Researchers at Palo Alto Networks’ Unit 42 have uncovered a sophisticated malware family, Airstalk, deployed as part of a suspected nation-state operation tracked under the cluster CL-STA-1009.
The malware, written in both PowerShell and .NET, appears to have been used in a likely supply chain attack targeting business process outsourcing (BPO) providers and managed service entities.
Airstalk abuses VMware’s AirWatch Mobile Device Management (now Workspace ONE UEM) API to establish covert command-and-control (C2) communications.
By exploiting legitimate AirWatch endpoints and device attribute functionality, the malware bypasses typical security monitoring and blends into trusted enterprise traffic. Some samples were even signed with a likely stolen digital certificate to evade detection.
Abusing AirWatch’s MDM API for Covert C2
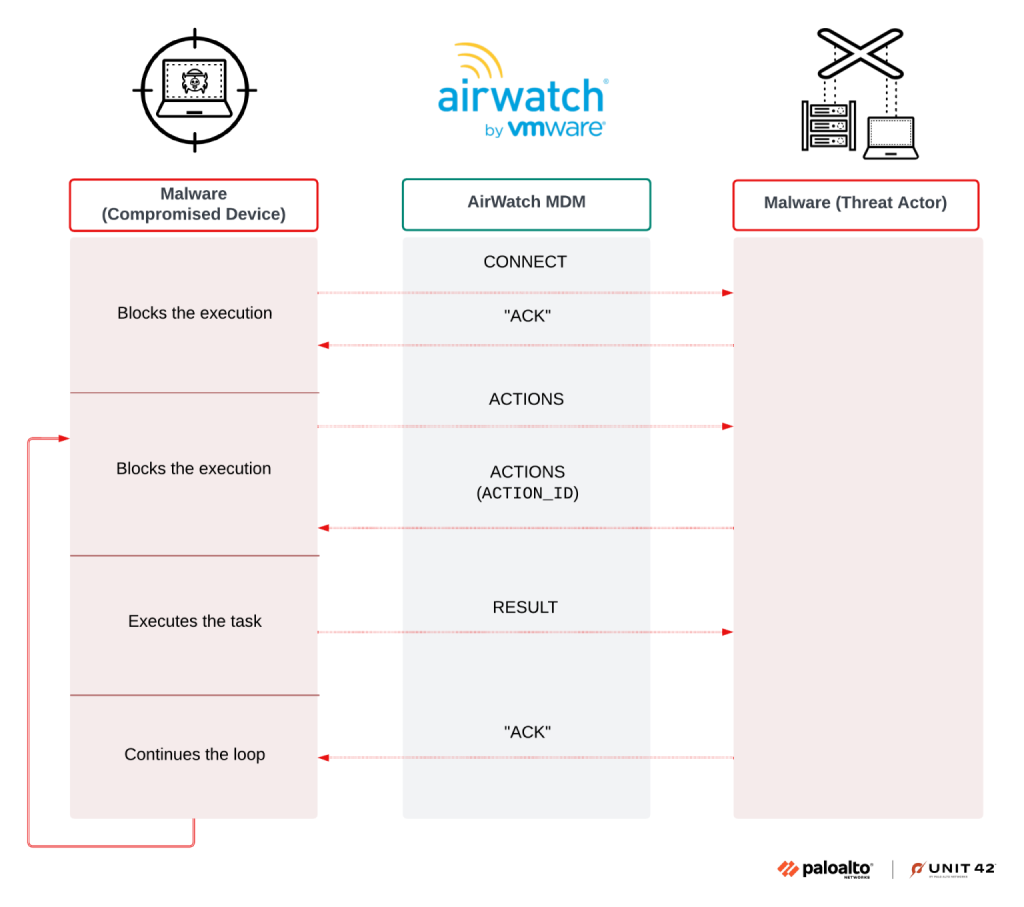
The PowerShell variant of Airstalk communicates over the AirWatch MDM API at /api/mdm/devices/, using custom device attributes as a covert “dead drop” to exchange encrypted C2 messages. Each message is Base64-serialized and includes UUIDs that uniquely identify compromised systems.
Additional uploads, such as screenshots or stolen data, are sent via the /api/mam/blobs/uploadblob endpoint, effectively disguising exfiltration as legitimate MDM traffic.
The C2 protocol uses distinct message types, such as CONNECT, CONNECTED, ACTIONS, and RESULT, to coordinate tasks. Once communication is established, Airstalk executes commands ranging from file enumeration and Chrome cookie theft to screenshot capture.
Table analysis revealed several unimplemented tasks, implying the malware’s modular structure and ongoing development.
.NET Variant Expands Capabilities and Targets
The .NET version of Airstalk demonstrates greater sophistication, adding support for additional browsers such as Microsoft Edge and Island Browser.
This version integrates three concurrent threads for C2 tasking, beaconing, and debugging. New message types MISMATCH, DEBUG, and PING enable version tracking and keep-alive communications.
Supported tasks include data theft from Chrome and Island Browser profiles, retrieving bookmarks, listing files, capturing screenshots, and opening arbitrary URLs.
The malware uses structured suffixes such as “-kb,” “-kr,” and “-kd” in UUIDs to denote communication types, indicating a deliberate, organized C2 protocol design.
Signed with a revoked certificate issued to a Chinese firm, Aoteng Industrial Automation (Langfang) Co., Ltd., and timestamped between June and November 2024, Airstalk displays characteristics consistent with advanced persistent threat operations.
Unit 42 assesses with medium confidence that CL-STA-1009 represents a nation-state campaign leveraging trusted MDM infrastructure to exfiltrate browser data and sensitive user information.
The targeting of third-party managed services and outsourcing providers underscores the growing appeal of BPO entities as high-value entry points for supply chain compromise.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates