German hosting provider Aurologic GmbH has emerged as a critical nexus within the global infrastructure ecosystem supporting malicious activity, according to research from Recorded Future’s Insikt Group.
Operating from Tornado Datacenter GmbH & Co. KG in Langen, Germany, the company provides upstream transit and data center services to multiple high-risk hosting networks consistently ranked among the top sources of validated malicious infrastructure.
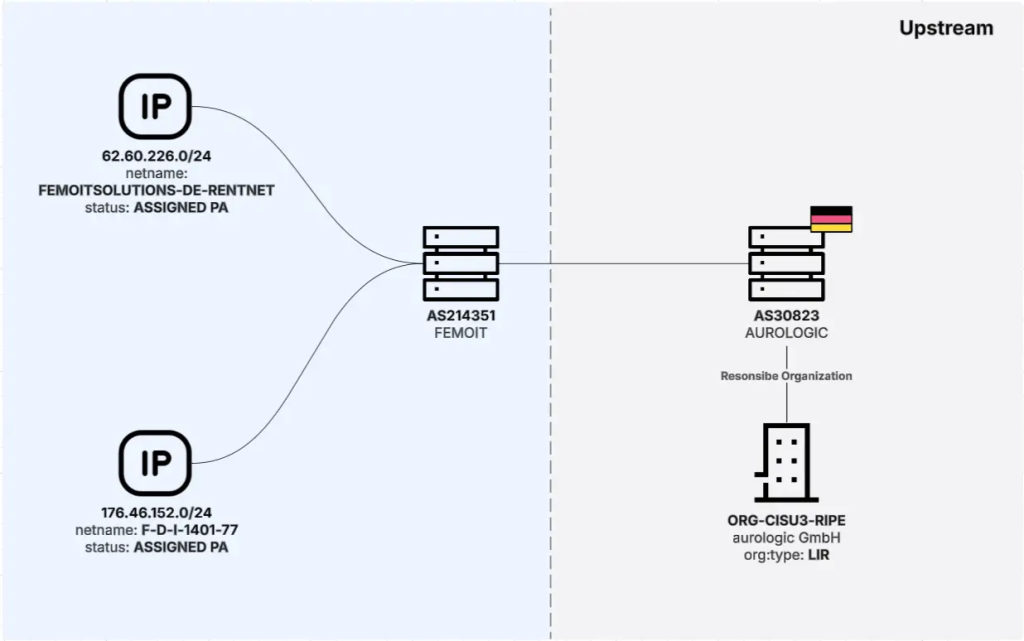
These downstream customers include several organizations designated as threat activity enablers (TAEs), such as Metaspinner Net GmbH, Femo IT Solutions Limited, Global-Data System IT Corporation (SWISSNETWORK02), Railnet LLC, and the recently sanctioned Aeza Group.
Founded in October 2023 following Combahton GmbH’s transition of its fastpipe[.]io network, Aurologic markets itself as a high-capacity European carrier offering dedicated servers, cloud hosting, data center colocation, and DDoS protection services.
However, despite its legitimate operational focus, the company has become a primary enabler for some of the most abusive networks operating globally.
Approximately 50% of Aeza International’s announced IP prefixes are routed exclusively through Aurologic, demonstrating the provider’s critical role in maintaining operational resilience for sanctioned infrastructure.
The Aeza Connection and Structural Challenges
Aeza Group, a Russian hosting provider, exemplifies the severity of Aurologic’s exposure. In July 2025, the US Department of the Treasury’s Office of Foreign Assets Control (OFAC) and the UK National Crime Agency jointly sanctioned Aeza and its affiliated entities as a “bulletproof hosting services provider.”
The designations cited Aeza’s involvement in supporting BianLian ransomware, Lumma and Meduza infostealers, and RedLine Stealer operations.
Despite these sanctions, routing evidence confirmed that Aurologic remained a primary upstream provider to Aeza International Ltd (AS210644), highlighting the company’s continued stance of “legal compliance over risk avoidance.”
Beyond Aeza, Aurologic’s infrastructure supports multiple additional TAEs with substantial malicious footprints.
Femo IT Solutions Limited, announcing only two /24 prefixes, has consistently displayed one of the highest concentrations of validated malicious infrastructure relative to its size, hosting command-and-control infrastructure for Cobalt Strike, DcRat, and multiple stealer families.
Global-Data System IT Corporation’s eleven active prefixes route exclusively through Aurologic with zero diversification, making the German provider the critical single point of failure for the network’s global availability.
Defining the Accountability Gap
Insikt Group assessed that Aurologic’s case exemplifies broader structural challenges surrounding accountability within the hosting ecosystem.
Upstream providers occupy a pivotal position within the internet infrastructure hierarchy, yet continue to defer responsibility for downstream activity, intervening only when legally compelled.
During a June 2024 meeting with German investigative organization CORRECTIV, Aurologic CEO Joseph Hofmann stated he would only take action upon formal law enforcement contact, describing his operational position as waiting for “law enforcement correspondence” rather than proactively addressing abuse patterns.
The company’s Terms of Service explicitly invoke the EU’s Digital Services Act to disclaim liability for customer-transmitted content, provided Aurologic claims to be unaware of any illicit use.
This reactive compliance framework, while potentially legally defensible under German and EU law, has enabled sustained malicious infrastructure operations worldwide, establishing Aurologic as a critical node in organized cybercrime and disinformation campaigns.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates