Since January, Trend Micro has identified a surge in phishing campaigns that exploit AI-driven development platforms, Lovable: app, Netlify: app, and Vercel: app to host counterfeit CAPTCHA challenge pages.
Attackers capitalize on the free hosting tiers, rapid deployment pipelines, and the inherent credibility of these domains to stage sophisticated ruses that bypass automated scanners.
Initial lures arrive via phishing emails bearing urgent themes such as “Password Reset Required” or “USPS Change of Address Notification.” When recipients click the embedded links, they encounter a fully functional-looking CAPTCHA widget generated through AI-assisted tooling.
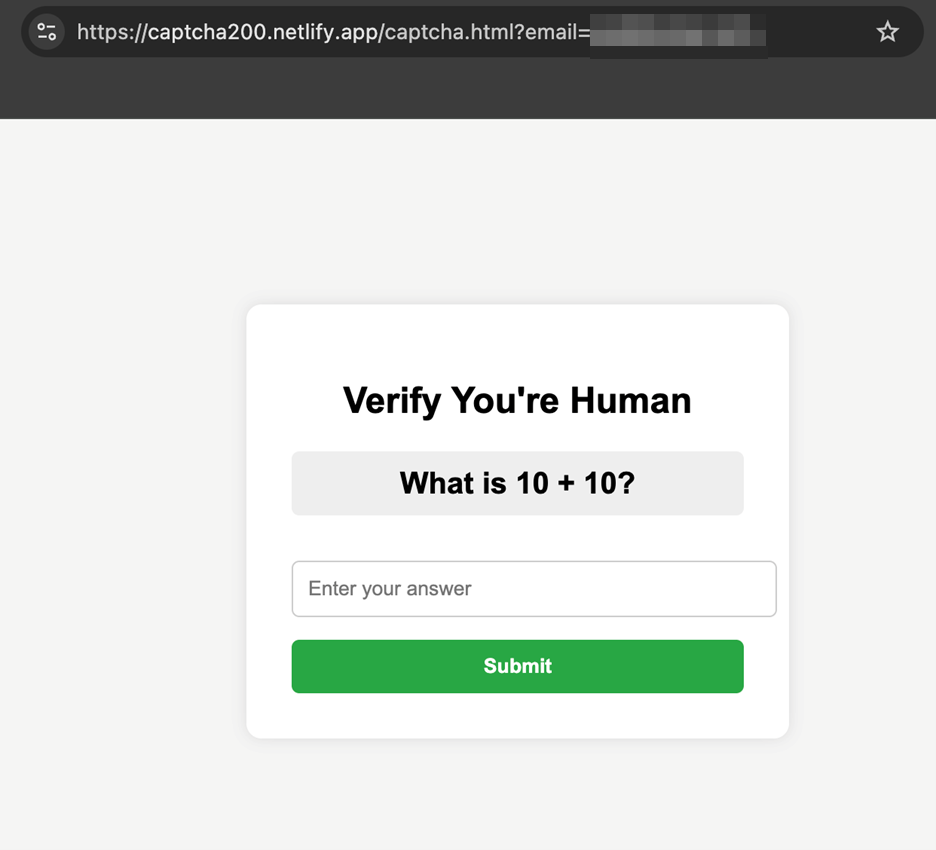
This CAPTCHA interface performs two critical functions: it lowers user suspicion by framing the interaction as a routine security measure and thwarts detection by security crawlers that only index the challenge page rather than the hidden phishing payload.
Upon successful completion of the CAPTCHA, client-side scripts silently redirect the user to the actual credential-harvesting site, where victims are prompted to enter login information for services like Microsoft 365, Google Workspace, and corporate VPN portals.
Failed attempts reload the challenge, further obfuscating the malicious intent. Trend Micro telemetry shows distribution across platforms: Vercel.app hosts 52 unique phishing sites, Lovable.app hosts 43, and Netlify.app hosts 3.
Activity ramped up significantly between February and April, coinciding with the increased adoption of remote work, then dipped before experiencing a renewed spike in August.
Defensive Measures and User Training Imperatives
Organizations must enhance their security posture to counter CAPTCHA-based phishing tactics. Traditional static URL blacklists and simple page inspections are insufficient against these dynamic redirects.
Instead, defenders should deploy email security gateways with advanced link sandboxing, capable of unpacking redirect chains and performing behavior-based analysis.
Web proxies and secure web gateways must be configured to detect and flag abnormal traffic patterns on trusted hosting domains, while integrating real-time threat intelligence feeds that monitor subdomain registrations across Lovable: app, Netlify: app, and Vercel: app for proactive takedown requests.

Equally vital is comprehensive user education. Employees require training to recognize suspicious CAPTCHA prompts and verify the authenticity of domain URLs, particularly those related to AI development platforms.
Encouraging the use of password managers adds a safeguard, as autofill will fail on unfamiliar phishing domains. Incident reporting procedures should be streamlined to ensure rapid response when a phishing attempt is detected.
As AI-powered web development platforms continue to democratize site creation, defenders must anticipate adversarial misuse.
By combining layered technical controls with informed user vigilance, organizations can mitigate the deceptive lure of fake CAPTCHA schemes and protect critical credentials and sensitive data.
Indicators of Compromise
- captcha200[.]netlify.app
- adobepdfonlinereadercaptcharobot[.]netlify.app
- captchaweb3[.]netlify.app
- basvursana2025hemen[.]vercel.app
- web-orpin-xi[.]vercel.app
- web-pnrf[.]vercel.app
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates