The Beast ransomware group, which emerged as a Ransomware-as-a-Service (RaaS) platform in February 2025 and evolved from the Monster ransomware strain, continues to expand its operations across global enterprises.
Operating through a sophisticated affiliate model with a Tor-based data leak site launched in July 2025, the threat actors have publicly disclosed attacks against 16 victim organizations spanning the United States, Europe, Asia, and Latin America.
The group targets diverse industries, including manufacturing, construction, healthcare, business services, and education, and assigns each victim to separate negotiation channels managed by different partners.
Multi-Vector Attack Distribution Strategy
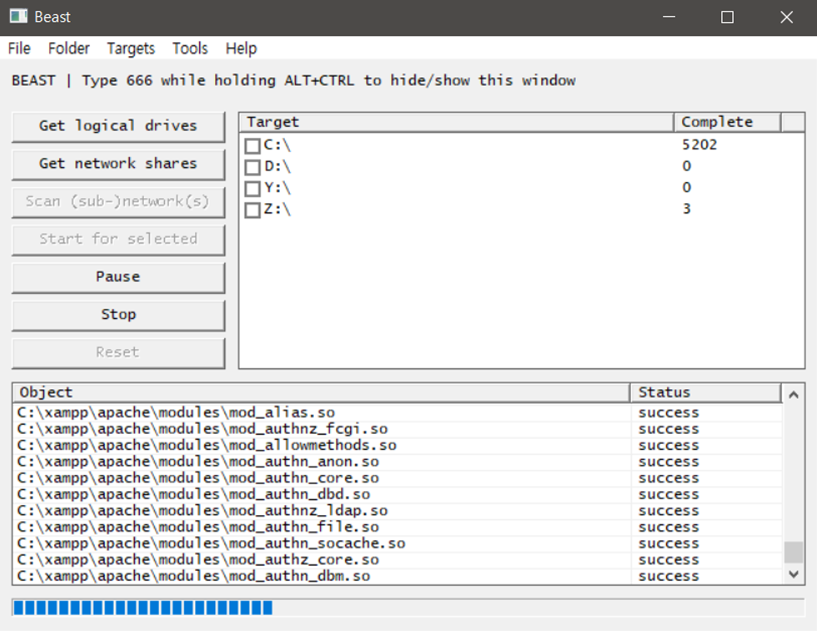
The primary distribution vector leverages compromised systems to scan for active Server Message Block (SMB) ports within target networks. Once identified, Beast attempts lateral movement by propagating to accessible shared folders across the network infrastructure.
This approach proves particularly effective in enterprise environments with interconnected systems and inadequate network segmentation.
Complementing this strategy, threat actors deploy phishing campaigns disguised as copyright infringement warnings or fraudulent job applications, often bundled with the Vidar information stealer to harvest credentials and sensitive data before deploying ransomware.
Advanced Encryption and Geographic Targeting
Beast’s technical implementation demonstrates sophisticated engineering designed to maximize encryption success and prevent data recovery.
Upon execution, the ransomware filters target systems using the GetLocaleInfo and GetSystemDefaultUILanguage APIs, deliberately excluding former Soviet Union member states and regions under Russian political influence, a pattern indicating operational constraints or developer origin.
This geographic targeting reduces execution across Commonwealth of Independent States territories while focusing on higher-value Western targets.
The malware uses ChaCha20 symmetric encryption for file encryption, with decryption keys stored exclusively on the attacker’s servers.
Infected files are named {OriginalFileName}.{GUID-like-string}.{Extension}, where the GUID is 18 bytes derived from SHA-512 hashing of system information and hardcoded values.
Each encrypted file includes 0xA0 bytes of metadata containing original file sizes, encryption keys, and verification information, making encrypted files distinctly larger than originals and preventing recovery through standard means.
System Hardening and Persistence Mechanisms
Beast performs comprehensive system hardening to maximize damage before encryption commences.
The ransomware terminates 50+ critical processes, including SQL Server instances, Oracle databases, backup utilities, antivirus products, and collaboration platforms. It simultaneously disables Windows Shadow Copy through WMI queries, eliminating native recovery mechanisms.
Additionally, the malware maintains persistence through self-replication to %ALLUSERPROFILE% directories and by registering the Run key, ensuring the infection survives system restarts.
Organizations facing Beast attacks confront virtually impossible decryption scenarios unless encryption algorithms are compromised or key management systems fail.
Security practitioners should prioritize preventive measures, including vulnerability assessments, robust backup isolation, strict external access controls, network segmentation for critical assets, and rapid incident response capabilities.
Early detection systems and threat intelligence monitoring prove essential for identifying Beast campaigns before extensive lateral movement occurs within enterprise environments.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates