Active Directory (AD) holds the digital keys to an organization’s network. Threat actors targeting the NTDS.dit file, which contains hashed credentials and critical domain data, can achieve full domain compromise if they succeed.
This article walks through a real-world scenario where attackers dumped and exfiltrated NTDS.dit, bypassing common defenses, and highlights how Trellix Network Detection and Response (NDR) detects these stealthy movements through behavioral, protocol, and exfiltration pattern analysis.
One File, Total Access: The Risk of Losing NTDS.dit
In Windows domains, AD serves as the central authority for authentication and authorization.
The NTDS.dit database houses user accounts, group policies, computer objects, and password hashes for all domain users, including Domain Administrators.
With SYSTEM hive access for decryption, adversaries can extract and crack these hashes offline, granting them unfettered access without phishing or brute-force attacks.
Attackers often use built-in tools vssadmin to create Volume Shadow Copies, bypassing file locks on NTDS.dit.
They then repair the snapshot esentutl and dump credentials via utilities such as Mimikatz or SecretsDump, all while avoiding traditional signature-based detections.
Attack Chain Overview
Illustrates the full kill chain from initial compromise through NTDS. This exfiltration shows how Trellix NDR intervenes at each stage.
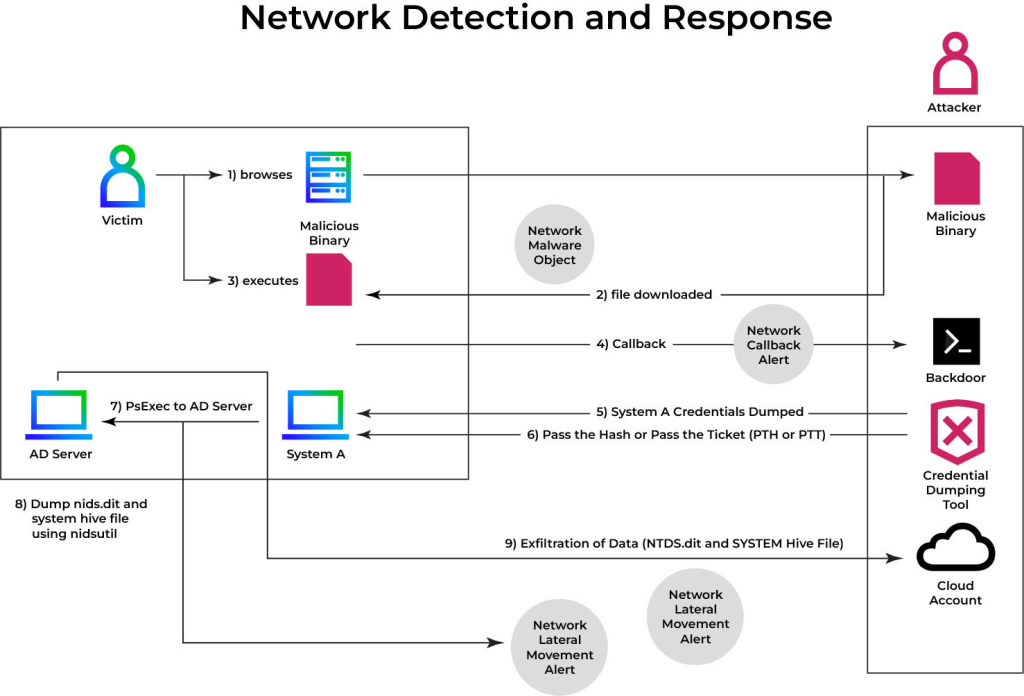
Step 1: Steal Password Hashes
After gaining network access, the attacker extracts password hashes from lsass.exe memory using Mimikatz or by leveraging DCSync.
These hashes facilitate offline password cracking and pass-the-hash techniques.
Step 2: Pass-the-Hash Authentication
With a stolen hash, the attacker authenticates as a privileged user via NTLM using Mimikatz, issuing commands like:
text/user:<username> /domain:<FQDN> /ntlm:<hash>
Step 3: Lateral Movement
Armed with elevated credentials, adversaries deploy PSExec to run commands on remote systems, extending their foothold and repeating credential theft on additional hosts.
Step 4: Dump and Exfiltrate NTDS.dit
On a domain controller, attackers create shadow copies or use DSDBUtil/NTDSUtil to extract NTDS.dit and the SYSTEM hive. After verifying extraction, they archive the files for stealthy exfiltration.
Detection with Trellix NDR
Trellix NDR flags these activities using two primary alert categories:
- Suspicious SMB Traffic and Shadow Copy Creation: Behavioral detection spots anomalous VSS and SMB operations indicative of NTDS.dit extraction.
- High-Fidelity Exfiltration Signatures: Custom signatures detect large, unusual transfers of .dit and registry hive files.
Trellix Wise, the AI assistant within Trellix NDR, automates alert triage, reduces false positives, and accelerates incident response by linking attacker IPs, tactics, and detection points in a unified knowledge graph.
The theft of NTDS.dit is a complete compromise of an Active Directory domain. Native tools and stealthy techniques make it easy for attackers to evade legacy defenses.
Trellix NDR’s combination of behavioral analytics, protocol anomaly monitoring, and AI-driven correlation transforms detection and response, ensuring defenders can thwart identity-based attacks before irreversible damage occurs.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates