Pakistan-linked threat group APT36, also known as Transparent Tribe, has significantly evolved its cyberattack playbook beyond traditional military targets to include critical Indian infrastructure sectors.
Security researchers have uncovered a sophisticated campaign that exploits .desktop files disguised as PDF documents to infiltrate Indian railways, oil and gas infrastructure, and government networks, marking a dangerous expansion of the group’s operational scope.
Advanced Infection Chains Using Desktop Files
APT36’s latest campaign employs two distinct attack variants, both utilizing .desktop files masquerading as legitimate PDF documents.
These files execute malicious scripts in the background while displaying decoy content to victims.
The first variant uses a single command and control server at 209.38.203.53, while the second employs redundant infrastructure with servers at 165.232.114.63 and 165.22.251.224 to ensure operational resilience.
The attack begins when victims open what appears to be a harmless PDF document. Behind the scenes, the .desktop file executes scripts that download malware payloads, establish persistence through cron jobs, and clean up traces of the infection.
The malicious files are given names like p7zip-full, tcl-8.7, emacs-bin, and crond-98 to blend in with legitimate system files.
Poseidon Backdoor Deployment
Following initial infection, APT36 deploys the Poseidon backdoor, built on the open-source Mythic command and control framework and written in Go.
This cross-platform tool enables long-term access, credential harvesting, and lateral movement within compromised networks.
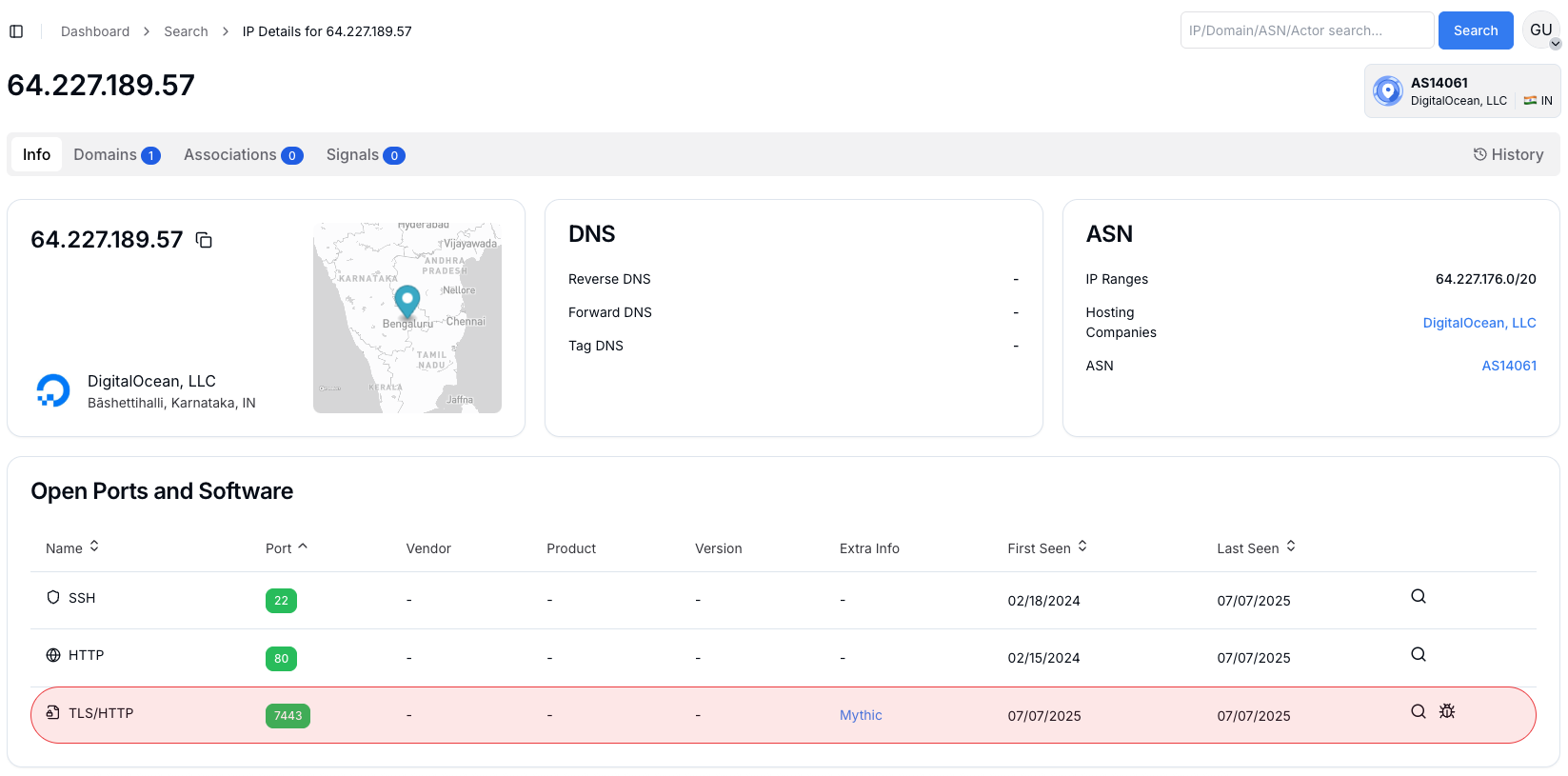
Security researchers identified command and control servers at 178.128.204.138 and 64.227.189.57, both hosted by DigitalOcean, with infrastructure spanning Germany and India.
The Poseidon backdoor’s modular design allows attackers to load functionality as needed, making it particularly dangerous for critical infrastructure environments.
Analysis confirmed that port 7443 is actively running Mythic C2 services, with one server located in Karnataka, India, suggesting the threat actors are strategically positioning infrastructure close to their targets.
Massive Phishing Infrastructure Exposed
Researchers discovered over 100 phishing domains in this campaign, many impersonating Indian government organizations and hosted by AlexHost.
The domains use familiar-looking subdomains combined with misleading top-level domains such as .report, .support, .digital, and .link. Examples include the Indian Army. nic.in/nomination-drdo-report, mod.gov.in/defence-personnel-support, and iaf.nic.in/ministry-of-defence-india.org.
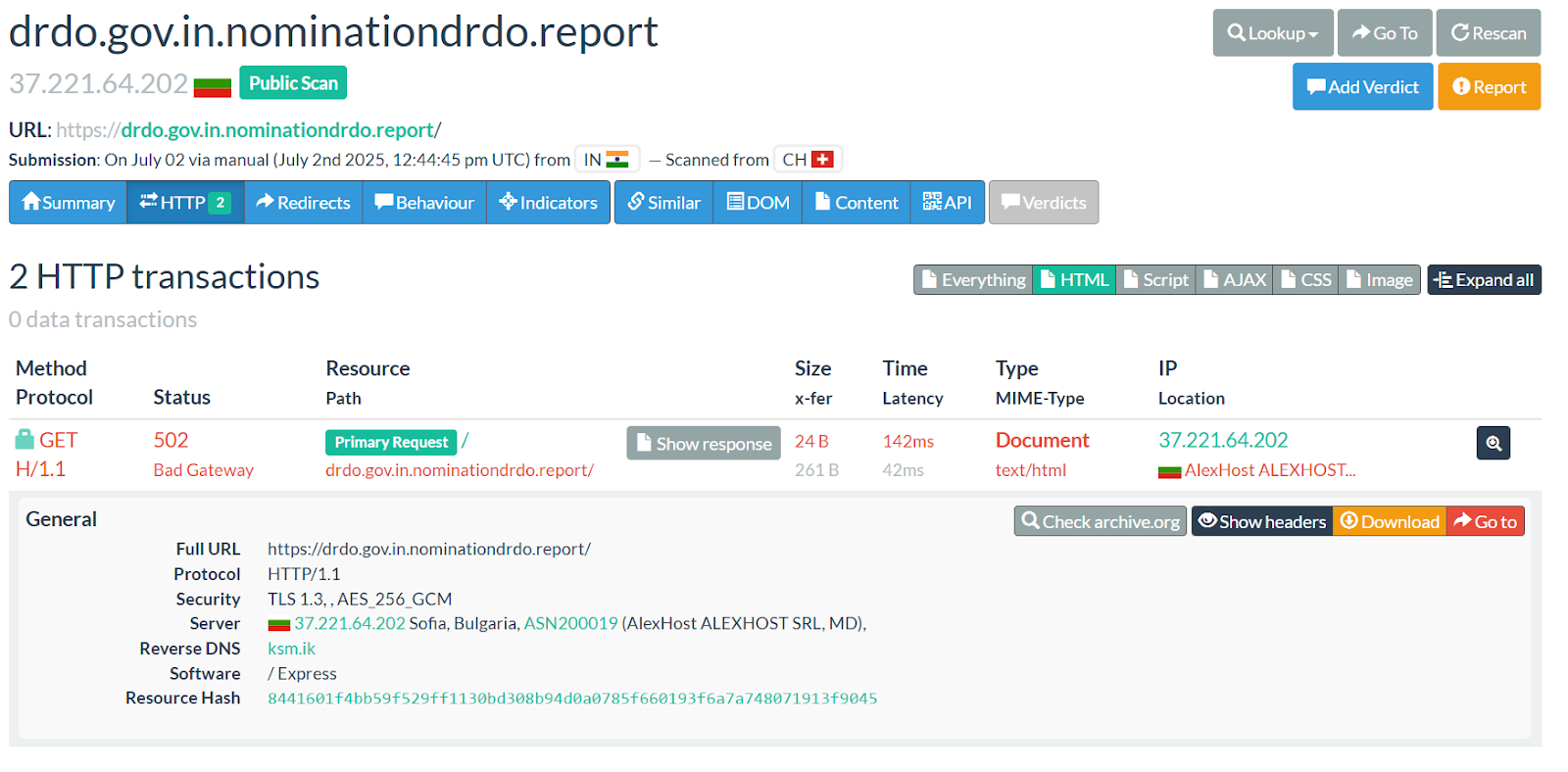
The phishing campaign first emerged through domains registered in early July 2025, with live infrastructure observed as of mid-July, indicating ongoing and active targeting.
The consistent use of domain formats, content templates, and hosting providers points to centralized control by APT36.
Security researchers have linked this infrastructure expansion to APT36’s broader strategy of targeting Indian critical sectors.
The group has previously demonstrated sophistication in credential harvesting operations. It continues to refine its techniques to avoid detection while maintaining persistent access to sensitive networks across multiple sectors of India’s national infrastructure.
Indicators of Compromises (IOCs):
| MD5 Hash | Description |
|---|---|
| e354cf4cc4177e019ad236f8b241ba3c | .desktop file used by APT36 for persistence and evasion. |
| 76e9ff3c325de4f2d52f9881422a88cb | Malicious .desktop file with scripts for system profiling. |
| 65167974b397493fce320005916a13e9 | APT36 launcher disguised as a document shortcut. |
| 6065407484f1e22e814dfa00bd1fae06 | APT36 desktop file with evasion techniques. |
| 5c71c683ff55530c73477e0ff47a1899 | Masquerading file executing payloads on Linux. |
| 8d46a7e4a800d15e31fb0aa86d4d7b7f | Phishing lure with backdoor and anti-analysis. |
| 589cf2077569b95178408f364a1aa721 | .desktop file used for initial compromise and evasion. |
| b3f57fe1a541c364a5989046ac2cb9c5 | Shortcut used by APT36 for Linux targeting and payload delivery. |
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates