Threat actors have discovered a potent combination of social engineering and technical exploitation that bypasses traditional security controls.
By combining FileFix phishing tactics with cache-smuggling techniques, attackers are deploying second-stage payloads without triggering endpoint detection and response (EDR) systems or network monitoring tools that typically flag suspicious web requests.
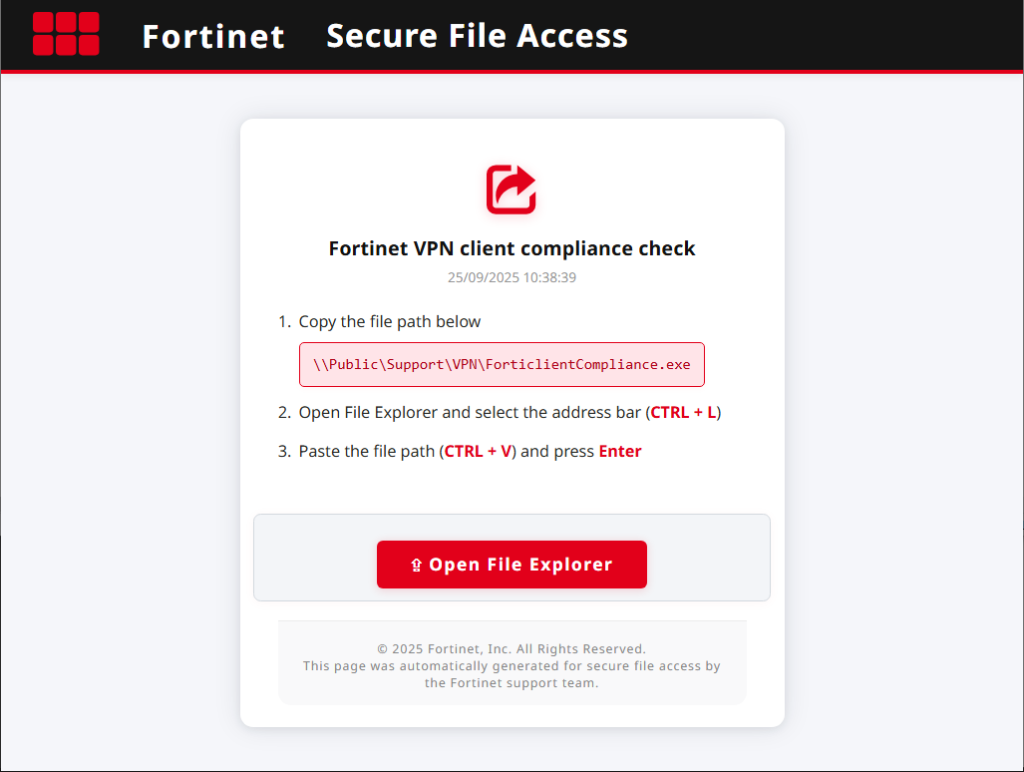
The attack chain begins with a deceptive phishing lure masquerading as legitimate software, such as a Fortinet VPN compliance checker.
Users are socially engineered to copy and paste a seemingly innocuous command, the entire malicious payload hidden behind padding characters and presented as a mundane file path. When pasted into Windows Explorer’s address bar, the hidden PowerShell command executes invisibly.
Technical Innovation: Eliminating Web Requests
What distinguishes this campaign from previous ClickFix variants is the elimination of explicit file downloads. Instead of downloading payloads directly, attackers leverage the browser’s automatic caching mechanism.
The phishing page contains obfuscated JavaScript that fetches a file presented as a JPEG image through HTTP headers, though the actual content is arbitrary binary data.
The browser automatically stores this fake image in its cache directory without user interaction or additional web requests visible to security tools.
The PowerShell script then navigates to the browser’s cache directory, searches through cached files using regular expressions for specific markers, and extracts the embedded payload, typically a ZIP archive containing the actual malware.
This technique circumvents security solutions that monitor file downloads or analyze PowerShell’s network activity, since no explicit web communication occurs after initial payload injection.
The attack’s sophistication deepens further through the smuggling of Exif data within legitimate-looking JPEG images. Researchers demonstrated that up to 64 kilobytes of data can be hidden within image metadata fields.
By embedding payloads after null bytes in Exif headers, the data remains invisible to most metadata parsers while remaining technically valid. When the browser caches these images, the hidden payload travels with them and is later extracted by malicious scripts using a simple regular expression.
Expanding Attack Surface
The implications extend beyond web-based phishing. Microsoft Outlook processes cached images similarly to web browsers, preemptively downloading and caching attachments even when image preview is disabled.
This enables Exif smuggling via email without requiring users to open attachments, creating a previously unavailable passive infection vector for attackers.
Security teams face a fundamental challenge: preventing these attacks requires monitoring unexpected process interactions with browser cache directories, restricting PowerShell execution, implementing DNS filtering for newly created domains, and educating users about social engineering tactics.
Organizations should also mandate stripping Exif data from inbound images and implement endpoint controls to detect suspicious cache manipulation.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates