A sophisticated Android banking Trojan named Herodotus has emerged on the mobile threat landscape, demonstrating advanced techniques to evade behavioral biometrics detection by artificially simulating human interaction patterns during remote-control fraud sessions.
ThreatFabric’s Mobile Threat Intelligence service identified malware distributed alongside established threats such as Hook and Octo, marking a significant evolution in device-takeover banking malware capabilities.
Herodotus combines components from the previously discovered Brokewell banking Trojan with novel functionality designed to perform credential theft and account takeover attacks.
The threat is already being offered as Malware-as-a-Service by its developer, identified as “K1R0,” on underground forums, indicating widespread commercial adoption despite the malware still being in active development stages.
Humanizing Fraud Through Behavioral Mimicry
The defining technical characteristic of Herodotus lies in its sophisticated approach to mimicking legitimate user behavior during automated transactions.
Unlike traditional banking Trojans that execute commands at machine speed, Herodotus deliberately introduces randomized delays between text input events, spacing characters between 300 and 3,000 milliseconds to replicate natural human typing cadence.
This behavioral obfuscation represents one of the first documented instances of a banking Trojan specifically engineered to bypass tempo-based and keystroke-analysis detection systems.
When operators remotely control infected devices, the malware splits operator-specified text into individual characters.
It injects each character with random intervals, preventing detection by rudimentary behavioral systems that measure input timing patterns.
The malware’s command interface includes a checkbox labeled “Delayed text,” which operators can toggle to enable human-mimicry functionality during live fraud sessions.
Beyond text input simulation, Herodotus leverages Accessibility Service abuse to execute remote control commands, including screen clicks, coordinate-based interactions, swipes, and global actions like Home or Back button presses.
The malware displays opaque blocking overlays to the victim while keeping overlays semi-transparent for operators, effectively hiding fraudulent activity during remote takeover sessions.
Active Campaigns and Distribution
ThreatFabric researchers observed active Herodotus campaigns targeting financial institutions in Italy and Brazil, with additional overlay pages identified for institutions in the United States, Turkey, the United Kingdom, and Poland.
The Italian campaign deployed the malware disguised as “Banca Sicura” (Safe Bank), while Brazilian operations used “Modulo Seguranca Stone,” masquerading as a security module for a legitimate payment processor.
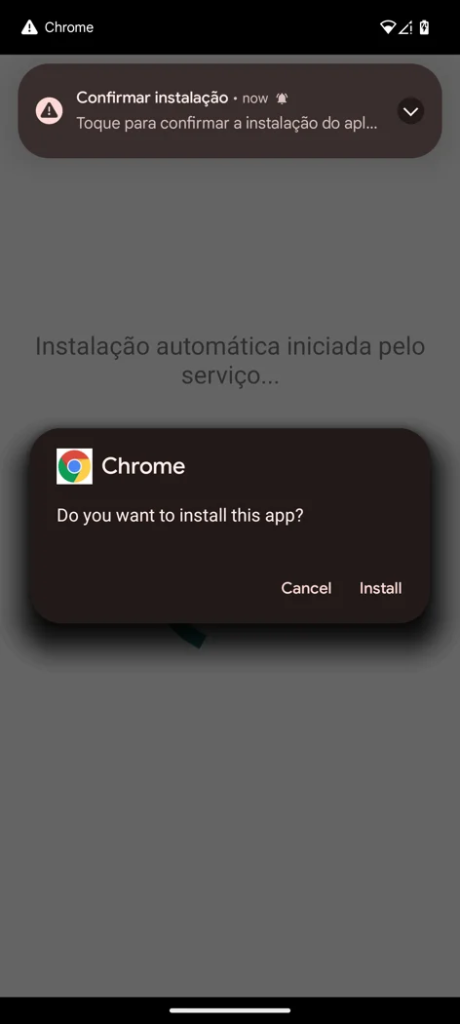
Distribution occurs through side-loading via SMiShing campaigns, directing victims to dropper applications.
The dropper, exclusively written to distribute Herodotus, attempts to install the payload while circumventing Android 13+ Accessibility Service restrictions by opening service settings pages and urging manual enablement.
Once activated, Herodotus queries the command-and-control server for targeted applications and corresponding credential-stealing overlay pages, using the MQTT protocol for communications.
The malware maintains a consistent C2 domain (google-firebase[.]digital) with different subdomains targeting specific regions.
Technical Implications
Financial institutions deploying traditional behavioral detection systems face heightened risks, as Herodotus’ deliberate input randomization may lead to erroneous, lower-risk assessments.
Next-generation behavioral analytics modeling individual user baselines remains effective, while malware classification systems identifying specific variants provide additional defensive value against this emerging threat.
Indicators of Compromise
Sample
| SHA-256 | Package name | Application name | C2 |
| 53ee40353e17d069b7b7783529edda968ad9ae25a0777f6a644b99551b412083 | com.cd3.app | Chrome | gj23j4jg[.]google-firebase[.]digital |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates