ESET’s APT Activity Report Q2–Q3 2025 reveals an alarming surge in destructive cyber operations against Ukrainian infrastructure, driven by Russia-aligned threat actor Sandworm.
The campaign, which unfolded between April and September 2025, involved the deployment of new wiper malware families aimed at crippling critical sectors, including energy, logistics, and agriculture.
Destructive Tools: ZEROLOT and Sting
According to ESET telemetry, Sandworm’s most notable operations during the period leveraged two new data wipers, ZEROLOT and Sting, both engineered for maximum disruption rather than data theft.
These wipers overwrite system files, partition data, and boot records, rendering infected machines completely inoperable.
In multiple incidents, wipers were delivered via spearphishing attachments disguised as legitimate financial or procurement documents, exploiting trusted communication channels between supply-chain partners.
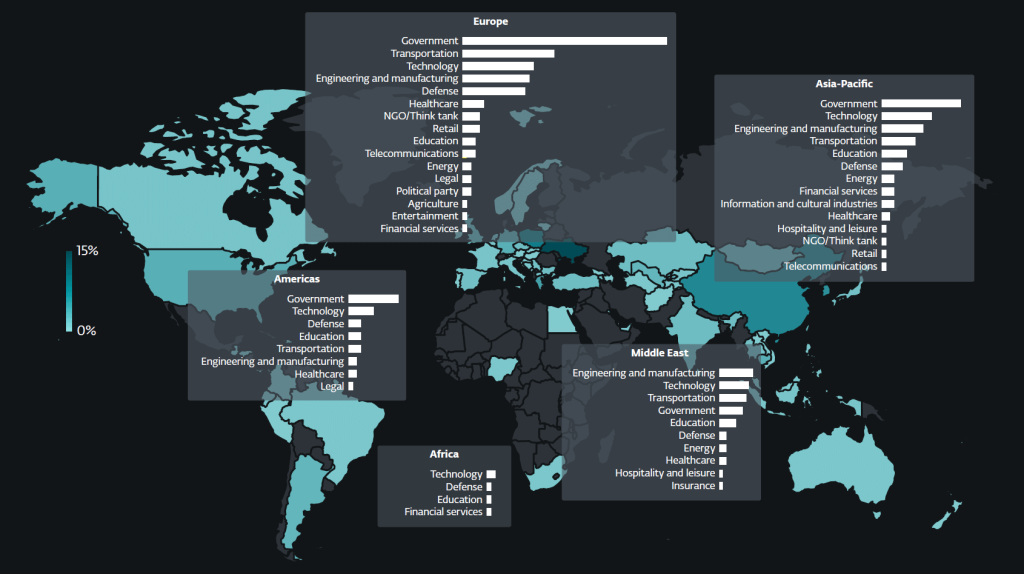
ESET researchers observed that the wipers share structural similarities with NotPetya and Industroyer2, historic Sandworm tools known for inflicting large-scale outages across Ukrainian systems.
The group also used PowerShell-based loaders and remote administration tools to propagate the destructive payloads laterally. Indicators of compromise (IOCs) included modifications to system drivers and persistence achieved through scheduled tasks and registry alterations.
ESET’s analysis indicates that Sandworm likely aimed to disrupt Ukraine’s grain export and energy logistics, undermining economic resilience during wartime.
The wiper attacks coincided with regional escalation events and were carried out hours before official political announcements, suggesting a high degree of operational coordination with strategic motives.
Broader Russian APT Developments
Sandworm’s destructive missions coincided with intensified espionage by other Russia-aligned APT groups, including Gamaredon, RomCom, and Turla. Gamaredon showed increased operational frequency, adopting new file-stealing modules and tunneling services.
At the same time, RomCom exploited a WinRAR zero-day vulnerability to deploy malicious DLLs and deliver multipurpose backdoors targeting European and Canadian sectors. This vulnerability was responsibly disclosed by ESET and patched swiftly.
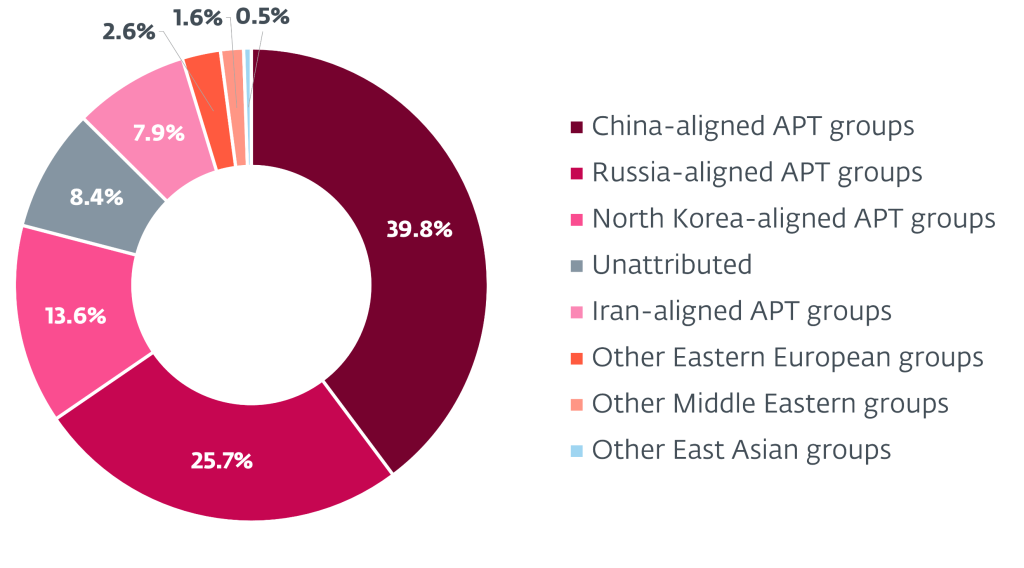
ESET identified rare operational overlaps between Russian APT factions, including Gamaredon’s selective use of one of Turla’s backdoors, indicating a level of inter-group collaboration not previously documented.
This cooperation, alongside Sandworm’s escalated destructive intent, marks a worrying evolution in Russian cyber strategy aimed at both espionage and direct economic sabotage.
ESET has confirmed detection and mitigation of Sandworm’s campaigns across its customer base through integrated telemetry systems.
Their report concludes that the attacks represent a deliberate shift toward destructive cyber operations as a geopolitical weapon, threatening the stability of Ukraine’s critical infrastructure and, by extension, European supply chains.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates