Since late August, Trend™ Research has identified a global surge of malware posing as legitimate AI and productivity applications.
Dubbed EvilAI, this campaign deploys trojans disguised behind realistic interfaces, functional features, and even valid code-signing certificates to infiltrate corporate and personal systems without triggering suspicion.
The rapid proliferation of 56 incidents in Europe and 29 each in the Americas and AMEA underscores the threat’s scope and sophistication.
Sophisticated Masquerade and Persistent Access
EvilAI installers masquerade under generic yet plausible names such as App Suite, Recipe Lister, and PDF Editor, offering bona fide utility features that match user expectations.
Upon installation, these applications present fully functioning UI elements such as document handling, recipe management, or AI-enhanced browsing while silently dropping a malicious JavaScript payload.
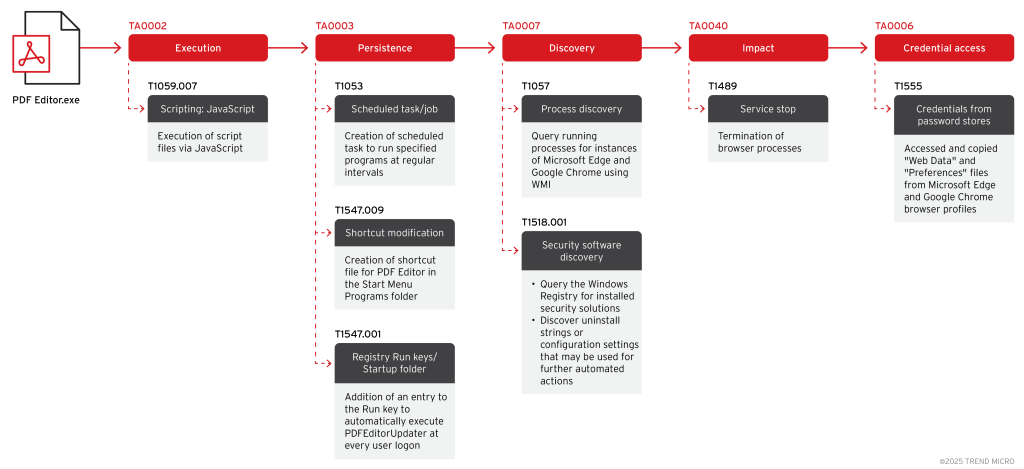
The payload resides in the user’s Temp folder (e.g., %LOCALAPPDATA%\Temp\{GUID}or.js) and is executed via Node.js (node.exe) launched in minimized mode.
This covert execution chain—invoked through cmd.exe /c start "" /min ensures that the legitimate window remains in the foreground as the trojan activates in the background.
To cement persistence, EvilAI creates a scheduled task named sys_component_health_{UID}, configured to run every four hours and daily at 10:51 AM. It also adds a Start Menu shortcut and writes an PDFEditorUpdater entry in the Windows Registry Run key.
These mechanisms guarantee re-execution even after reboots, allowing the malware to maintain a foothold over extended periods.
AI-Driven Evasion and Data Exfiltration
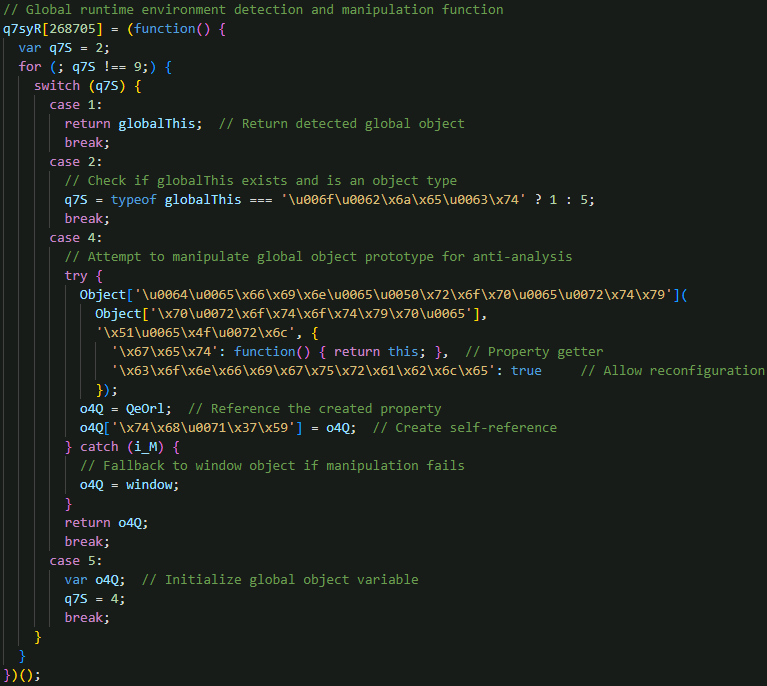
EvilAI’s operators leverage large language models to generate clean, static-analyzer-friendly JavaScript code, effectively evading signature-based AV scanners.
Control-flow flattening, Unicode-escaped strings, MurmurHash3-based anti-analysis loops, and self-cleaning routines conceal the trojan’s actual operations.
Each obfuscated loop computes a hash on its counter and magic constants to thwart static inspection, dynamically constructing critical strings only at runtime.
Once active, EvilAI enumerates running browser processes via WMI queries (Get-WmiObject Win32_Process) and inspects registry uninstall strings to detect installed security products.
It then forcibly terminates Chrome and Edge using taskkill, duplicates of “Web Data” and “Preferences” files from browser profiles—appending “Sync” to exfiltration copies and storing them alongside the originals.
This method yields cookies, autofill data, and authentication tokens without alerting users.
All communications with EvilAI’s C&C infrastructure are encrypted using AES-256-CBC, with session keys derived from the malware’s unique instance ID (UUID).
The Trojan constructs JSON payloads containing progress identifiers and timestamps, encrypts them with IVs prepended, and encodes the output in Base64. Responses follow the same decryption routine, enabling remote command execution for file operations, registry modifications, and process launches.
Early telemetry indicates that India (74 cases), the United States (68), and France (58) are most affected, with critical sectors such as manufacturing (58), government (51), and healthcare (48) experiencing significant infections.
As EvilAI continues to evolve, defenders must adapt by monitoring anomalous Node.js activity, scheduled task creations, and AI-style code obfuscation patterns to detect and disrupt this stealthy, AI-empowered trojan.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates