Security researchers have uncovered a sophisticated cryptocurrency wallet drainer masquerading as a legitimate NPM package, marking a concerning evolution in cybercrime where threat actors are leveraging artificial intelligence to create more convincing malware.
The malicious package @kodane/patch-manager, which accumulated over 1,500 downloads in just two days, demonstrates how AI is being weaponized to craft professional-looking code that can deceive even experienced developers.

Sophisticated Stealth Operations
The malware presents itself as an “NPM Registry Cache Manager” with seemingly legitimate functionality for license validation and registry optimization.
However, beneath this facade lies what the author brazenly calls an “ENHANCED STEALTH WALLET DRAINER” in the package’s own documentation.
Upon installation, the package executes a post-install script that strategically places malicious files in hidden directories designed to mimic legitimate cache folders across different operating systems.
The malware establishes persistence through a background process called connection-pool.js, which connects to a command-and-control server at https://sweeper-monitor-production.up.railway.app.
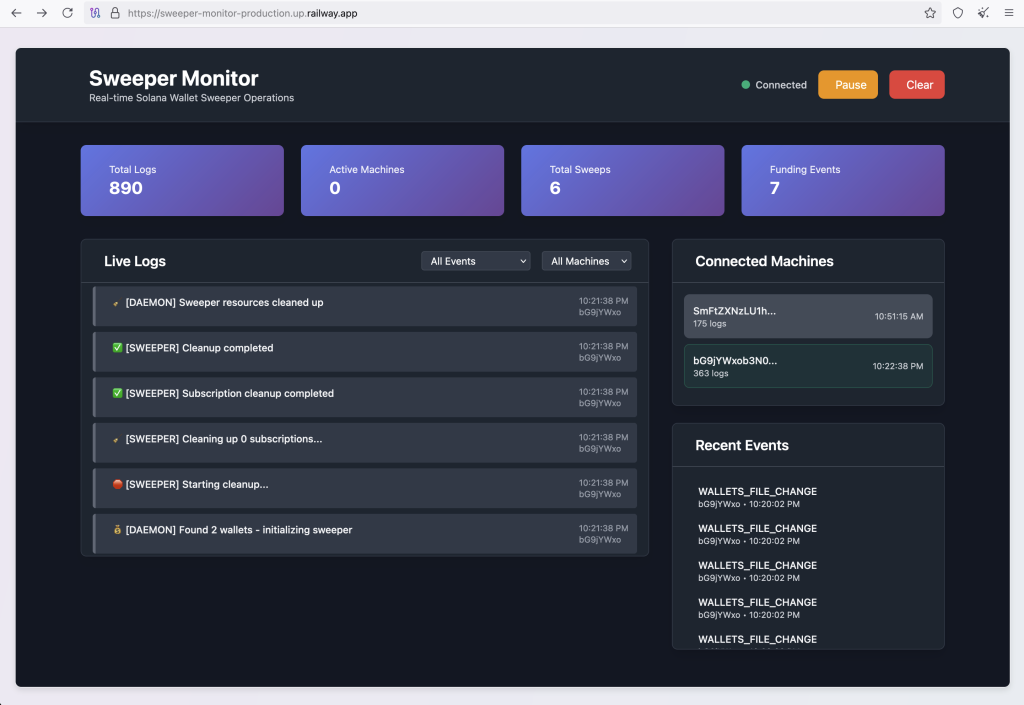
According to the report, This C2 infrastructure generates unique machine identifiers for compromised hosts and has been observed managing multiple infected systems simultaneously.
When cryptocurrency wallet files are detected, the malware activates its transaction-cache.js component, which drains funds while cleverly leaving enough balance to cover transfer fees, sending stolen assets to a hardcoded Solana address: B2XwbrGSXs3LAAcqFqKqGUug5TFA1Bug2NNGH3F3mWNK.
Clear Signs of AI Generation
Multiple indicators suggest this malware was generated using AI tools, remarkably resembling output from platforms like Claude.
The code contains excessive emojis in source files, abundant console.log messages with detailed explanations, and unusually comprehensive comments written in perfect English – patterns rarely seen in human-authored malware.
The README.md file follows typical AI-generated markdown structures with consistent indentation and numerous inline code examples.

Most tellingly, the malware’s self-designation as “Enhanced” aligns with AI tools’ tendency to label any code modification as an enhancement.
Rapid Response and Protection
Published initially on July 28, 2025, by an author using the NPM username “Kodane,” the package saw 19 different versions released over two days before NPM flagged it as malicious on July 30th.
The threat actor’s operational security suggests possible origins from UTC +5 timezone countries, potentially Russia, China, or India.
This incident highlights critical gaps in current security tools, as traditional Software Composition Analysis (SCA) and Endpoint Detection and Response (EDR) solutions lack capabilities to detect JavaScript-based malware.
Organizations must implement specialized package firewall solutions and maintain vigilance against increasingly sophisticated AI-generated threats targeting the software supply chain.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates