A financially motivated cybercrime group has spent the past year targeting Indonesian and Vietnamese Android users by deploying banking trojans disguised as official government identity and payment applications.
By spoofing Google Play Store and App Store interfaces and delivering malicious APKs through obfuscated WebSocket connections, the operators have evaded traditional network security measures and automated scanners.
Analysis of more than 100 malicious domains reveals consistent use of Alibaba ISP, Gname.com registration, and share-dns.net nameservers. In contrast, domain registrations rapidly transition to active DNS resolutions, often within 10.5 hours, during the daytime hours in Eastern Asia.
Sophisticated WebSocket-Based Delivery
The group’s hallmark delivery mechanism utilizes the Socket.IO library to establish real-time, bidirectional WebSocket connections, rather than relying on simple HTTP downloads.
On sites such as icrossingappxyz[.]com, which features fake download buttons for Google Play and App Store, clicking the Android icon triggers a socket.emit('startDownload',…) event.
The server then streams the malicious APK in numerous small chunks via socket.on('chunk',…) handlers, all while updating an on-page progress bar through downloadProgress messages.
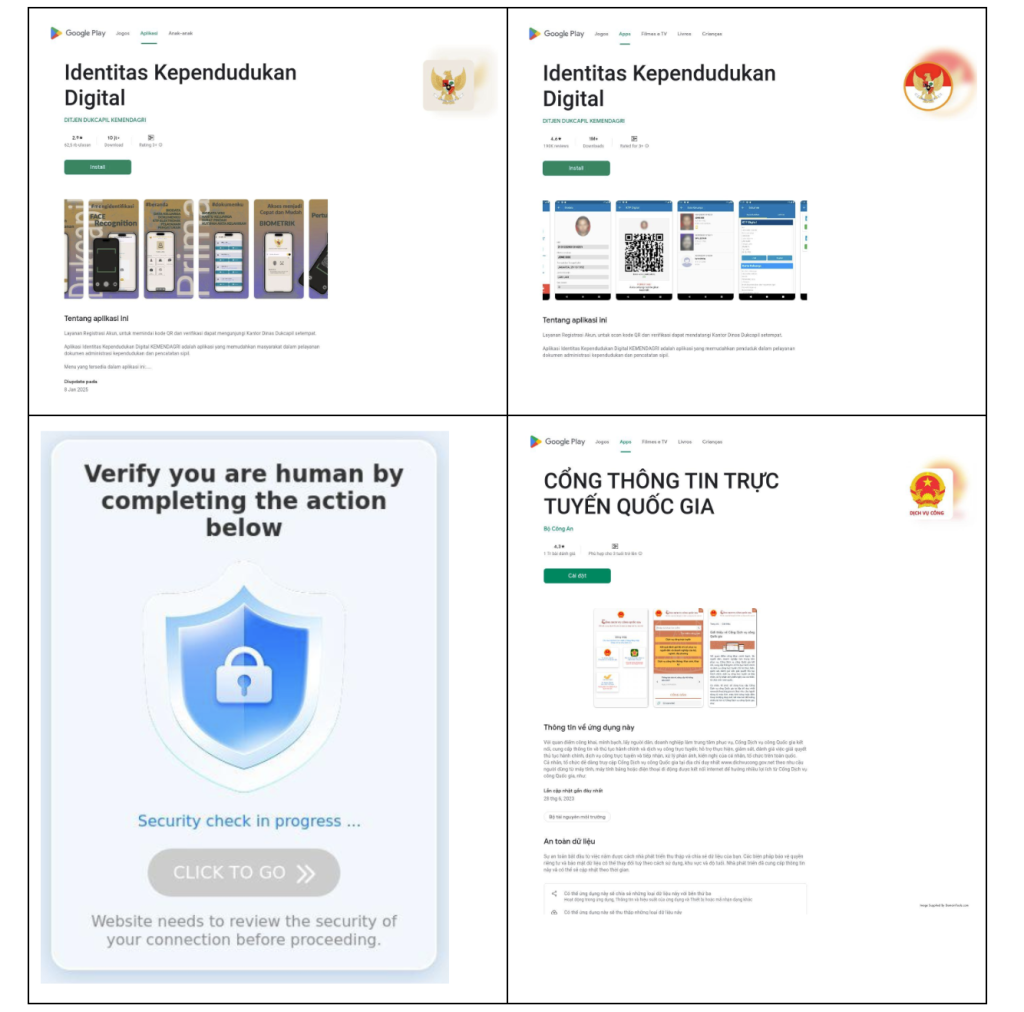
Once complete, the script aggregates chunks in memory, sets the MIME type to application/vnd.android.package-archive, and programmatically initiates a hidden anchor element to prompt the user’s download dialog.
This method circumvents firewalls configured to block direct .apk URLs and thwart static crawlers that scan for malicious links.
The downloaded file, commonly named IdentitasKependudukanDigital.apk (SHA-256: 1f9253092c5a2abdb7bc3d93fccad85f23ce5bfde38377c792a242f045afcdb5), installs a variant of the BankBot trojan family first leaked in 2016.
Some browsers detect the anomalous download and display security warnings, but many users proceed unaware of the malware’s true nature.
Simpler spoofed sites, such as twmlwcs[.]cc, hosting M-Pajak.apk (SHA-256: e9d3f6211d4ebbe0c5c564b234903fbf5a0dd3f531b518e13ef0dcc8bedc4a6d), offer direct download links, often with mixed Thai, Vietnamese, Portuguese, and Indonesian code strings, indicating the use of multilingual templates by less sophisticated actors.
Infrastructure Patterns Reveal Operational Footprint
Domain registration data spanning August 2024 to September 2025 highlights distinctive operational behaviors. The threat actors repeatedly reuse TLS certificates across pairs of domains and cluster dozens of spoofed sites on identical IP addresses predominantly hosted via Alibaba and Scloud.
Registered through Gname.com Pte. Ltd. and using share-dns[.]Alongside Cloudflare nameservers, these domains often share the server title “Identitas Kependudukan Digital – Apps on Google Play” and run on Nginx.
First-seen DNS queries closely mirror domain registration times, with an average 10.5-hour lag, signaling swift deployment.
Open directory listings on domains like dgpyynxzb[.]com and ykkadm[.]ICU hosts multiple APK variants ranging from BRI-JR to OCBCmobileid, each file accompanied by its SHA-256 hash.
Infections are configured to phone home to C2 domains such as saping. ynhqhu[.]com and admin. congdichvucongdancuquocgia[.]cc, further underscoring a coordinated infrastructure.
This campaign highlights the importance of behavioral detection and real-time traffic inspection in identifying anomalous WebSocket file transfers.
End-user warnings remain a critical defense layer; however, network defenders must enhance their monitoring of TLS certificates, DNS registration patterns, and IP clustering to disrupt these malicious operations.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates