Cybersecurity researchers from Mandiant have uncovered a critical zero-day vulnerability in Gladinet’s Triofox file-sharing platform.
The flaw, tracked as CVE-2025-12480, was actively exploited by the threat actor group UNC6485 starting August 24, 2025, to bypass authentication and execute malicious code with system-level access.
How the Attack Works
The exploitation involved a two-step process that was remarkably simple yet devastatingly effective. First, attackers manipulated HTTP host headers by setting them to “localhost” in their requests.
This bypassed authentication controls, granting unauthorized access to restricted configuration pages.
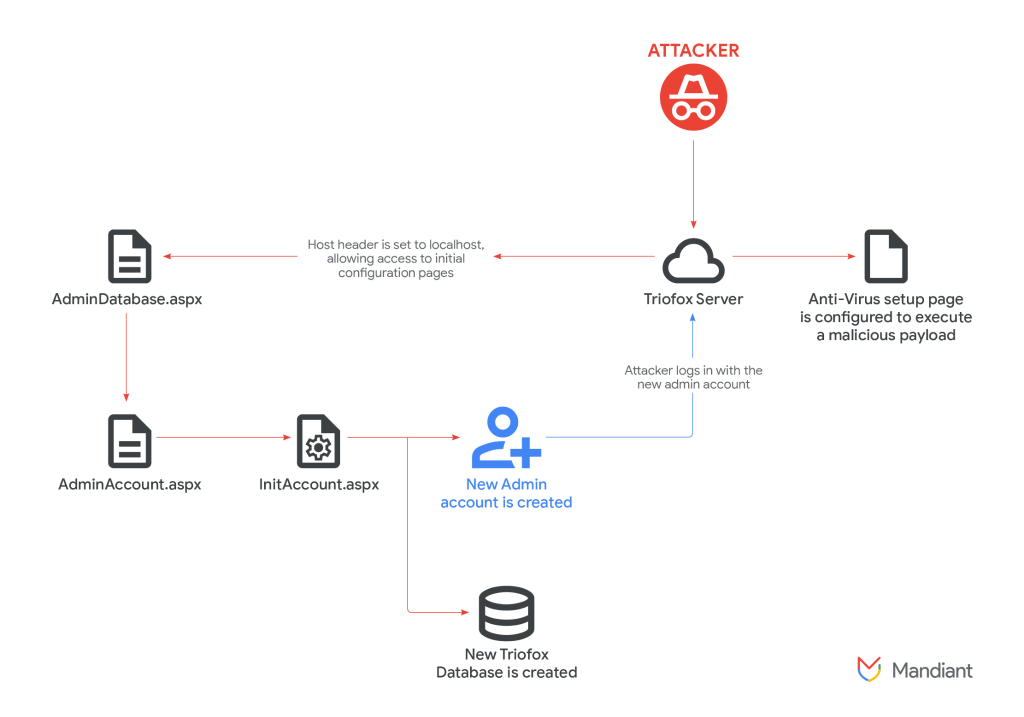
The vulnerability existed in Triofox’s CanRunCriticalPage() function, which incorrectly trusted the host header without validating that requests actually originated from the local system.
This allowed remote attackers to spoof their source IP address.
After gaining initial access, UNC6485 created a new administrator account called “Cluster Admin” through the compromised setup interface.

They then exploited a second weakness in Triofox’s built-in antivirus scanner.
The attackers discovered they could configure the anti-virus scanner path to point to their own malicious batch script instead of legitimate security software.
When files were uploaded to shared folders, Triofox automatically executed the attacker’s payload with full SYSTEM account privileges.
Using this technique, UNC6485 deployed multiple remote access tools, including Zoho Remote Access, AnyDesk, and SSH utilities like Plink and PuTTY.
These enabled encrypted connections to their command-and-control servers for enumeration and privilege escalation attempts.
Mandiant identified the intrusion within 16 minutes using Google Security Operations, spotting suspicious deployments of remote access utilities and unusual file activity in temporary directories.
Security teams noticed anomalous HTTP logs showing external requests with localhost referrer headers.
Companies running Triofox should immediately upgrade to version 16.7.10368.56560 or later.
Security teams should audit all administrator accounts for unauthorized entries, verify anti-virus configurations, and hunt for attacker tools using Mandiant’s detection queries.
Monitoring for unusual outbound SSH traffic can help identify ongoing compromises.
| Attribute | Details |
|---|---|
| CVE ID | CVE-2025-12480 |
| Vendor | Gladinet |
| Product | Triofox |
| Vulnerability Type | Unauthenticated Access Control / Host Header Injection |
| Severity | Critical |
| CVSS Score | 9.8 |
| Affected Versions | 16.4.10317.56372 and earlier |
| Patched Version | 16.7.10368.56560 |
| Threat Actor | UNC6485 |
| Active Exploitation | August 24, 2025 |
Find this Story Interesting! Follow us on Google News, LinkedIn and X to Get More Instant Updates