Threat hunters from CyberProof and other security research teams have exposed a wave of attacks spreading through WhatsApp that reveal close operational and technical connections between the Maverick and Coyote banking trojans.
These ongoing campaigns primarily target Brazilian users and mimic legitimate communication to trick victims into downloading malicious ZIP archives from web.whatsapp.com.
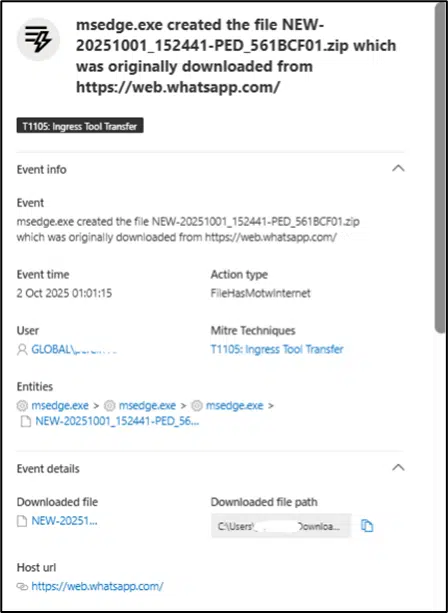
One such file, named NEW-20251001_152441-PED_561BCF01.zip, contained a disguised shortcut that appeared as a PDF but actually executed a heavily obfuscated command sequence.
Once opened, the LNK file launched cmd.exe, which constructed an encoded PowerShell script through multiple nested loops and Base64 fragments. The decoded fragments reconstructed a downloader command that linked back to zapgrande[.]com, executing additional payloads directly in memory.
This pattern represents a growing trend toward fileless malware designed to bypass endpoint detection mechanisms and conventional antivirus checks.
Multi-Stage Payloads and Advanced Persistence Mechanisms
Further analysis revealed that once the downloader script was executed, it fetched a secondary payload written in .NET.
The loader performed anti-analysis checks to avoid sandbox environments or debugging tools before contacting two additional command-and-control endpoints on zapgrande[.]com.
These servers appear to deliver distinct modules responsible for data theft, remote communication, and hijacking WhatsApp Web sessions.
Persistence within infected systems is achieved by deploying batch files in the Startup directory following the HealthApp-{GUID}.bat naming scheme, ensuring reinfection after system reboot.
The script connects to sorvetenopote[.]com using a startup path parameter, allowing the attacker to maintain communication even if other components fail. In several cases, this stage also included routines to turn off Microsoft Defender and User Account Control settings to minimize detection.
The infection chain mirrors earlier Coyote activity, which employed similar persistence and communication mechanisms, including encrypted URLs and obfuscated PowerShell payloads.
Code Similarities Point to Common Origins
A comparative analysis of Maverick and Coyote reveals extensive technical overlap. Both rely on .NET frameworks, use multi-layer PowerShell loaders, and employ AES and GZIP encryption to decode lists of targeted financial institutions.
The targeted banks include several major Brazilian entities, such as Itaú, Bradesco, Caixa, and Banco do Brasil. Both malware families are programmed to monitor browser activity for specific URLs associated with online banking, then trigger credential theft modules when a match is detected.
The Coyote Trojan, first identified in 2024, focused on corporate and financial sectors, whereas Maverick extends these attacks to include hotels and trading firms. Researchers believe these similarities indicate shared development resources or active code reuse between the operators.
The current campaigns demonstrate growing sophistication through improved evasion, wider propagation, and potential use of AI-enhanced code mutation to stay ahead of detection.
Experts warn that continued tracking and behavioral monitoring remain critical to defending Brazilian institutions against these evolving threats.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates