In a dramatic turn for digital privacy, over 62,000 user accounts of the notorious Android spyware service Catwatchful were exposed after a security researcher exploited a critical SQL injection vulnerability.
Catwatchful, which openly markets itself as undetectable stalkerware, claims to offer “absolute stealth” for users seeking to monitor devices without consent—a practice widely condemned by cybersecurity experts and privacy advocates.
The breach was discovered by Eric Daigle, a security blogger, who detailed his findings in a comprehensive blog post.
Daigle began by registering a free trial account and analyzing the app’s network traffic.
While most of the sensitive user data was stored securely in Firebase, Daigle found that Catwatchful’s custom backend server, catwatchful.pink, was running an unauthenticated PHP API vulnerable to SQL injection—a flaw that allows attackers to manipulate database queries and extract information.
SQL Injection Flaw Grants Full Access to User Data
Using the automated tool SQLmap, Daigle quickly identified and exploited the vulnerability, gaining access to the entire user database.
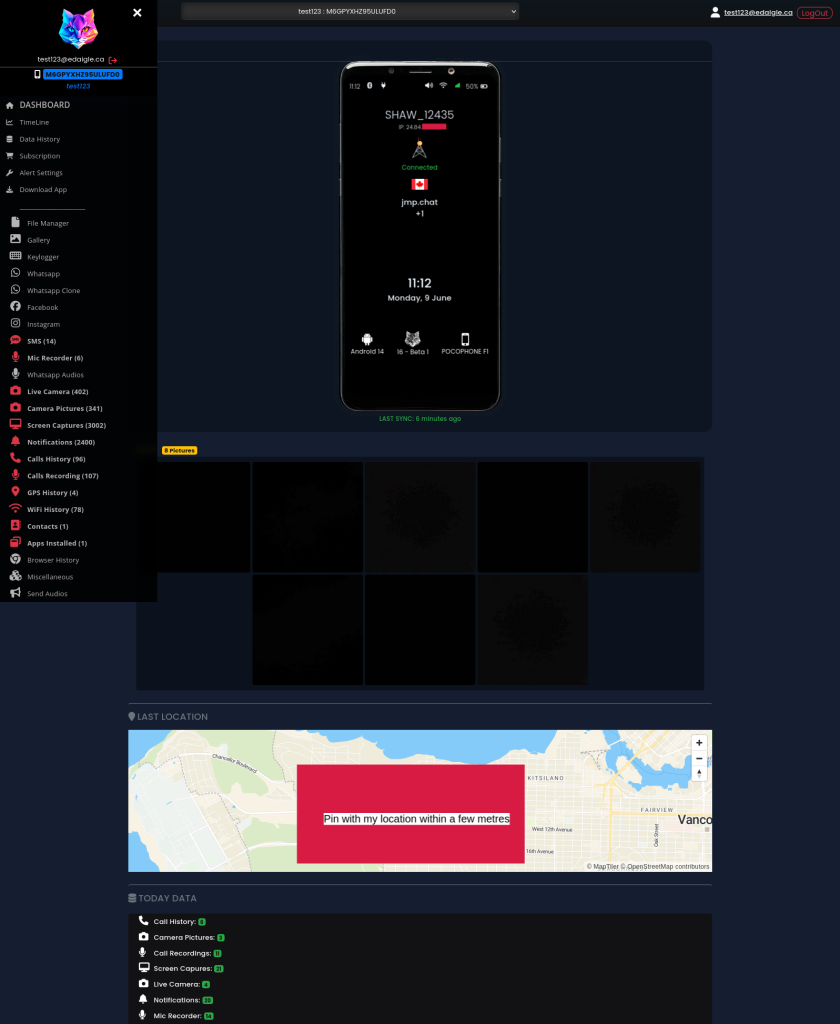
The exposed data included plain-text email addresses and passwords for every account registered with Catwatchful since its inception, over 62,000 in total.
The dump also revealed device associations and administrative records.
The implications are severe: attackers could use this information to hijack accounts, access private surveillance data, and potentially identify both stalkers and their victims.
Daigle coordinated with journalist Zack Whittaker, who alerted Google and the service’s hosting provider.
The original domain was taken offline, but the operators briefly relaunched the service under a new domain, which remained vulnerable until a web application firewall was deployed.
Aftermath and Industry Response
The breach highlights ongoing risks posed by stalkerware apps, which often operate in legal and ethical gray areas.
While Catwatchful’s operators have attempted to restore service, the exposure of their entire user base may lead to further legal and regulatory scrutiny.
Security experts urge users to avoid such surveillance tools and recommend regular device security checks.
The incident also underscores the importance of secure coding practices, particularly for services handling sensitive personal data.
For more details and technical analysis, read Eric Daigle’s original blog post.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates