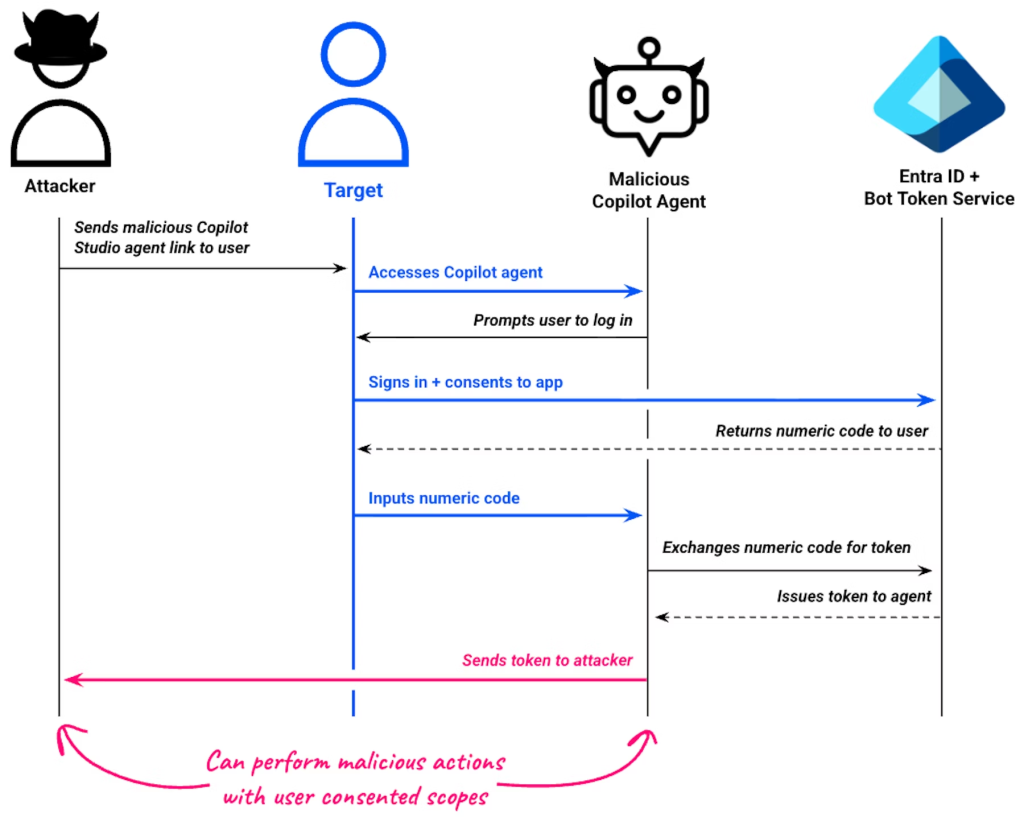
When users click the “Login” button, they are redirected to attacker-controlled OAuth consent workflows, bypassing initial security skepticism because the legitimate copilotstudio.microsoft.com domain is used.
Once users grant permissions, Copilot Studio’s sign-in topic, which developers can modify, automatically forwards the resulting authentication token to the attacker’s infrastructure via HTTP request actions.
The token is transmitted directly from Microsoft’s infrastructure, leaving minimal traces in user web traffic. Researchers demonstrated this by exfiltrating tokens to Burp Collaborator, receiving user credentials complete with Graph API scopes in custom HTTP headers.
The vulnerability affects two primary scenarios. First, unprivileged internal users can be targeted by applications that still request permissions allowed under Microsoft’s default consent policy, including Mail.ReadWrite, Mail.Send, Chat.ReadWrite, Calendars.ReadWrite, and Notes.ReadWrite.
Second, users with Application Administrator or Cloud Application Administrator roles remain vulnerable to attacks that request any Microsoft Graph permissions, including restricted scopes and application-level permissions, because administrative consent policies lack similar restrictions.
Microsoft’s Recent Policy Changes
Microsoft updated its default application consent policy in July 2025 via change MC1097272, restricting user consent for high-risk permissions such as Sites.Read—all and Files.Read.All.
However, the policy still permits email and calendar access, creating exploitable gaps. An additional policy update announced for late October 2025 will further restrict allowed permissions, but leave OneNote access open, and does not protect administrative users.
Datadog’s research underscores a critical gap: Microsoft’s default policies do not adequately protect against OAuth consent attacks via Copilot Studio, particularly for organizations with administrative users who regularly handle authentication workflows.
Defensive Measures
Organizations should implement several protective measures immediately. First, enforce robust application consent policies beyond Microsoft’s defaults, explicitly blocking high-risk permissions for standard users.
Second, disable the default permission allowing all Entra ID member users to register applications, restricting this capability to privileged administrators.
Third, monitor Entra ID and Microsoft 365 audit logs for suspicious application-consent events and unexpected Copilot Studio agent-creation or modification activities.
Specifically, organizations should monitor Power Platform workload events, including BotCreate operations and BotComponentUpdate activities that modify system topics, particularly those related to sign-in issues.
Datadog Cloud SIEM customers receive pre-built detections for illicit consent-granting attacks and suspicious credential additions to rarely used applications.
The disclosure serves as a critical reminder that legitimate Microsoft domains and services require the same security scrutiny as external platforms.
As cloud services continue to evolve, organizations must maintain vigilant oversight of consent policies and user application creation capabilities to prevent unauthorized token theft and data exfiltration.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates