In a significant blow to the DeFi ecosystem, Check Point Research revealed that Balancer V2’s ComposableStablePool contracts were exploited on November 3, 2025, resulting in the theft of $128.64 million across six blockchain networks in less than half an hour.
The attackers weaponized a subtle arithmetic precision flaw within Balancer’s pool invariant logic, transforming a rounding error into a catastrophic exploit chain that bypassed standard security mechanisms.
Exploit Origin and Mechanism
The breach was first detected by Check Point’s blockchain monitoring systems, which flagged abnormal withdrawals from the Ethereum mainnet’s Balancer Vault contract.
The root cause lay in an arithmetic precision loss vulnerability in the _upscaleArray function, which scales token balances during invariant computation. When balances were driven to the microscopic 8–9 wei range, Solidity’s integer division logic caused rounding discrepancies that could reach ten percent per operation.
By embedding this rounding behavior into a 65‑step batchSwap sequence, the attacker amplified minor precision losses into a full‑scale distortion of the pool invariant (D value).
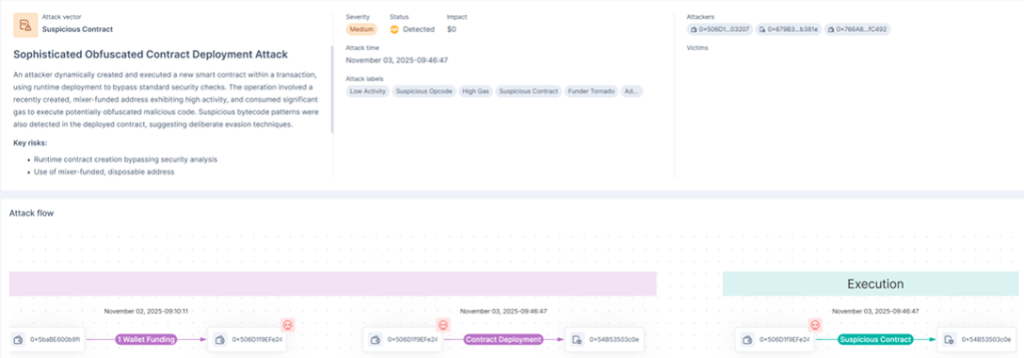
Since the Balancer Pool Token (BPT) price derives directly from this invariant, artificially reducing D allowed them to suppress BPT prices and execute arbitrage swaps that extracted vast liquidity from affected pools.
The three‑phase process repeated atomically within the same batchSwap call:
- Adjusting token balances close to the rounding boundary to set up a precision vulnerability.
- Triggering precision loss through micro‑swaps that miscalculated invariants.
- Exploiting price suppression to mint undervalued BPT and redeem them for full‑value assets.
Contract Forensics and Withdrawal Trail
On‑chain analysis linked the exploitation to contract 0x54B53503c0e2173Df29f8da735fBd45Ee8aBa30d, deployed by address 0x506D1f9EFe24f0d47853aDca907EB8d89AE03207.
The entire heist unfolded during constructor execution, which automatically performed 65 swaps targeting specific Balancer pools. Internal balance updates showed the attacker netting 6,586 WETH, 6,851 osETH, and 4,259 wstETH.
Instead of transferring tokens directly, the attacker leveraged Balancer’s Internal Balance feature, accumulating stolen assets inside the Vault’s accounting layer.
A later function call, identified by selector 0x8a4f75d6, invoked manageUserBalance to withdraw these amounts to the recipient address 0xAa760D53541d8390074c61DEFeaba314675b8e3f.
Check Point emphasized that despite multiple audits, the bug survived because traditional analysis focuses on single‑transaction correctness rather than cumulative arithmetic drift.
The event underscores the importance of adversarial modeling, continuous invariant monitoring, and precision‑sensitive simulation within DeFi math libraries. Balancer’s loss highlights a growing trend mathematical corner cases are now a preferred weapon for well‑funded on‑chain attackers.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates