The Stormshield CTI team identified two active servers closely resembling those documented by Check Point in their recent APT35 report.
Both servers host an identical minimalist HTML landing page, composed of four animated colored dots, and differ only in the file paths to their JavaScript and CSS assets.
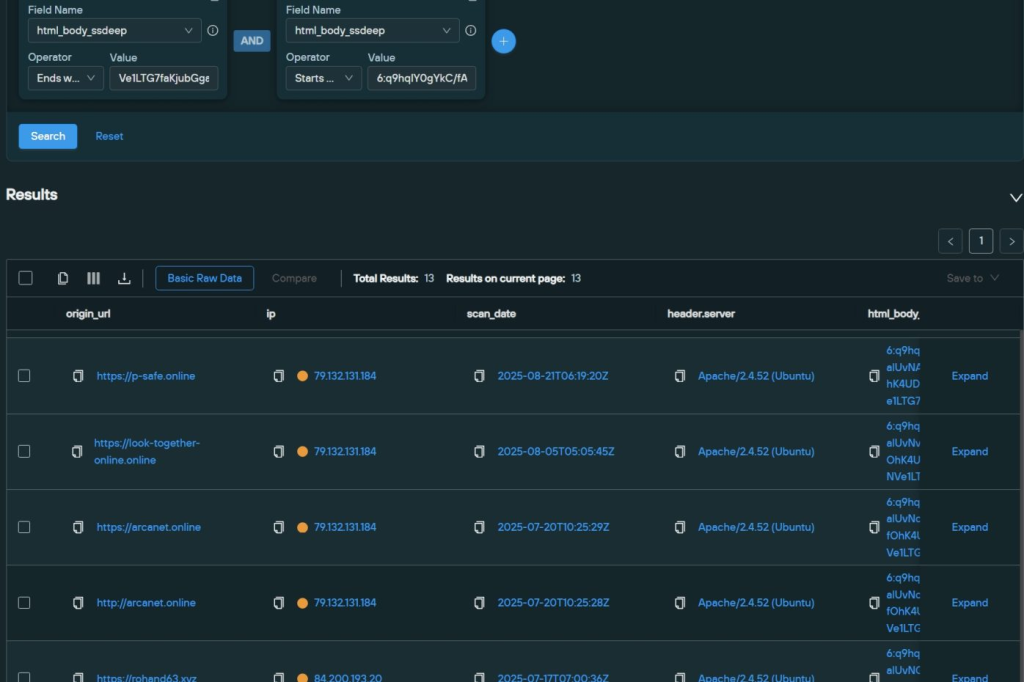
By leveraging the SilentPush platform’s html_body_ssdeep attribute, researchers generated a content-hash signature that matched eight known instances tied to 45.143.166.230 and 195.66.213.132, as well as two previously undocumented hosts: 84.200.193.20 and 79.132.131.184.
The novel fingerprints enabled the discovery of hidden infrastructure that had eluded traditional IP- or domain-based filtering, underscoring the value of SSDEEP–based detection in unearthing low-profile phishing hubs.
Phishing Infrastructure Analysis
A detailed examination of the server at 84.200.193.20, registered under AS214036 (Ultahost, Inc.), revealed a rapid churn of domains throughout July 2025, with each domain active for two to twelve days.

Only rohan63[.]xyz remains in active resolution, indicating that APT35 employs frequent domain rotation to thwart takedowns.
In contrast, the host at 79.132.131.184 (AS39378, SERVINGA) maintains continuity, resolving at least 49 “.online” domains since July 20, 2025, with the most recent registration, proof-video[.]online, appearing on September 20, 2025.
All domains adopt video-conferencing motifs such as meet. google [.]online a tactic consistent with documented APT35 TTPs since 2023.
By masquerading as legitimate Google Meet-style portals, the adversary effectively harvests credentials from government, military, and academic targets in Israel and beyond.
Tracking Techniques and Defensive Measures
Beyond domain discovery, investigators exploited VirusTotal’s URL search API to track query-parameter usage across phishing pages.
A search for “url:online/?invitation” returned multiple submissions containing unique invitation tokens, such as ?invitation-ter-nsbs-oerthose submitted from Sweden and Israel between mid-July and mid-September 2025.
These tracking parameters likely allowed the threat actors to correlate click-throughs with specific email campaigns or targeted recipients.
Concurrently, a wildcard subdomain query for viliam.* uncovered over 112 hosts, providing a reconnaissance shortcut for defenders.
To counter these techniques, security teams are advised to integrate SSDEEP–based hashing into email and web-filtering pipelines, inspect incoming URLs for the “?invitation-” pattern, and continuously monitor DNS registrations for the “viliam.” prefix.
Such layered detection strategies enable proactive identification and blocking of emerging APT35 phishing domains before credential compromise occurs.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates