Cloud providers have long depended on hardware-based memory encryption to safeguard sensitive data, including passwords, financial records, and personal files, from both external hackers and curious insiders.
Leading technologies such as Intel SGX (Software Guard Extensions) and AMD SEV-SNP (Secure Encrypted Virtualization with Secure Nested Paging) aim to ensure that encrypted data remains protected even if a cloud host or administrator is compromised.
However, a newly disclosed hardware exploit called Battering RAM demonstrates that these critical defenses can be neutralized using a tiny, low-cost add-on board priced at under $50.
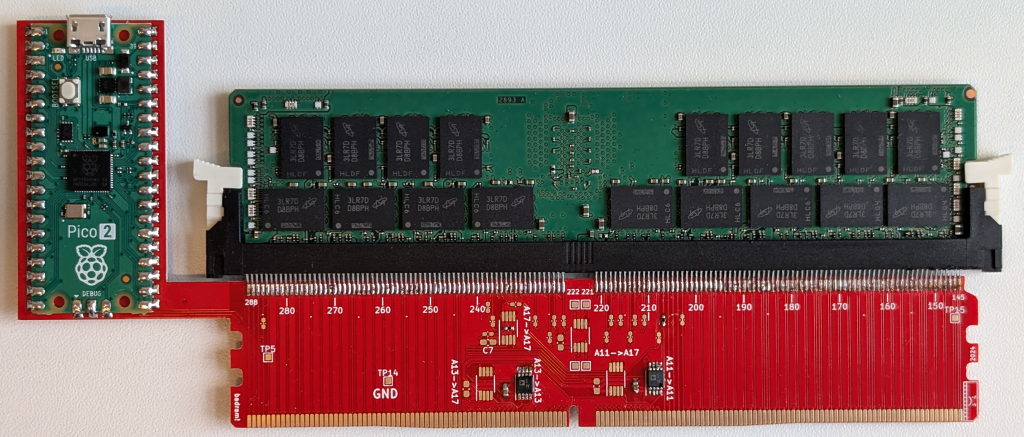
The device can then perform a ciphertext capture, reading encrypted data destined for secure enclaves or virtual machines.
How the Attack Works
1. Stealthy Initialization: During system startup, the interposer operates invisibly. It does not interfere with the boot process, allowing the firmware to verify memory encryption keys and complete all setup routines without detection.
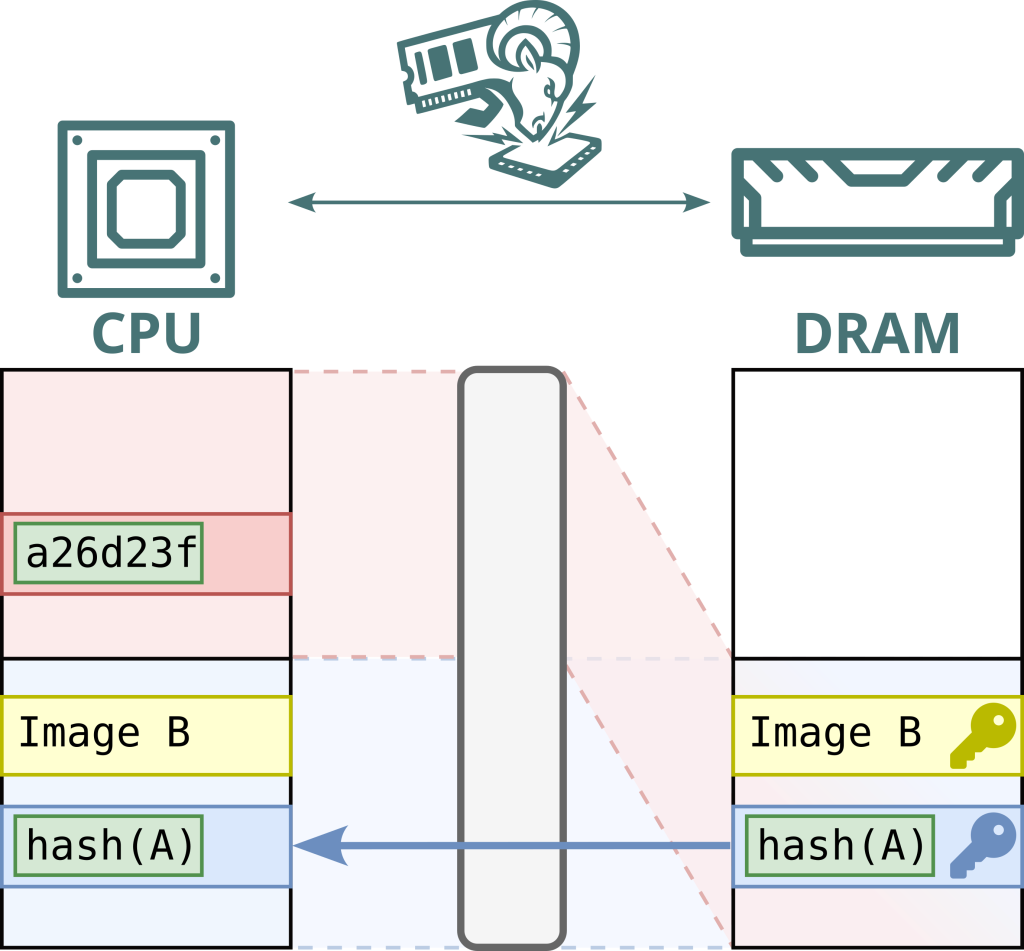
2. Activating Malicious Mode: Once the operating system is running, the attacker engages a hidden hardware switch. This transforms the interposer’s behavior: it begins rewriting address metadata so that pages designated as encrypted—belonging to secure enclaves or virtual machines—are transparently redirected to attacker-controlled memory buffers.
3. Capturing Encrypted Data: With the address metadata altered, any read operations on the aliased buffer yield encrypted ciphertext that originally belonged to the protected environment. The attacker harvests this encrypted data for later use.
4. Executing a Replay Attack: Next, the attacker reconfigures the interposer to map the victim’s physical memory address to their own enclave. By replaying the previously captured ciphertext into this location, the processor is tricked into decrypting and executing it within the attacker’s enclave context.
5. Exposing Plaintext Secrets: As the processor decrypts the replayed data, sensitive plaintext—intended to remain confidential—becomes accessible inside the attacker’s enclave. This grants the attacker full read and write privileges to memory regions safeguarded by Intel SGX or AMD SEV-SNP.
Traditionally, commercial memory interposers used by chip manufacturers for testing cost over $100,000. By contrast, the Battering RAM setup uses off-the-shelf analog switches and a four-layer PCB, all manufacturable for under $50.
The researchers have published full schematics and design files, raising concerns that malicious actors could rapidly adopt the technique.
Intel and AMD have acknowledged the findings, emphasizing that fully mitigating Battering RAM requires fundamental redesigns of memory encryption protocols.
Potential hardware mitigations include adding cryptographic integrity checks on memory metadata, continuously verifying memory mapping throughout system runtime, and incorporating tamper-evident mechanisms that detect unauthorized metadata changes.
Until such enhancements appear in future processor generations, cloud customers and service providers are urged to incorporate physical memory attack scenarios into their threat models and to explore complementary safeguards such as multi-party memory encryption and real-time hardware attestation to protect critical workloads.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates