Hackers are actively exploiting exposed ASP.NET machine keys to inject a sophisticated malicious module dubbed “HijackServer” into Internet Information Services (IIS), putting hundreds of web servers worldwide at risk of persistent compromise and remote code execution.
The rapidly expanding threat leverages long-known, but too often overlooked, configuration issues in Microsoft’s .NET framework to stage powerful attacks against organizations of all sizes.
Exploiting the Weak Link: Machine Key Exposure
Attackers begin by identifying ASP.NET applications with publicly disclosed or weak machine keys, secrets required to validate and decrypt viewstate data.
By either scraping these keys from abandoned code repositories and programming forums or exfiltrating them from platforms like SharePoint, hackers can manipulate ASP.NET viewstate, leading directly to arbitrary code execution on the underlying server.
Microsoft had warned in early 2025 that over 3,000 machine keys were already exposed, significantly increasing the pool of easy targets.
Once access is gained, threat actors use privilege-escalation techniques, such as EfsPotato and DeadPotato, to gain administrator-level control. The infection chain proceeds with the deployment of a remote access tool and, ultimately, the HijackServer IIS module.
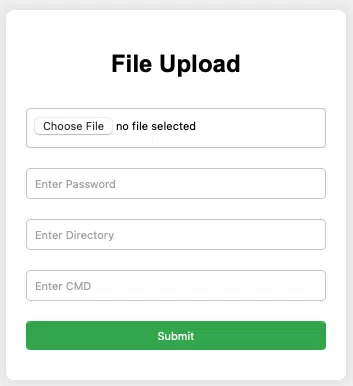
To evade detection, attackers execute noisy but effective log-clearing and use a rootkit signed with a repurposed, expired code-signing certificate. This rootkit hinders forensic analysis by hiding files, registry keys, and processes related to the intrusion.
Malicious Module Delivers Persistent Backdoor
HijackServer is engineered as a native IIS module (written in C and .NET), hooking into all HTTP request stages.
It functions both as a search engine optimization (SEO) scam tool that generates fake investment pages visible only to Googlebot and as a fully unauthenticated backdoor.
The module provides attackers with a stealthy, robust channel for remote command execution and file uploads, bypassing traditional authentication methods. Operators control the implant via crafted HTTP headers, further obfuscating their presence.
Config files and HTML templates for HijackServer are fetched from attacker-controlled staging domains, mainly registered with providers in Hong Kong and shielded by Cloudflare.
The infection kit includes automated scripts and a Chinese-language graphical deployment tool, suggesting the campaign has broad, potentially commoditized distribution among threat actors.
Researchers have now identified HijackServer variants for Apache (delivered via PHP) and .NET platforms, extending risk to a broader array of web servers.
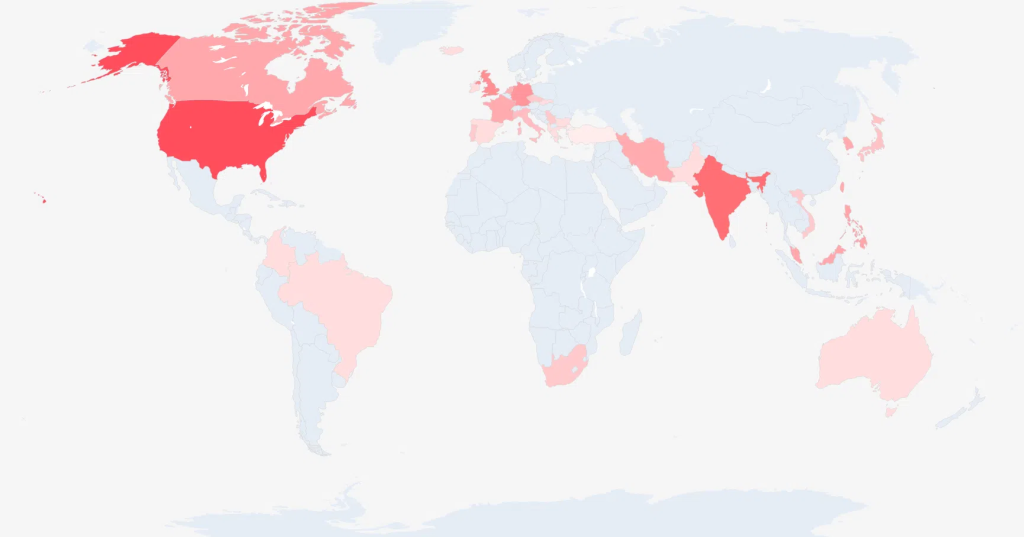
The scope of compromise is significant: as of September 2025, at least 171 distinct IIS server instances had the backdoor installed, affecting hundreds of domains globally, from online shops to government portals.
Administrators are urgently advised to rotate all ASP.NET machine keys and scrutinize their IIS environments for suspicious modules or rootkit artifacts, as even patched vulnerabilities leave organizations exposed if secrets have been leaked.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates