Security teams have observed a novel twist on the ClickFix social engineering technique, as threat actors lure victims seeking the AnyDesk remote-access tool into executing malicious code via a fake Cloudflare Turnstile and a Windows search protocol handler.
The attack ultimately delivers MetaStealer, a commodity infostealer that has been known for harvesting credentials and crypto wallets since 2022.
A Deceptive Verification Lure
Victims begin by clicking a link promising an AnyDesk installer, only to be redirected to anydeesk[.]ink, where a counterfeit “Secure Access Verification” page imitates Cloudflare Turnstile.
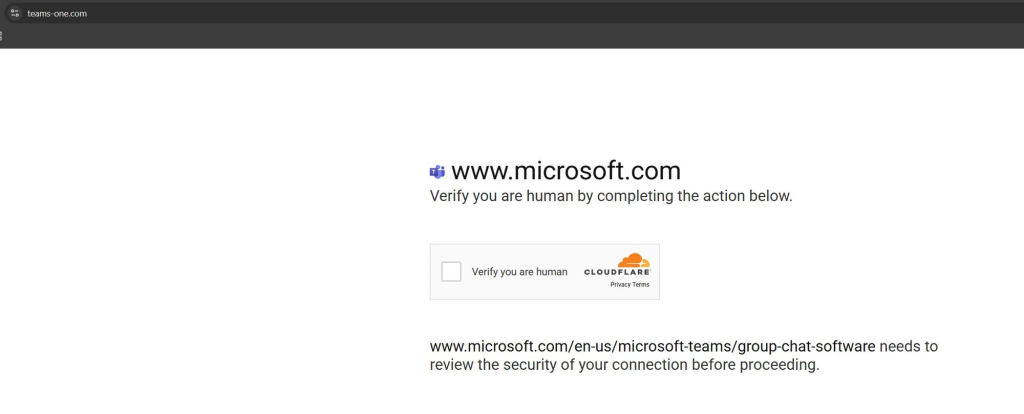
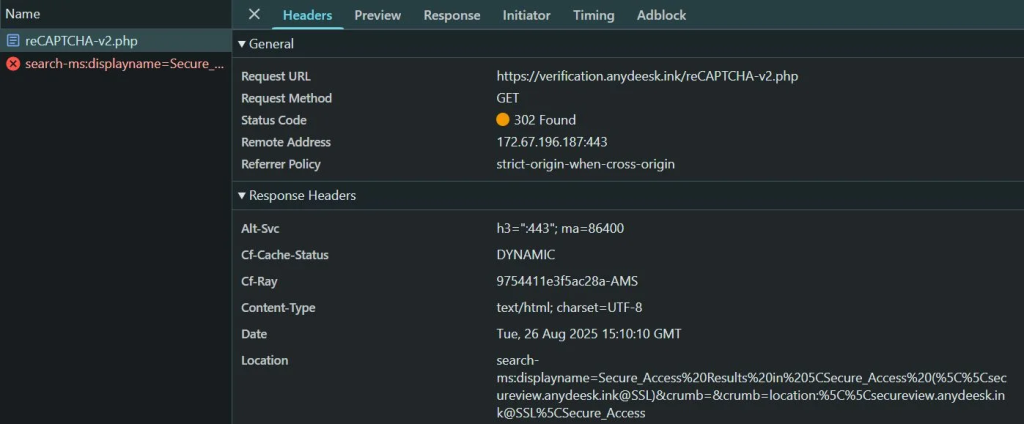
Beneath the obfuscated JavaScript, the page redirects the browser to a PHP script for verification. anydesk [.]ink/reCAPTCHA-v2.php.
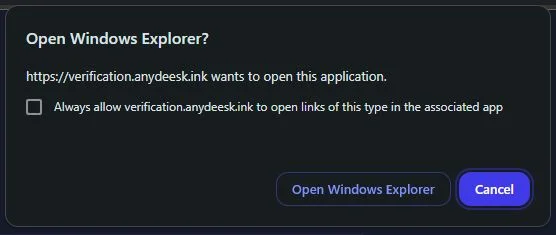
When users click the verification box, instead of triggering a standard Windows Run prompt (as in classic ClickFix), the page invokes the Windows File Explorer “Search” protocol (search-ms URI), steering victims toward malicious content hosted on an attacker-controlled SMB share.
Hijacking Windows Search Protocol
The search-ms URI includes a displayname parameter that references the share path. Once File Explorer launches, it accesses the remote share and displays a file disguised as “Readme AnyDesk.pdf.”
In reality, this is a Windows shortcut (LNK) whose payload launches two simultaneous processes. The first uses cmd.exe to download the legitimate AnyDesk installer via Microsoft Edge, likely to mitigate suspicion, while the second fetches a malicious MSI package from chat1.]store into the user’s temporary directory.
By embedding the victim’s %COMPUTERNAME% environment variable as a DNS subdomain, the attacker effortlessly exfiltrates the hostname without prior reconnaissance.
MetaStealer Unleashed
Upon execution via msiexec, the MSI reveals two critical components: CustomActionDLL, a DLL performing setup operations, and Binary.bz.WrappedSetupProgram, a CAB archive containing 1.js and ls26.exe. The 1.js script cleans up the infection chain, removing artifacts to evade detection.
The ls26.exe binary, protected with Private EXE Protector, serves as the MetaStealer dropper. Static analysis confirms behavior consistent with known MetaStealer samples, including credential harvesting, file exfiltration, and crypto wallet theft routines.
Mitigation and Awareness
This attack exemplifies how blending familiar verification UIs with native Windows features can bypass traditional endpoint controls.
Organizations should expand user training to recognize fraudulent CAPTCHA or Turnstile prompts that redirect to File Explorer, rather than solely focusing on disabling the Run dialog box.
Network controls should monitor search-ms URI invocations and unexpected SMB share connections to prevent unauthorized access.
Additionally, strict application whitelisting and endpoint monitoring for msiexec launches of unknown MSI packages can thwart similar infection chains before MetaStealer can execute its payload.
By understanding the evolution from ClickFix to FileFix and now to search-ms–based delivery, defenders can adapt policies and user education to block these increasingly sophisticated social-engineering attacks.
IOCs
| Indicator | Description |
| https[://]anydeesk[.]ink/download/anydesk[.]html | Domain with fake Cloudflare Turnstile |
| macawiwmaacckuow[.]xyz | MetaStealer C2 Domain |
| yeosyyyaewokgioa[.]xyz | MetaStealer C2 Domain |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates