AhnLab Security Intelligence Center (ASEC) recently uncovered a sophisticated campaign exploiting Remote Monitoring and Management (RMM) tools, specifically LogMeIn Resolve (GoTo Resolve) and PDQ Connect.
Threat actors are using deceptive websites that mimic legitimate download pages for well-known utilities, including Notepad++, 7-Zip, and WinRAR, to lure unsuspecting users.
Once a user downloads and installs what appears to be authentic software, they instead deploy an RMM tool preconfigured to give attackers remote access.
Some of the filenames used to disguise the malicious installer include “notepad++.exe,” “winrar.exe,” “chatgpt.exe,” and “windows12_installer.exe,” among others.
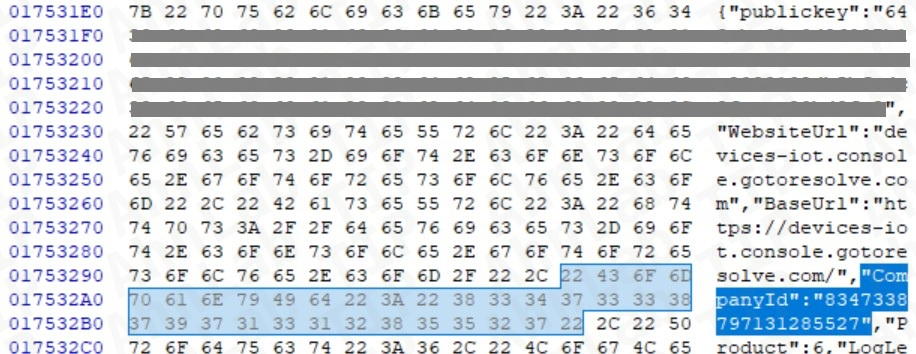
The attackers embed the LogMeIn Resolve client, a legitimate commercial solution for remote IT management, but then configure it.
Hence, the “CompanyId” field ties the install directly to the threat actor’s infrastructure. Analysts identified three distinct CompanyId values associated with these campaigns, allowing visibility into how attackers were structuring their footholds.
From Legitimate Remote Support to Stealthy Backdoor
LogMeIn Resolve and PDQ Connect both offer remote control, patch management, and monitoring capabilities, features vital for IT teams but exploited by attackers to evade antivirus and firewalls.
Once the RMM client is installed under the attacker’s control, the attacker can execute PowerShell commands and deploy their primary payload: PatoRAT.
PatoRAT is a Delphi-based backdoor with extensive remote-control and surveillance capabilities. Its configuration is stored in a XOR-encrypted resource and includes details such as client tags, mutex names, and lists of command-and-control (C&C) servers.
Debug strings and portions of the code are written in Portuguese, suggesting possible regional development or operational links.
Upon execution, PatoRAT exfiltrates system details, CPU and OS info, user credentials, location data, and live memory stats to its C&C servers.
It supports keyboard logging, screen captures, browser credential theft, and remote desktop access. Additional features include mouse and clipboard control, plugin delivery, QR code scanning, and port forwarding mechanisms.
Defensive Measures and Recommendations
These campaigns highlight the growing trend of attackers abusing legitimate remote administration tools rather than traditional malware, thereby bypassing standard security controls.
ASEC advises users to verify software sources by only downloading from official vendor sites and checking digital signatures. Organizations should monitor for suspicious RMM tool installations and regularly update operating systems and security software.
The technical sophistication of this campaign, leveraging trusted IT software as both delivery vector and remote access backdoor, underscores the importance of vigilant software sourcing and multi-layered threat detection strategies.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates