A critical vulnerability in Microsoft Azure’s API Connection architecture that enabled complete cross-tenant compromise of cloud resources worldwide.
The bug, which Microsoft patched within a week of disclosure, earned Gulbrandsrud a $40,000 bounty and a presentation slot at Black Hat 2025.
The vulnerability exploited Azure’s shared API Management (APIM) infrastructure to access any connected backend service, including Key Vaults, databases, and third-party platforms like Salesforce and Jira across different Azure tenants.
The vulnerability stems from Azure’s architectural design where all API Connections utilize a globally shared APIM instance.
This shared infrastructure processes authentication token exchanges between user applications and backend services, with Logic Apps and other Azure services querying the APIM to access connected resources.
While Microsoft’s documentation shows that only authorized applications should perform these token exchanges, Gulbrandsrud discovered that the shared nature of this infrastructure created an exploitable attack vector.
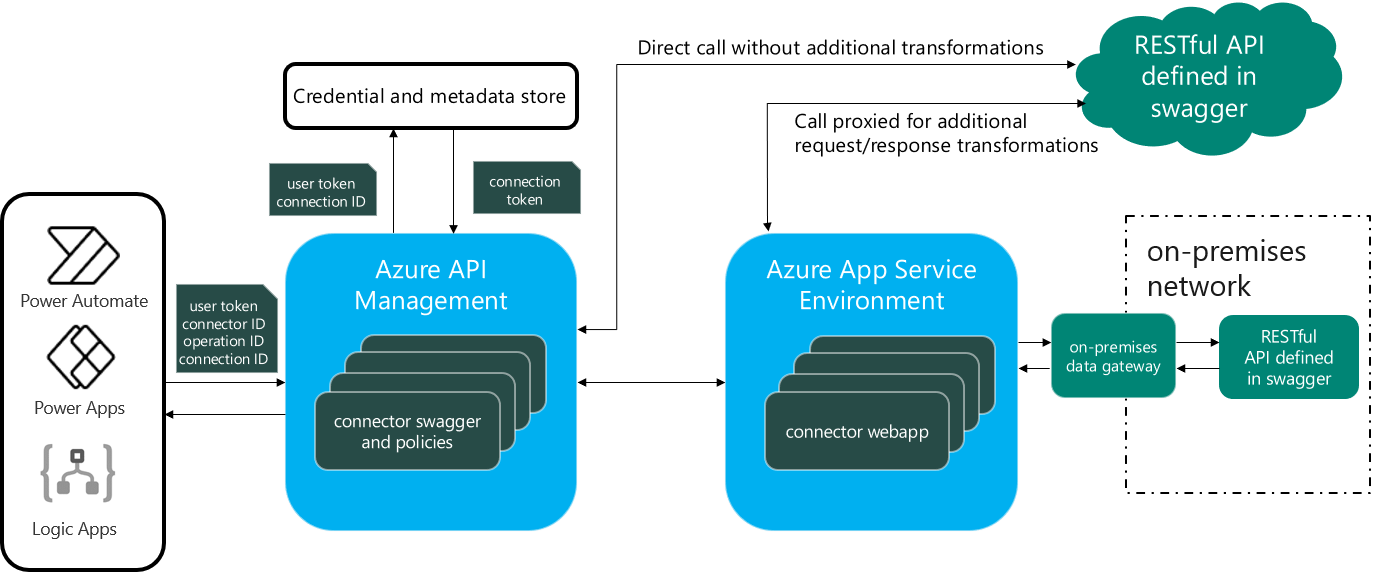
The critical flaw involved an undocumented DynamicInvoke endpoint that allows Azure Resource Manager (ARM) to call arbitrary actions on API Connections.
This endpoint accepts POST requests with custom path and method parameters, enabling attackers to specify which backend service endpoints to target.
Since ARM uses super-privileged tokens when communicating with the APIM instance, successful exploitation grants administrative access to any connected service globally.
Azure API Connection Vulnerability
Gulbrandsrud’s exploitation technique leveraged path traversal through custom Logic App connectors. By creating a custom connector with string path parameters, he could inject malicious paths that would traverse the directory structure to access other tenants’ connections.
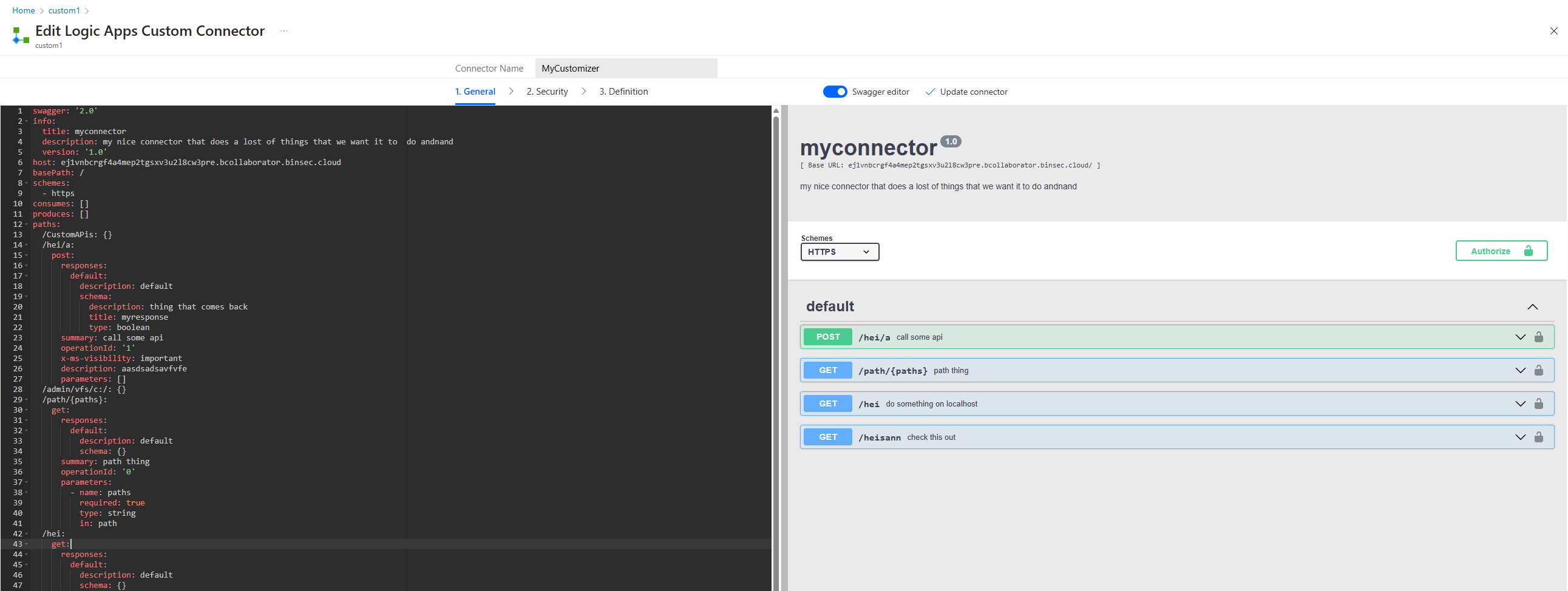
When ARM processed a DynamicInvoke request with a crafted path like ../../../../[VictimConnectorType]/[VictimConnectionID]/[action], the system would normalize the path and grant access to the target connection.
The attack demonstrated complete compromise of Azure Key Vaults, allowing unauthorized access to stored secrets across tenant boundaries.
The researcher showed how the vulnerability could extract sensitive information from any backend service connected through API Connections, effectively bypassing all Role-Based Access Control (RBAC) restrictions.
The only requirement was knowing the target connection’s identifier, though these values frequently appear in CI/CD logs and public forums.
Rapid Response and Industry Impact
Microsoft’s security team confirmed the vulnerability within three days of disclosure on April 7, 2025, and implemented mitigations within a week.
While Gulbrandsrud noted that obtaining specific connection IDs remained challenging, the theoretical impact encompassed any organization using Azure API Connections for backend integration.
The company classified this as a critical security issue due to its potential for widespread cross-tenant data breaches affecting enterprise customers worldwide.
The vulnerability particularly threatened organizations storing sensitive credentials and secrets in Azure Key Vaults, which serve as central repositories for encryption keys, passwords, and certificates.
The discovery highlights the security risks inherent in shared cloud infrastructure architectures, where multi-tenant systems can create unexpected attack vectors.
The $40,000 bounty reflects the severity of a vulnerability that could have enabled attackers to compromise multiple organizations’ cloud resources through a single Azure tenant compromise.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.