Varonis recently uncovered a new remote access trojan (RAT) named Atroposia, which is gaining traction on underground forums as an affordable, modular cybercrime toolkit.
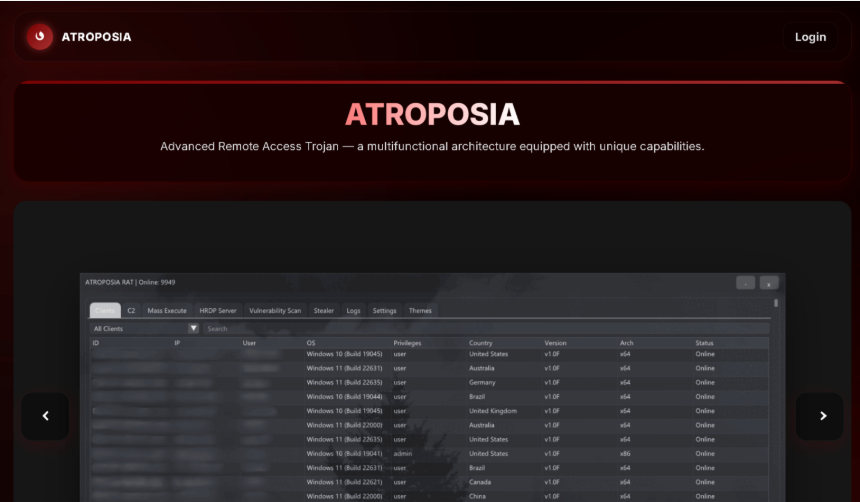
Priced at approximately $200 per month or $900 for six months, Atroposia caters to low- and no-skill attackers with its turnkey package that includes encrypted command channels, hidden remote desktop access, credential and cryptocurrency wallet theft, DNS hijacking, local vulnerability scanning, and robust persistence mechanisms.
Hidden Remote Desktop and Fileless Data Exfiltration
A key feature of Atroposia is its stealthy remote desktop, branded HRDP Connect. This tool spawns an invisible remote desktop session in the background, with no visible notification to the victim.
This covert “shadow login” allows attackers to fully interact with the victim’s system, opening applications, viewing sensitive documents, and manipulating workflows in real-time without alerting the user.
Traditional remote access monitoring and alerts often miss this type of hidden session, enabling silent espionage and data theft. Atroposia also provides extensive file system control through a built-in file manager, granting attackers full directory browsing and data manipulation capabilities.
Its fileless Grabber module hunts for targeted files by extension or keyword and compresses them into password-protected zip archives entirely in memory for stealthy bulk exfiltration, minimizing on-disk footprints that traditional DLP systems can detect.
A stealer module targets saved credentials, chat app data, and cryptocurrency wallets, facilitating both lateral network movement and financial theft.
Clipboard Snooping and DNS Hijacking for Network Compromise
Another covert channel exploited by Atroposia is clipboard monitoring. It captures anything the user copies or cuts, including passwords, source code snippets, and confidential information.
Attackers can extract authentication tokens, session cookies, or crypto wallet addresses in near real-time, increasing the risk of account hijacking and fraudulent crypto transactions.
Beyond victim-host compromise, Atroposia manipulates network traffic via a DNS-hijacking module that silently redirects DNS queries to attacker-controlled IP addresses.
This enables phishing, man-in-the-middle attacks, and malware delivery, bypassing external DNS protections and even undermining HTTPS security by rerouting legitimate traffic to malicious servers.
Vulnerability Scanning and Persistence Mechanisms
Atroposia’s modular design is further exemplified by its built-in vulnerability scanner, which audits compromised systems to identify missing patches, misconfigurations, or exploitable software versions.
This intelligence enables attackers to escalate privileges, often via automatic UAC bypass, and to deepen their foothold by leveraging multiple persistence techniques that survive system reboots.
Varonis highlights Atroposia as part of a growing trend of criminal toolkits that lower the barrier to launching sophisticated cyberattacks. These platforms bundle complex discovery, delivery, and evasion techniques into easy-to-use interfaces accessible to even unskilled attackers.
Varonis’ Data Security Platform aids in early detection by monitoring for behavioral anomalies associated with Atroposia, such as unusual credential dumping, rogue DNS modifications, or lateral movement within networks.
This evolution in malware democratization signals an urgent need for enterprises to adopt advanced behavioral analytics and vigilant monitoring to defend against increasingly accessible and potent threats like Atroposia.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates