A new information-stealing malware called Anivia Stealer has emerged in the underground cybercrime marketplace, promoted by threat actor ZeroTrace.
The Windows infostealer, based on C++17 features, has advanced capabilities, including User Account Control (UAC) bypass mechanisms and automatic privilege escalation, raising significant concerns among cybersecurity professionals.
The malware is actively marketed through dark web channels and cybercrime forums, with subscription-based pricing ranging from €120 for 1 month to €680 for lifetime access.
Security researchers note that Anivia Stealer appears to be a rebranded or forked version of ZeroTrace Stealer, another malicious tool previously distributed by the same developer who has also promoted Raven Stealer.
Technical Capabilities and UAC Bypass Mechanisms
Anivia Stealer incorporates sophisticated technical features designed to evade detection and maximize data exfiltration.
The malware’s UAC bypass functionality allows it to escalate privileges automatically without triggering Windows security prompts, enabling execution with administrative rights while remaining undetected.
Built in C++17, the stealer operates across multiple Windows versions from Windows XP to Windows 11, requiring no additional dependencies for deployment.
The malware maintains encrypted communications with its command-and-control panel, protecting threat actor operations from network monitoring. An integrated auto-update capability ensures the malware remains current with the latest evasion techniques and feature enhancements.
The data theft capabilities target a comprehensive range of sensitive information, including passwords, authentication cookies, cryptocurrency wallets, authentication tokens, and Local Security Authority (LSA) credentials.
Anivia Stealer captures screenshots of victim systems, extracts WhatsApp message data, and collects detailed system information for reconnaissance.
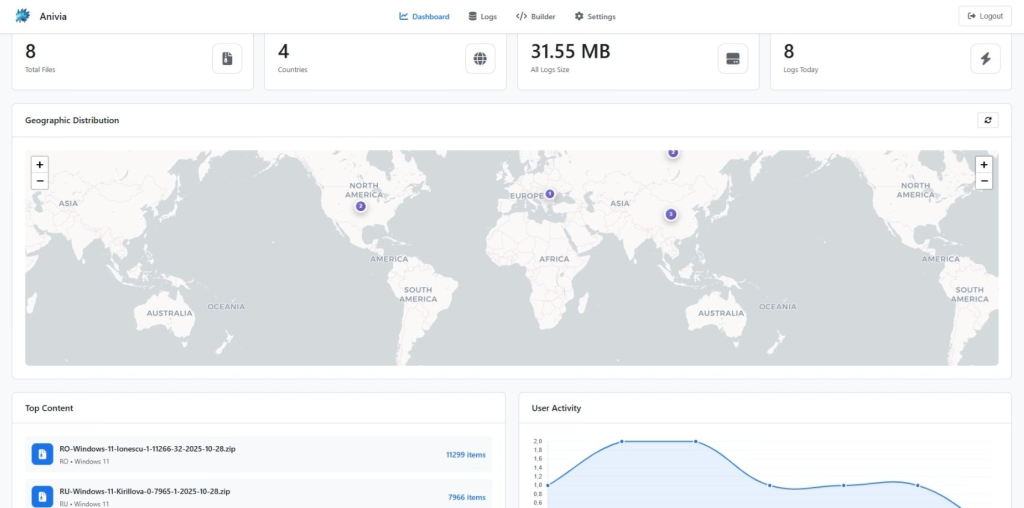
The web-based control panel provides threat actors with a live dashboard featuring geographic visualization via an interactive world map that displays the locations of infected systems.
Advanced filtering options and log parsing tools enable efficient management of stolen credentials and extracted data.
Underground Marketplace and Attribution Concerns
The subscription pricing structure reflects common malware-as-a-service (MaaS) business models prevalent in cybercriminal ecosystems. The tiered pricing includes one month for €120, two months for €220, three months for €320, and a permanent lifetime license for €680.
Security researchers analyzing GitHub commit histories and author metadata have identified evidence suggesting Anivia Stealer represents a rebrand of ZeroTrace Stealer by the same developer.
This pattern of rebranding existing malware tools allows threat actors to circumvent reputation-based blocking while maintaining established codebases.
While comprehensive malware analysis remains pending, the advertised features align with contemporary infostealer capabilities observed in similar threats.
Organizations should implement robust endpoint detection and response solutions, enforce the principle of least privilege, and maintain up-to-date security controls to defend against UAC bypass techniques and credential theft.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates