A large-scale, ongoing phishing campaign is exploiting Cloudflare Pages and Zendesk infrastructure to impersonate customer support portals of well-known global brands.
Security researchers have identified more than 600 domains hosted on Cloudflare’s *.pages.dev subdomain being used in this operation, marking one of the most widespread abuse cases of developer-hosted infrastructure observed in recent months.
Large-Scale Abuse of Cloudflare Pages
Threat actors behind the campaign registered hundreds of typosquatted domains using patterns similar to legitimate brand names, such as slight misspellings or alternate letter placements.
These cloned domains often resemble official helpdesk or support sites, leading users to believe they are communicating with trusted customer support representatives.
The phishing pages are notably sophisticated and appear to be AI-generated, incorporating realistic branding, professional content, and functional chat widgets.
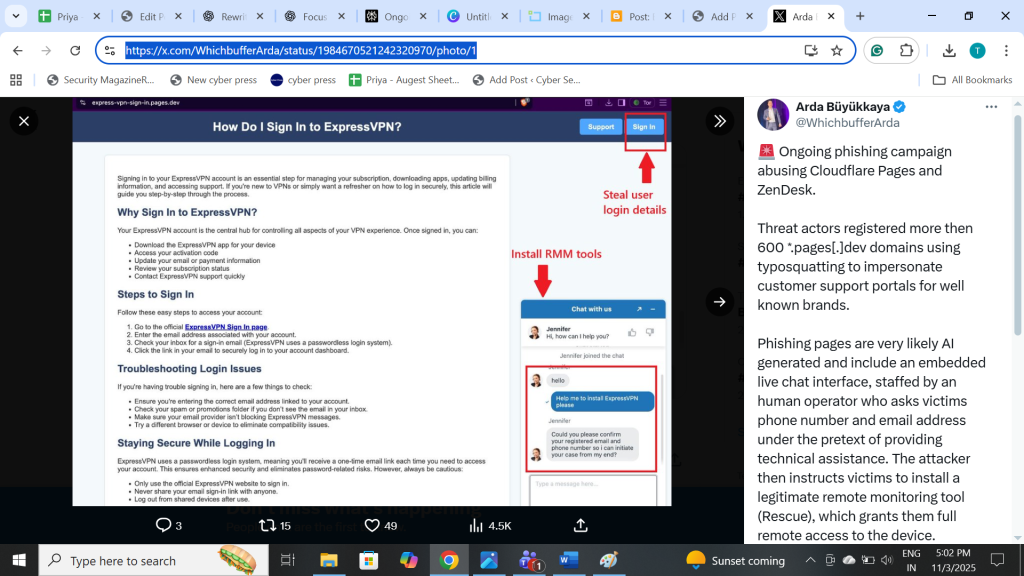
Each fraudulent portal contains an embedded live chat interface connected to an operator who engages directly with victims. During these interactions, the operator requests the victim’s phone number and email address under the pretext of verifying identity or initiating technical support.
Researchers report that the attackers subsequently instruct targets to download and install legitimate remote desktop software, specifically Remote Rescue or similar monitoring tools.
Once the victim grants remote access, the attacker gains complete control of the device, allowing them to navigate local files, harvest stored credentials, and intercept login sessions.
Social Engineering and Financial Theft
The ultimate goal of the operation is financial gain through account takeover and fraud. Victims are typically guided to perform actions such as logging in to bank portals or entering payment details while the attacker monitors in real time.
Once credentials are exposed, funds can be transferred or stolen with minimal resistance. In some observed cases, malware payloads were deployed after initial access to maintain persistence on compromised systems.
This campaign demonstrates an evolving trend in phishing operations leveraging legitimate, trusted cloud and customer support ecosystems to bypass traditional security filters.
Cloudflare Pages and Zendesk domains are often whitelisted by corporate firewalls, giving attackers an advantage in avoiding detection.
Security analysts recommend that users verify domain names carefully before entering sensitive information, avoid installing remote-control tools on unsolicited instructions, and report suspicious “support chat” interactions immediately.
Organizations using Cloudflare and Zendesk should implement automated monitoring for typosquatting activity targeting their brand names and enforce stricter verification for customers onboarding.
As these hybrid social engineering schemes continue to combine AI-generated content with real-time attacker engagement, the boundary between legitimate support and fraud grows harder to detect, underscoring the importance of vigilance and domain-level threat intelligence.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates