A large-scale malware campaign has emerged in Brazil, spreading a new fileless banking Trojan named Maverick through WhatsApp.
The attack leverages malicious LNK files sent via ZIP archives, evading messaging platform restrictions to deliver a highly modular payload capable of complete system compromise.
Researchers identified significant code similarities with the previously known Coyote Trojan, though the new strain exhibits distinct infrastructure and capabilities, including artificial intelligence-assisted code generation.
Fileless Multi-Stage Infection Chain
The infection begins when a victim receives a ZIP file on WhatsApp containing a malicious .LNK shortcut disguised as a legitimate document or bank communication.
Once opened, the shortcut triggers a PowerShell command that downloads additional payloads from a command-and-control (C2) server. This communication channel uses strict verification, including “User-Agent” validation, ensuring that only malware can access subsequent payloads.
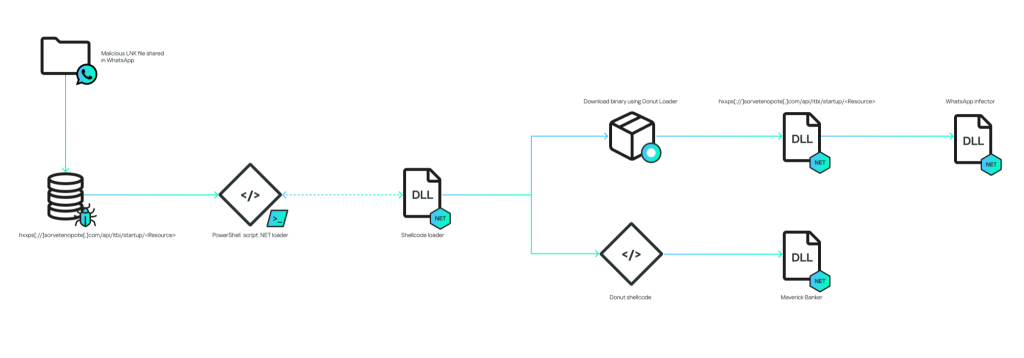
Each stage executes exclusively in memory via encrypted .NET assemblies and Donut-based shellcode loaders. The first .NET loader downloads two encrypted shellcodes using an HMAC256-based API key derived from the string “MaverickZapBot2025SecretKey12345.”
Decryption relies on XOR routines where keys are embedded in the file’s tail section. These loaders eventually deploy two core components: a WhatsApp infector and the Maverick Banker module.
The WhatsApp infector utilizes the open-source WPPConnect project with Selenium automation to hijack the victim’s WhatsApp Web session.
It sends spam messages containing new malicious ZIP files to stored contacts, enabling rapid worm-like propagation. This unique self-spreading method allows Maverick to amplify its footprint through social connections rather than traditional phishing channels.
Full Control and Banking Credential Theft
The Maverick Banker payload executes from memory, registers persistence scripts in the Windows startup folder, and then monitors the victim’s browsers, including Chrome, Edge, Firefox, and Brave.
It targets 26 Brazilian banking portals, six crypto exchanges, and one payment service. Banking site detection triggers an AES‑256 decryptor that loads a .NET agent designed for credential theft and remote desktop control.
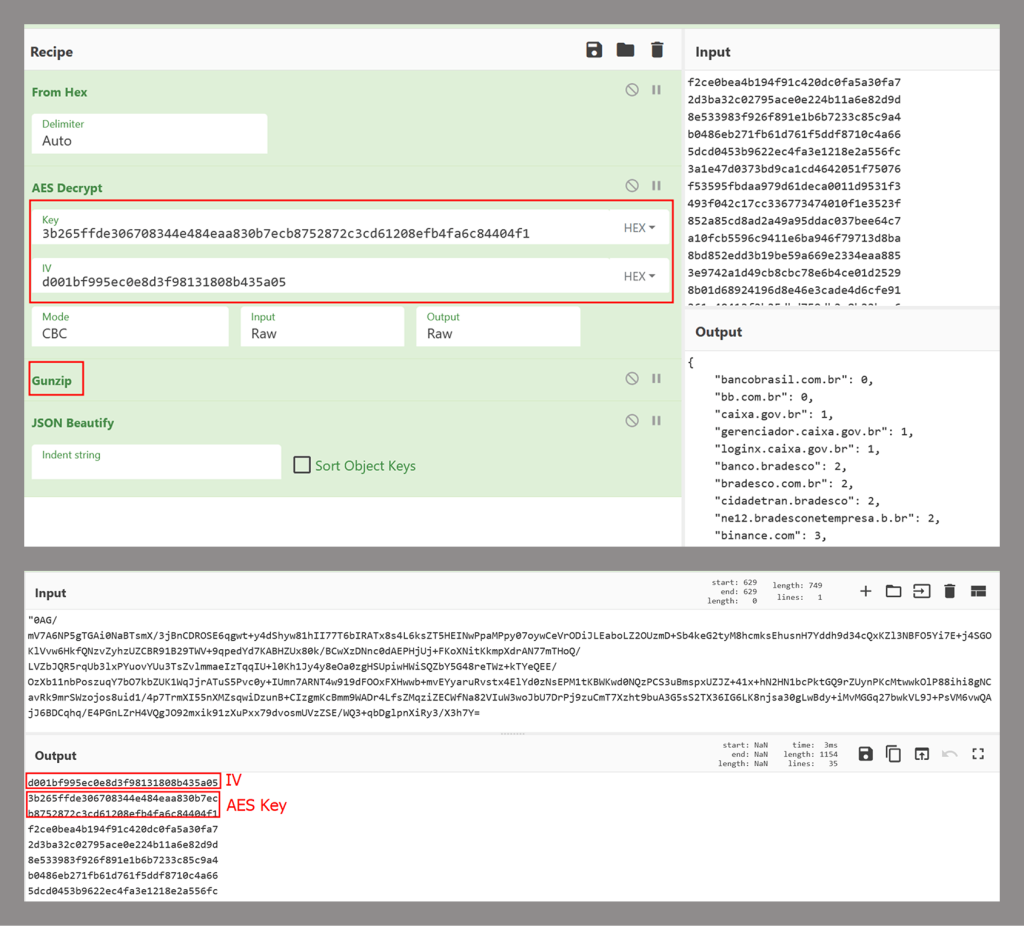
The final component, Maverick Agent, connects to its remote C2 server—casadecampoamazonas.com over SSL using an encrypted X.509 certificate.
After authenticating with the password “101593a51d9c40fc8ec162d67504e221”, it can execute commands such as taking screenshots, logging keystrokes, emulating keyboard and mouse input, locking the victim’s screen, and displaying phishing overlays of banking pages.
Security analysts have blocked over 62,000 infection attempts in the first 10 days of October. The campaign, confined to Brazilian users, indicates localized targeting through language, locale, and timezone verification.
The Maverick Trojan demonstrates a formidable evolution in regional banking malware, combining AI-assisted code, fileless persistence, and instant messaging exploitation for complete remote control.
IoCs
| Dominio | IP | ASN |
| casadecampoamazonas[.]com | 181.41.201.184 | 212238 |
| sorvetenopote[.]com | 77.111.101.169 | 396356 |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates