Attackers have long exploited identity and access management misconfigurations in AWS, but a new open-source tool called AWSDoor is raising the stakes by automating sophisticated persistence techniques that blend in with legitimate administrative activity.
By modifying IAM roles, injecting rogue policies, and leveraging native services like Lambda and EC2, adversaries can now maintain long-term footholds in cloud environments without dropping malicious binaries.
Security teams must rapidly adapt their detection and response strategies to combat these emerging threats.
IAM-Based Stealth Persistence
AWSDoor’s initial persistence module focuses on IAM identities, enabling adversaries to create or manipulate access keys and trust policies with minimal effort.
The tool can generate new AccessKey credentials on privileged users—even bypassing multi-factor authentication requirements—while logging suggests such keys are neither unusual nor noisy in many environments.
AWSDoor also automates trust policy backdooring: attackers can inject their own AWS account or role into a target role’s trust document, granting external assume-role privileges that evade typical permission reviews.
A third IAM tactic uses the NotAction operator to craft policies that effectively grant full administrative privileges under the guise of a narrowly scoped permission, hiding in plain sight among benign configurations.
Beyond IAM, AWSDoor offers modules that exploit AWS compute services for persistence. An “AdminLambda” feature can deploy a new Lambda function or layer containing malicious code concealed within standard libraries.
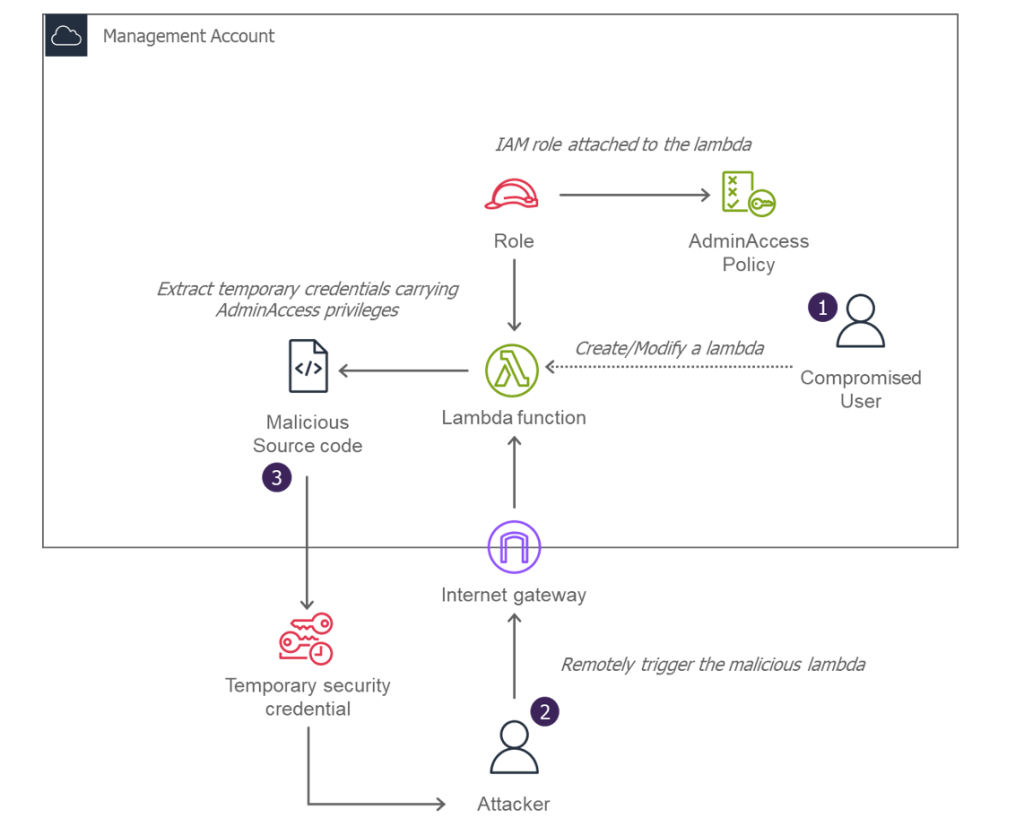
Because AWS consoles display only that a layer exists—without revealing its contents—poisoned dependencies can go undetected during routine reviews.
Attackers may also attach over-privileged roles to existing functions or expose them via API Gateway or Function URLs, creating remote code execution endpoints.
On EC2, AWSDoor can orchestrate reverse SOCKS proxy tunnels through the AWS Systems Manager agent, allowing outbound pivoting without opening inbound ports.
By automating SSH key deployment and proxy setup, adversaries gain network access through legitimate service channels.
Logging Impairment and Silent Exfiltration
AWSDoor includes capabilities to undermine AWS monitoring at scale.
Its CloudTrailStop module disables event logging on specified trails or reconfigures event selectors to suppress management and data events entirely.
Even organization-level trails remain immune to this tactic, making it difficult to track attacker activity after initial compromise.
For data exfiltration, AWSDoor can snapshot and share EBS volumes with external accounts or abuse S3 lifecycle policies for “shadow deletes” that silently expire bucket contents without generating delete object events.
Finally, the tool can detach a compromised account from its AWS Organization, stripping away centralized controls and visibility while leaving resources intact for undetected data theft.
Organizations must extend beyond basic IAM auditing to detect these advanced persistence techniques.
Continuous monitoring of IAM policy changes, trust policy updates, and unusual layer attachments is essential.
Implementing Cloud Security Posture Management (CSPM) to flag NotAction policies, enforcing strict Service Control Policies against account detachment, and integrating Cloud-native EDR solutions can help defenders identify and disrupt AWSDoor’s automated backdoors before they become entrenched.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates