Cybersecurity researchers at Sekoia have uncovered a sophisticated phishing campaign targeting hospitality industry customers worldwide through compromised Booking.com hotel accounts.
The threat actors leverage stolen customer data, including personal identifiers and reservation details, to conduct highly credible banking fraud schemes that have been active since at least April 2025.
The campaign employs a multi-stage attack methodology that begins with malicious emails sent to hotel administrators from compromised corporate email accounts.
These messages impersonate Booking.com communications with subject lines referencing customer requests and tracking codes, such as “New guest message in reference to your unit” and “New last-minute booking” to deceive recipients into believing the correspondence is legitimate.
The emails contain URLs following the pattern hxxps://{randomname}[.]com/[a-z0-9]{4} that redirect victims through a complex infrastructure designed to evade detection.
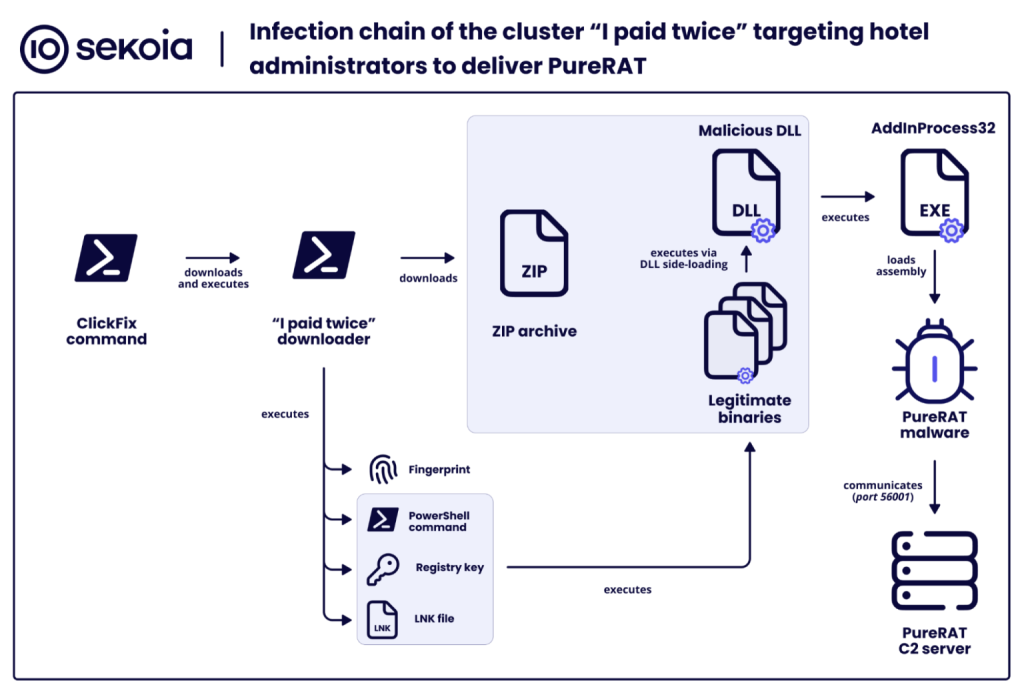
ClickFix Social Engineering Delivers PureRAT Malware
The attack chain uses the ClickFix social engineering tactic, presenting victims with a fake Booking page. Com-branded pages that include admin and extranet URL patterns to enhance legitimacy.
Hotel staff are prompted to copy and execute PowerShell commands disguised as reCAPTCHA verification, which ultimately deploys PureRAT malware on their systems.
PureRAT, also known as PureHVNC and ResolverRAT, is a Remote Access Trojan sold as Malware-as-a-Service by the developer PureCoder since March 2021.
The malware establishes persistence through Windows registry Run keys and communicates over TCP/TLS on ports 56001, 56002, and 56003.
PureRAT implements a modular plugin architecture that enables remote desktop control, keylogging, webcam capture, file exfiltration, and credential theft targeting browser extensions, cryptocurrency wallets, and two-factor authentication applications.
The malware loader employs DLL side-loading and reflective loading techniques via AddInProcess32.exe to execute entirely in memory, without writing to disk, significantly complicating detection efforts.
Cybercrime Ecosystem Fuels Booking Platform Exploitation
Once hotel Booking.com extranet accounts are compromised, threat actors either sell the harvested credentials on cybercrime forums or directly exploit them to send fraudulent payment requests to hotel guests.
Victims receive WhatsApp messages or emails containing legitimate reservation details claiming a security issue occurred during banking verification.
These communications direct customers to phishing pages protected by Cloudflare and hosted on Russian bulletproof hosting infrastructure under AS216341 (OPTIMA LLC) that harvest banking credentials.
Sekoia researchers identified a thriving underground economy supporting these operations on Russian-speaking forums, including LolzTeam, Exploit, and WWHClub.
Services range from hotel administrator email harvesting, starting at $10, to premium Booking.com extranet account logs, priced from $5 to $ 5,000 depending on the number of managed properties and active reservations.
The threat actor moderator_booking claims their team has earned over $20 million from this fraud model, which has expanded to target Expedia, Airbnb, and Agoda platforms.
Sekoia analysts assess with high confidence that this profitable cybercrime ecosystem will continue targeting the hospitality industry through increasingly sophisticated techniques.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates