In an unprecedented security incident in September 2025, more than 500 gigabytes of internal data were leaked from Chinese infrastructure firms that operate the machinery behind the Great Firewall (GFW) of China.
This leak offered an unfiltered cross-section of China’s sprawling censorship architecture, exposing technical blueprints, operational logs, internal communications, and, crucially, the human networks behind the digital curtain.
The breach, believed to be the work of either a privileged insider or a highly coordinated external adversary, yielded an archive that researchers now estimate approaches 600GB and contains upward of 100,000 unique files.
Internal project management data, emails, technical manuals, configuration files, and operational runbooks were uncovered, many of which pertained directly to censorship and surveillance mechanisms used domestically and exported to multiple countries, including Myanmar, Kazakhstan, and Ethiopia.
Exposing the Technical Arsenal
Crucially, the dump exposed the RPM packaging server integral to distributing control software across targeted networks alongside Jira and Confluence exports, revealing the ticketing, bug reports, and deployment cycles that drive the evolution of China’s censorship stack.
PCAPs and raw IP logs from state-run telecoms, such as China Telecom and China Mobile, provided an unvarnished view of real-time monitoring, packet interception, and the operational tactics employed to filter, redirect, or silently drop traffic flagged as subversive or foreign.
Alongside this, a maze of spreadsheets listed VPN and proxy fingerprints, application telemetry, DNS queries, SSL certificates, and behavioral patterns that form the backbone of Chinese detection heuristics.
Visio diagrams detailed both the logical and physical architecture of firewall deployments down to the provincial level, suggesting a distributed yet centrally orchestrated apparatus.
The so-called “five rings network” diagrams and network status screenshots illuminated deep segmentation, VLAN zoning, and edge-control logic at play.
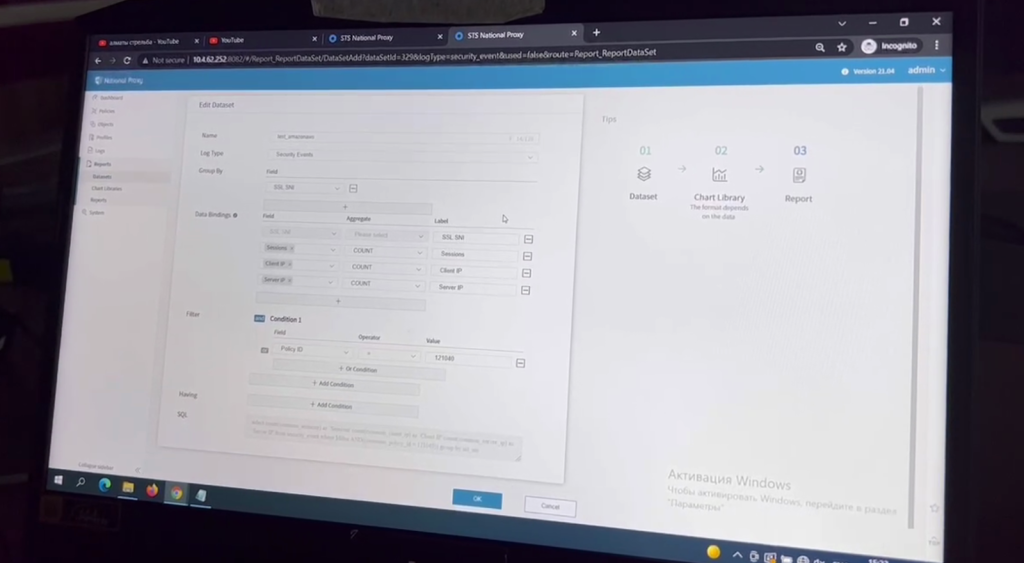
At the same time, OCR’d dashboard screenshots offered an unprecedented look at the management interfaces guiding censorship activities.
Unmasking the Human Infrastructure
System-level monitoring also became public, exposing session logs, thread utilization, CPU usage, and real-time alerts.
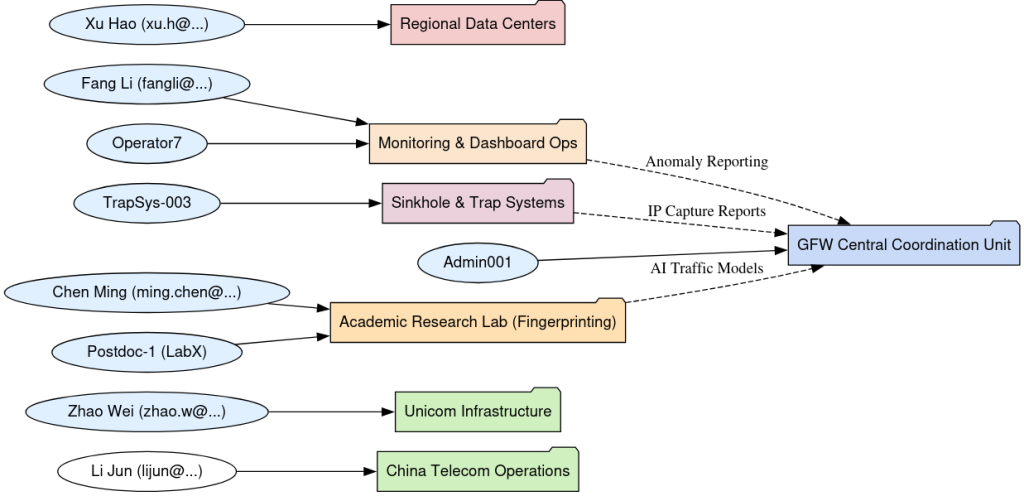
Significantly, hundreds of files retained internal metadata linking usernames, organizational affiliations, and even edit trails, offering a rare attribution vector tying actual engineers, operators, and state-linked contractors to censorship infrastructure.
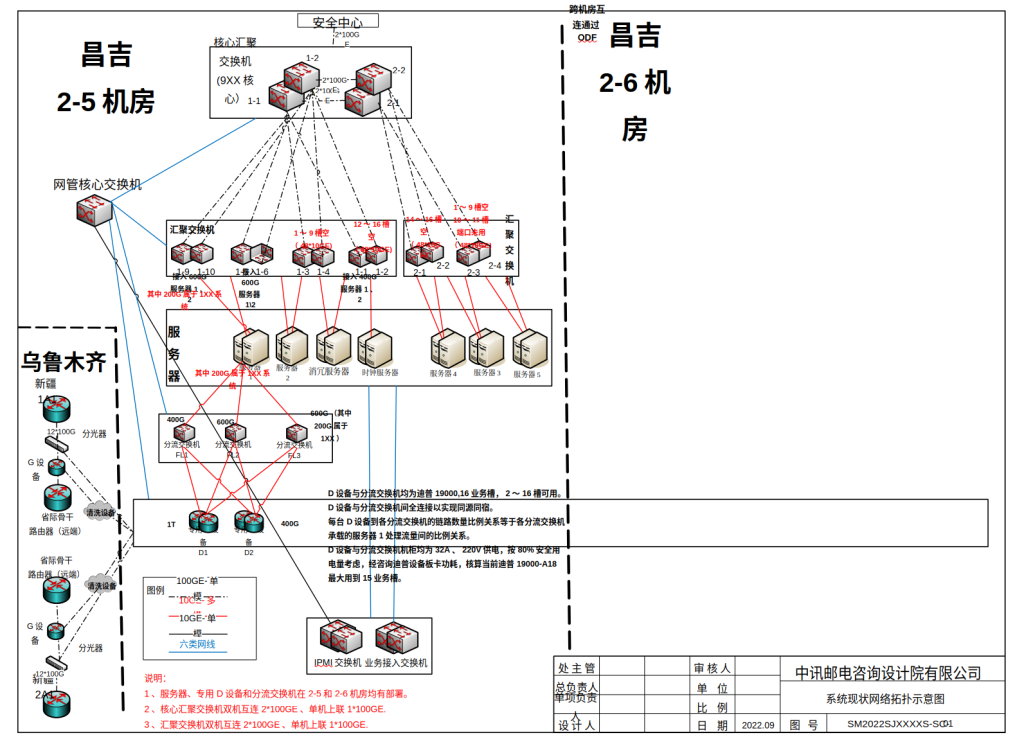
Organization: China Information and Communication Design Institute Co., Ltd
Operational records revealed repeated shortcomings and lapses in rule propagation, accidental exposures of regional blacklist data, and evidence of foreign entities probing China’s perimeter via honeypots.
These failures highlighted the brittle, reactive nature of GFW’s distributed enforcement and the reliance on periodic synchronization across provincial nodes.
The implications of the breach are sweeping. Technical insights into deep packet inspection (DPI), VPN heuristics, and SNI fingerprinting now empower circumvention communities to evade surveillance while exposing operational and human weak points that adversaries could exploit.
For the first time, the world can scrutinize not just the algorithms or the policy, but also the technical and human scaffolding that underpins China’s digital authoritarian ambitions.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates