Researchers have identified continued activity from the SmartApeSG campaign, now using the ClickFix-style fake CAPTCHA attack vector to deliver NetSupport RAT payloads.
Also known by aliases such as ZPHP or HANEYMANEY, the campaign first surfaced in mid-2024, initially distributing its malware through spoofed browser update pages.
In its latest evolution, SmartApeSG has adopted a more convincing CAPTCHA-style deception that abuses user trust to trigger malware execution manually.
Evasion Through Interactive Deception
The SmartApeSG attack sequence originates from compromised websites where a hidden SmartApeSG JavaScript is injected into standard web pages. When activated under specific conditions, such as particular IP geolocation or browsing patterns, victims are presented with a “verify you are human” page that mimics legitimate CAPTCHA challenges.
Once the user clicks the verification box, malicious code quietly injects a command string into the clipboard while displaying a pop-up that instructs the user to open the Windows Run dialog and paste the command.
The injected command leverages the Windows mshta utility to fetch and execute a remote payload, initiating the infection chain.
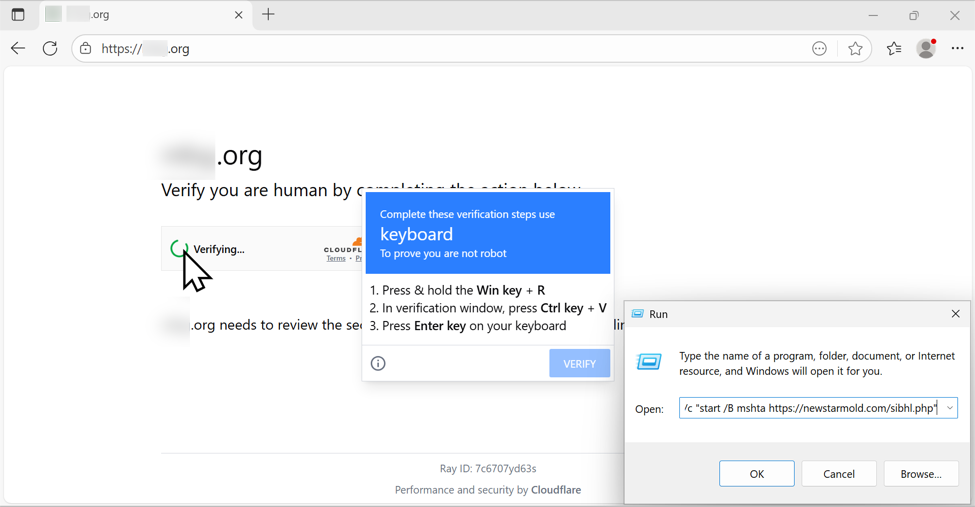
Captured traffic from observed infections shows communications with domains such as frostshiledr[.]com newstarmold[.]com, hosting intermediate scripts and malicious components.
The final stage retrieves a ZIP archive containing the NetSupport RAT remote administration tool from hxxps[:]//www.iconconsultants[.]com/4nnjson.zip, a 9.1 MB file (SHA256: 1e9a1be5611927c22a8c934f0fdd716811e0c93256b4ee784fadd9daaf2459a1).
Persistence and Command Control
The NetSupport RAT drops its executable into C:\ProgramData\ and establishes persistence by creating a Windows Start Menu shortcut that runs a corresponding JavaScript loader from the user’s AppData\Local\Temp directory.
Subsequent network activity reveals encrypted outbound connections to 194.180.191[.]121 over TCP port 443, functioning as the campaign’s current command-and-control (C2) infrastructure.
These infection chains exhibit notable operational discipline, with attackers rotating domains and C2 endpoints almost daily to hinder tracking and takedown. When successful, the RAT grants remote access capabilities allowing adversaries to spy on users, exfiltrate data, or stage secondary payloads.
Monitoring by security researchers and the Mastodon account “Monitor SG” continues to reveal clusters of SmartApeSG-linked indicators. Analysts often rely on repositories such as URLscan.io to pivot and identify additional compromised sites tied to this activity.
The SmartApeSG campaign demonstrates the growing fusion of social engineering and technical exploitation.
By offloading execution to users through interactive deception, campaigns like this successfully bypass traditional automated detections, underscoring the importance of user awareness and continuous domain monitoring within enterprise threat defenses.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates