Seqrite Labs’ APT team has uncovered an extended cyber-espionage campaign linked to the Kazakhstan-based threat actor Silent Lynx.
The group, initially identified by Seqrite researchers in late 2024, continues to evolve its operations, targeting diplomatic and government entities across Central Asia, Russia, and China through spear‑phishing and malicious archives.
New Campaigns and Geopolitical Motives
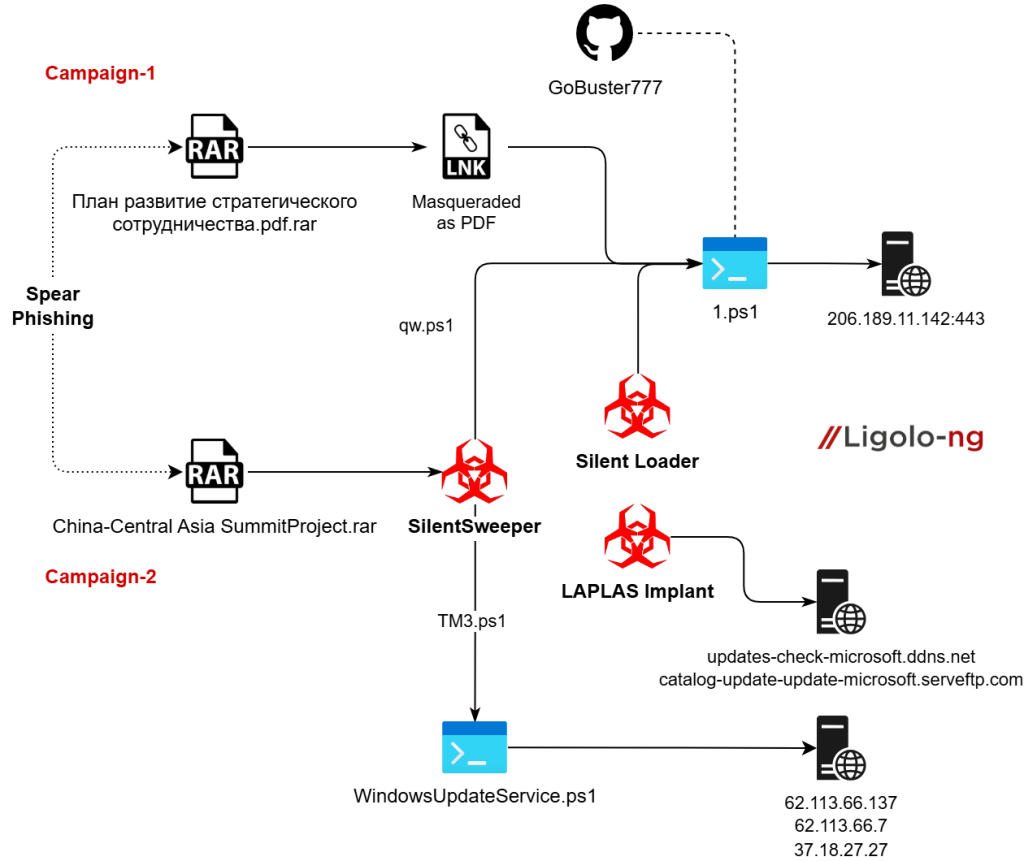
The latest research, internally referred to as Operation Peek‑A‑Baku, reveals multiple campaigns running between June and October 2025. The first, associated with diplomatic cooperation between Russia and Azerbaijan, employed weaponized RAR archives containing malicious LNK shortcuts.
The archive, deceptively titled “Plan for the Development of Strategic Cooperation,” downloaded a PowerShell reverse shell from a GitHub repository named GoBuster777.
Decoded analysis revealed a lightweight TCP‑based reverse shell connecting to the command‑and‑control server at 206.189.11.142:443. The payload executed remote commands, mirrored results to the attacker, and remained persistent via PowerShell-based communication loops.
Alongside this, the actor deployed the open‑source tunneling tool Ligolo‑ng, providing lateral movement and encrypted proxy capabilities across infected hosts.
A secondary campaign targeted China–Central Asia diplomatic channels under the guise of the “China‑Central Asia Summit Project.”
The RAR archive contained the .NET-based implant SilentSweeper, which extracted a PowerShell payload named TM3.ps1 designed to create a Windows scheduled task triggering every six minutes.
This task executed downloaded VBScript and PowerShell scripts responsible for establishing persistence and broader access to compromised devices.
Shared Tooling and Infrastructure Links
Silent Lynx’s evolving toolkit shows substantial overlaps with earlier iterations documented in 2024, particularly the use of C++ loaders such as Silent Loader and TCP-based implants like Laplas.
These implants relied on CreateProcess API calls to spawn PowerShell sessions and connect to remote C2 servers using XOR‑decoded parameters, maintaining a minimal footprint.
Silent Lynx’s persistent use of GitHub‑hosted Base64‑encoded blobs marks a tactical shift from embedding payloads directly within binaries, a move likely inspired by prior research exposure.
Researchers also identified infrastructure shared among campaigns, including IP addresses 62.113.66.137 (Russia) and 206.189.11.142 (Netherlands), used to host exfiltration scripts and payloads.
The recurrence of Golang tunneling utilities such as RESOCKS and Ligolo‑ng highlights the group’s dependence on cross‑platform, low‑cost utilities to sustain command channels.
Espionage Focus and Outlook
Silent Lynx’s continued targeting of government think tanks, ministries, and diplomatic sectors underscores its espionage focus, particularly around events in Dushanbe and Astana.
Seqrite researchers assess with medium to high confidence that the group will continue to leverage double‑stage PowerShell and .NET loaders, GitHub‑hosted payloads, and regional event themes in future infiltration attempts.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates